What Is TLS 1.2, and Why Should You (Still) Care?
Gigamon Products GigaSMART® SSL/TLS Decryption Apps | Gigamon Live Demo | Gigamon Test Drive
The internet is the most ambitious communication and data transference technology ever created. But with those advancements come several challenges, and as we improve our ability to share large amounts of information between computers, servers, and other digital devices, the risk of that data falling into unauthorized hands increases significantly.
To prevent eavesdroppers, hackers, and other cybercriminals from accessing sensitive data as it moves through the internet, various cryptographic protocols have been introduced. The most famous of these are Secure Socket Layers (SSL) and Transport Layer Security (TLS).
SSL has long been defunct — replaced by TLS and its subsequent versions — TLS 1.0, TLS 1.1, and TLS 1.2. And with TLS 1.0 and 1.1 deprecated as of the end of 2020, organizations and web hosts who wish to ensure data safety need to make the move to support TLS 1.2 across all of their deployments. But what is TLS 1.2, and how does it work? To answer that, let’s first take a quick look at the history of cryptographic protocols.
SSL 1.0, 2.0, and 3.0
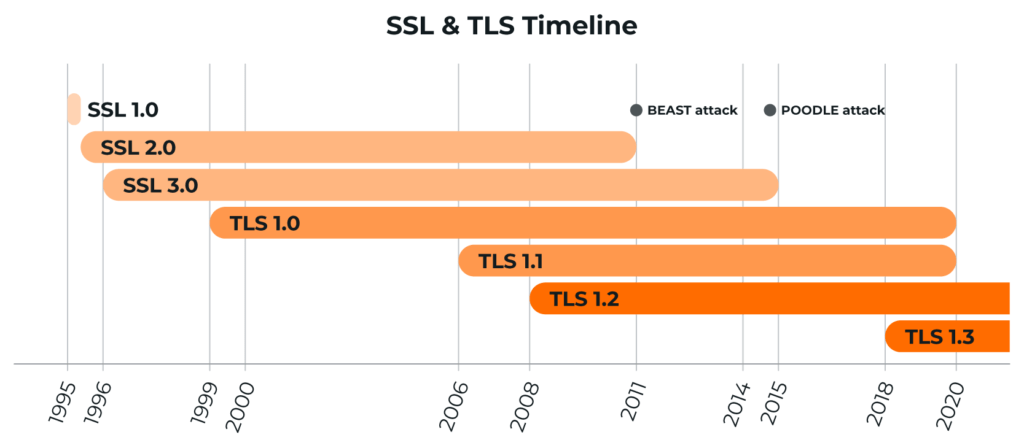
Back in 1995, when the internet was still figuring itself out, Netscape decided to address growing concerns over internet security by creating a form of encryption that would allow data to travel safely without the risk of being intercepted — Secure Socket Layers. SSL 1.0 was flawed, and never saw general release, but SSL 2.0 followed shortly afterward, and was then superseded by the much improved SSL 3.0.
This final SSL version became the standard for internet encryption for nearly two decades. Unfortunately, as technology improved, so did the capabilities of various online threat actors. In late 2014, the Google Security Team detected a major security flaw in SSL 3.0, necessitating a new approach to communication encryption. TLS was the solution.
TLS
Originally envisioned as another SSL protocol upgrade, TLS instead grew into something unique enough to deserve its own designation. And while TLS 1.0 was different enough from SSL as to make interoperability impossible, TLS 1.0 was designed with a mechanism allowing it to fall back on SSL 3.0 when needed — at reduced security effectiveness.
TLS 1.0 was followed by TLS 1.1, improving its security offering and addressing a number of newly discovered weaknesses in the previous version. And TLS 1.1 was an effective cryptographic protocol for several years. But as with all of the previous protocols, it eventually became outdated and incapable of supporting modern cryptographic algorithms. TLS 1.2 addressed these issues while also including increased protection against newly discovered security vulnerabilities.
What Is TLS 1.2?
As you’ve no doubt surmised from this brief history of online security protocols, TLS 1.2 is simply an upgraded form of TLS 1.1. TLS 1.2 was released in 2008, offering improved security, and was designed for both high performance and improved reliability. To accomplish this, it relies on a combination of symmetric and asymmetric cryptography.
