What Is SSL, TLS, and HTTPS?
To understand communications security, it’s crucial to understand HTTPS (Hypertext Transfer Protocol Secure), SSL (Secure Sockets Layer), and TLS (Transport Layer Security). This article explores how they work, the need for both HTTPS and SSL/TLS, and the distinctions between SSL, TLS, and HTTPS. In short, TLS and SSL are security protocols that protect data privacy. But for businesses interested in protecting the integrity of their networks, that’s only scratching the surface.
At Gigamon, our purpose is to give you the visibility you need to ensure security and effectiveness across your entire digital infrastructure. The Gigamon Guide to Communications Security puts SSL and TLS networks front and center, illuminating the purposes and processes behind the internet’s most widely used security protocols. But to understand how these protocols work, and how they interoperate with HTTPS, let’s first take a look at why they’re so important.
For related information on what is SSL and TLS, check out these resources:
- Feature Brief: SSL/TLS Decryption
- Don’t TLS 1.3 Naked – The Risks and Benefits of Traffic Decryption Decoded for You
- TLS by the Numbers
- What Is TLS 1.2, and Why Should You (Still) Care?
Data Up for Grabs
Internet data packets travel at incredibly high speeds, reaching hundreds of thousands of kilometers per second. However, data does not arrive at its destination instantly. It passes through multiple devices as it travels between point A and point B.
And while it’s in transit, it’s vulnerable.
There’s no denying it — criminals are targeting data, and they have your business in their sights. That’s because stolen data is valuable…and costly. Research suggests that the average data breach ends up costing the target company USD 3.92 million.1
Given that we create, upload, and send approximately 2.5 quintillion bytes of data2 every day, keeping track of all of the information zipping around the internet isn’t easy.
And that’s where data encryption and authentication processes like TLS and SSL come in.
What Is Data Encryption and Authentication?
Data encryption and authentication aim to protect sensitive information by scrambling it during transmission. The intended recipient, such as a web server, receives a key that provides instructions to decrypt the data. Without this key, intercepted encrypted data appears as meaningless gibberish.
To establish effective encryption/decryption, there must be an agreement between the sender and receiver. This is facilitated by security protocols like TLS and SSL. Understanding the relationship between HTTP, TLS, and SSL is crucial before delving into their definitions.
What Is HTTPS?
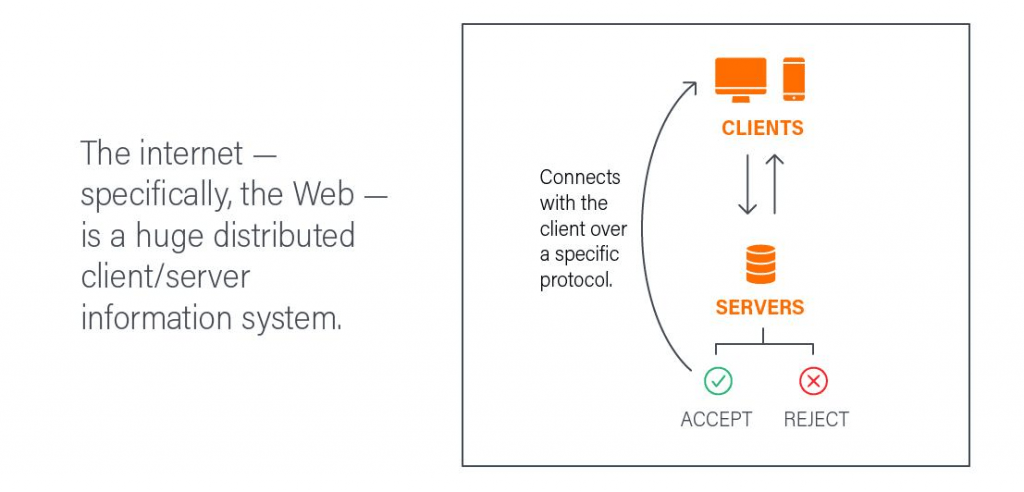
The web operates as a distributed client/server information system, where clients request information from servers using specific protocols. The protocol acts as a standard set of rules which make it possible for the servers and clients to communicate and interact.
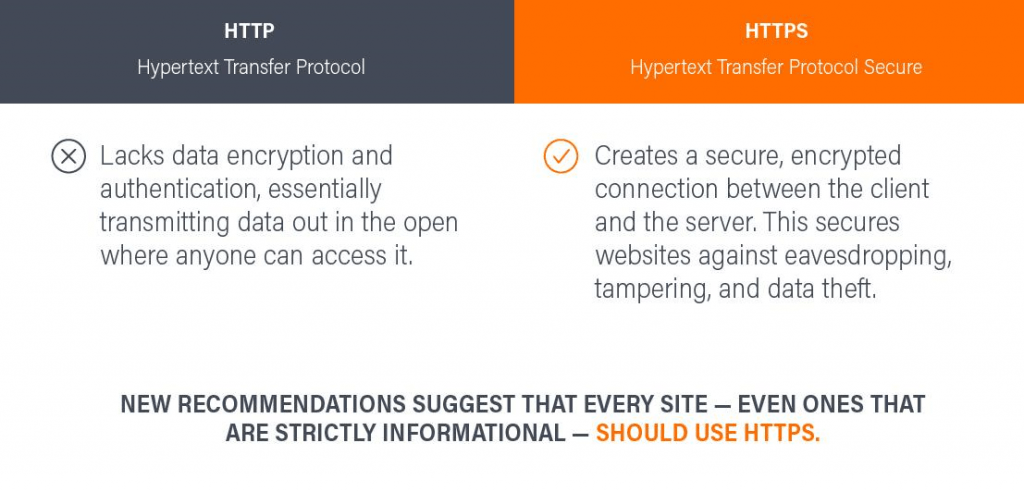
HTTP (Hypertext Transfer Protocol) is the fundamental protocol of the World Wide Web, governing data transmission, formatting, and server responses. While widely adopted, HTTP lacks security measures such as data encryption and authentication, leaving transmitted data vulnerable. To address this, HTTPS (Hypertext Transfer Protocol Secure) establishes an encrypted connection between clients and servers, safeguarding websites from eavesdropping, tampering, and data theft.
Originally, HTTPS was designed specifically for e-commerce and business websites that regularly handle sensitive information (such as passwords and credit card details), but new recommendations3 suggest that every website — even ones that are strictly informational — should use HTTPS. Google promotes this mindset by offering slight search engine rankings boosts to HTTPS sites, and by displaying “not secure” warnings in Google Chrome browser address bars on non-HTTPS sites.
HTTPS offers advantages such as:
- Data integrity: Data encryption and authentication between browser and website provide data integrity to prevent cyberattackers from viewing sensitive information
- Faster performance: The speed of data transfers increases because HTTPS reduces the data’s size
- Privacy and security: HTTPS prevents websites from being hacked between browser and server
- Secure communications: HTTPS establishes a secure connection prior to data transfers
- SEO: Search engines use it as a ranking signal and give preference to websites configured with HTTPS
- User experience: Websites using HTTPS are marked as secure by browsers, thereby enhancing user experience through trust
Overall, HTTPS offers a better, safer solution for the client/server model, but it isn’t exempt from attacks. To maintain security standards, sites must use a TLS/SSL certificate purchased from a trusted certificate authority.
What Is SSL?