More specifically, TLS 1.2 replaces the MD5/SHA-1 combination in the digitally signed element with a single hash, ensuring increased security in negotiation during the handshake. At the same time, TLS 1.2 provides improvements to both the client’s and the server’s ability to designate algorithms for the hash and the signature. TLS 1.2 also supports increased authentication encryption and adds TLS extensions and AES cipher suites.
All of this is to say that TLS 1.2 was a definite improvement over its predecessors. But, as anyone who works with technology knows, you can’t stop progress.
In 2018, the Internet Engineering Task Force (IETF) finalized and published TLS 1.3, making it the most advanced and secure cryptography protocol available. TLS 1.3 improved web performance and security by increasing TLS handshake speed, improving load times, and removing obsolete and insecure TLS 1.2 cipher suites, such as the RSA key exchange algorithm, the RC4 stream cipher, the CBC mode cipher, and others. Simply put, TLS 1.3 is designed to secure against every known TLS 1.2 vulnerability and simplify the configuration process.
So, with TLS 1.3 currently the obvious best choice for online data encryption, why should you still care about TLS 1.2?
The TLS 1.2 Deadline
As previously mentioned, as of the end of 2020, TLS versions 1.0 and 1.1 are no longer supported. That means that websites that don’t support TLS 1.2 or higher are now incapable of creating secure connections. Attempting to access those sites using a mainstream web browser (such as Google Chrome, Apple Safari, Mozilla Firefox, and Microsoft Edge) will return a “Secure Connection Failed” error message. Similarly, e-commerce sites that wish to be able to accept credit card payments and remain PCI compliant must use TLS 1.2 or higher.
The overwhelming majority of websites currently support TLS 1.2 and will not be affected by the loss of TLS 1.0 and 1.1. That said, there may still be a handful of sites that have not yet upgraded. By delaying support for TLS 1.2, these sites put themselves, and their clients, at significant risk.
Dangers of Not Upgrading to TLS 1.2
TLS 1.2 isn’t simply the obvious next step for Transport Layer Security; it’s an actual solution to serious security threats. In recent years, both TLS 1.0 and 1.1 have become vulnerable to various advanced cryptographic threats, including BEAST and POODLE. Both of these threats allow attackers to take advantage of TLS security weaknesses to recover potentially sensitive data. These are by no means the only threats facing outdated TLS protocols. Organizations that resist upgrading put themselves and their users at risk of data theft.
And beyond the dangers of insecure data, non-TLS 1.2-compliant sites will also suffer significant traffic loss. As visitors attempt to use standard browsers to access these sites, they will encounter the aforementioned error message, essentially deflecting them away from accessing the desired content. This not only means that these sites will be unable to interact with potential customers, it also negatively impacts the organization’s credibility. After all, those who see “Secure Connection Failed” are much less likely to trust that particular site, or the organization behind it, in future sessions. Outdated TLS versions have also been linked to lower rankings in Google search-engine results pages.
Finally, e-commerce sites that do not have TLS 1.2 support risk up to $100,000 in noncompliance fines and will likely be unable to process payments.
How to Upgrade to TLS 1.2
Unfortunately, there is no single button or process to ensure TLS 1.2 compatibility; depending on the platform and software solutions currently in use, the process may be extremely simple or unnervingly complex.
Start by identifying which of your systems may need to be upgraded and which don’t. Reviewing local software, legacy systems, and online stores and payment gateways may reveal TLS vulnerabilities. Platforms and connections that may need to be upgraded to TLS 1.2 include internet information services, web servers, e-commerce applications, and .Net Framework. Thankfully, e-commerce third-party support will likely have already been upgraded.
Working closely with IT and security teams is vital, as is creating a detailed migration plan. Upgrading to support TLS 1.2 is essential, particularly as TLS 1.0 and 1.1 are deprecated. But for the best possible protection, upgrade to TLS 1.3 and regularly patch and upgrade your TLS software to ensure protection against new threats.
As internet information technologies evolve, so do the threats that they face. The coordinated move to TLS 1.2 is an effective solution to help ensure optimal data security, both for organizations and customers.
Gigamon has a number of tools that help you to keep your information secure, specifically when it comes to SSL/TLS decryption. Learn how our bundled GigaSMART® SSL/TLS Decryption apps will help you to efficiently decrypt and re-encrypt traffic and meet privacy and compliance requirements — meaning not only greater security, but fewer headaches for you.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today








 Dan Daniels
Dan Daniels