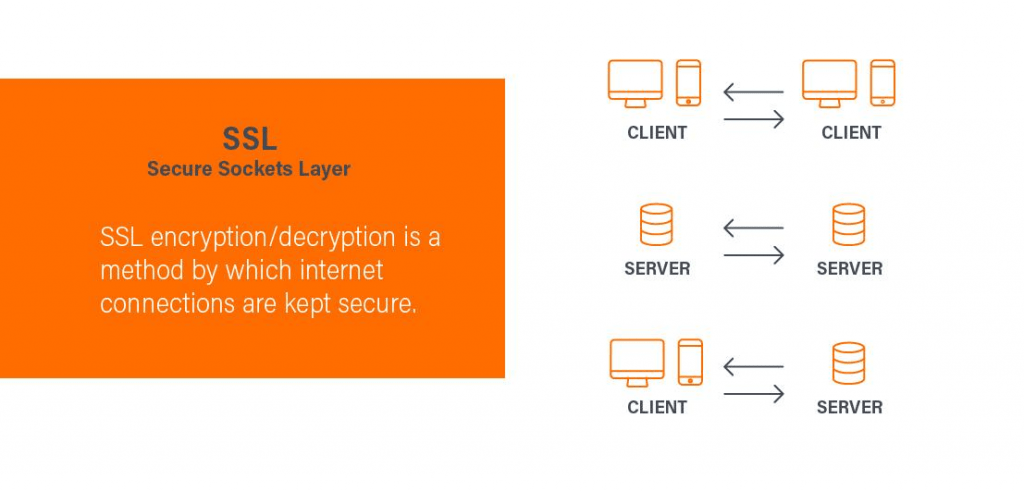
SSL (Secure Sockets Layer) was developed by Netscape in 1994. SSL is the security protocol part of HTTPS responsible for the encryption and authentication between various elements operating on a network. To better understand SSL, let’s take a look at some history surrounding the technology.
SSL encryption/decryption is a method by which internet connections are kept secure, whether they be client to client, server to server, or client to server. This prevents unauthorized third parties from seeing or altering any user data being exchanged across the internet.
SSL encryption was originally created to protect connections between customers and online businesses. However, with the rising value of mundane personal information and online browsing habits, cyber criminals began targeting non-commerce sites as well, leading to wider SSL adoption. In 1999, an updated protocol called TLS was released and has replaced SSL as the standard security certificate.
HTTPS vs. SSL
Hypertext Transfer Protocol Secure (HTTPS) combines Hypertext Transfer Protocol (HTTP) with either SSL or TLS. It’s important to understand that SSL/TLS is a part of HTTPS; together, they are a single protocol. The difference between HTTPS and HTTP is that HTTPS uses SSL/TLS to provide more security than HTTP alone. This leads to the question: Is SSL the same as TLS?
What Is TLS?
Often, the terms TLS and SSL are used interchangeably. But there is a difference between the two.
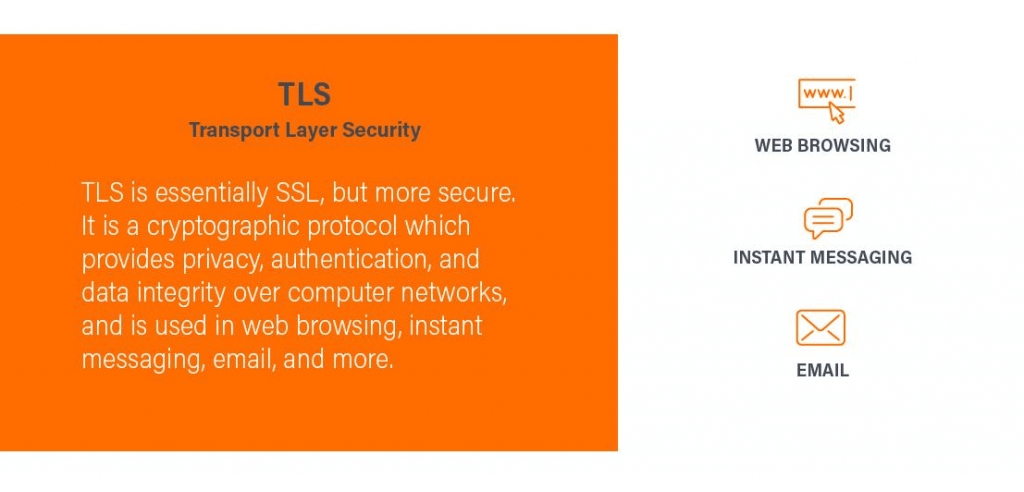
TLS, short for Transport Layer Security, is an enhanced and more secure version of SSL. TLS serves the same purpose as SSL, providing privacy, authentication, and data integrity over computer networks for various applications such as web browsing, instant messaging, and email.
While the terms SSL and TLS are used interchangeably, TLS is considered more trustworthy due to its improvements over SSL. TLS addresses known vulnerabilities of SSL, supports stronger cipher suites and algorithms, and offers a faster handshake process. It includes additional security features like the “close notify” message, HMAC (Hash-based Message Authentication Code), and upgraded cipher suites to mitigate previous SSL security concerns.
Message authentication ensures and reassures that data has not been modified during transit and allows the recipient to verify the message source.
TLS networks offer improved key management, incorporating features such as key material generation, advanced encryption algorithms, elliptical-curve keys, secure remote passwords, pre-shared keys, and Kerberos. TLS encryption is superior to SSL’s in security and data communication. TLS has undergone four versions, with TLS 1.3 being the most recent and secure. You can easily identify a TLS connection in your browser by the presence of a padlock icon and the “HTTPS” prefix in the URL.
Many certificates and references still use the term SSL; it’s well known, and the distinction is less relevant to the general populace. However, it’s important to recognize that TLS is the modern, more secure version. For accuracy, IT authorities use the term “SSL/TLS” to encompass both protocols.
HTTPS Is SSL/TLS Secure
TLS/SSL is essential for securing websites — it puts the S in HTTPS. Major browser makers highly recommend having an up-to-date TLS/SSL certificate. In 2018, Google Chrome started labeling sites without SSL/TLS as “not secure,” and other browsers adopted similar practices. Furthermore, Google rewards sites with HTTPS with improved search engine rankings, motivating website owners to prioritize SSL/TLS certificates.
How Does SSL/TLS Decryption Work?
To be effective, modern SSL/TLS needs to combine high performance and reliable security. It does this by using both symmetric and asymmetric cryptography.
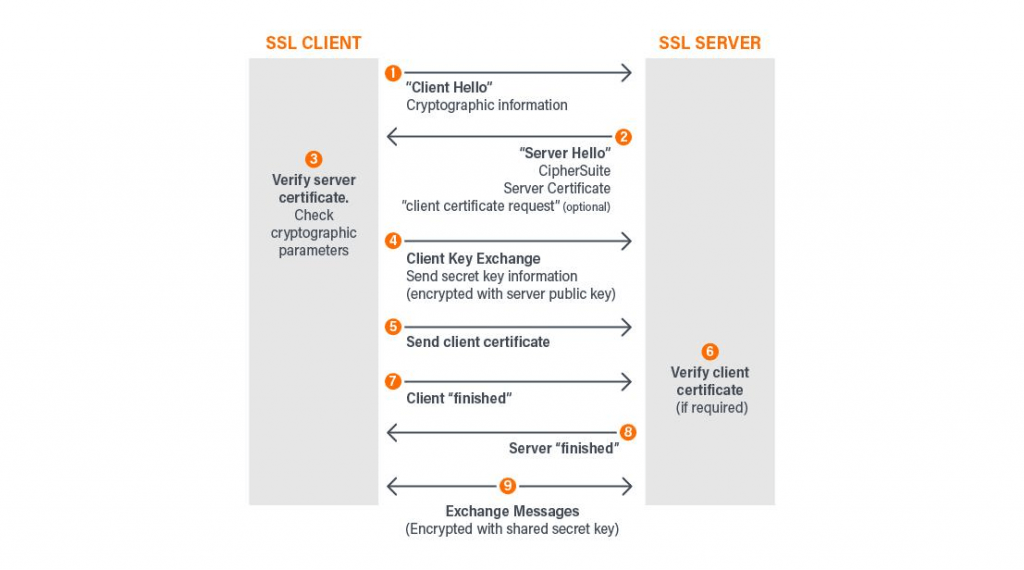
Symmetric cryptography employs a shared secret key (at least 128 bits) for encrypting data, while asymmetric cryptography relies on key pairs (private and public keys) for a more secure connection. Modern SSL/TLS uses asymmetric cryptography to generate a secure session key, which is used for data encryption/decryption and discarded afterward. The TLS handshake is a negotiation process during which the client and server establish communication, verify authenticity, determine encryption algorithms, and agree upon session keys.
The Three Levels of TLS/SSL Certificates
Although SSL/TLS offers a relatively secure solution for communications security, businesses may need extended authentication to provide increased protection for sensitive data. Organizations can opt for business-level authentication TLS/SSL certificates. How do TLS and SSL certificates work?
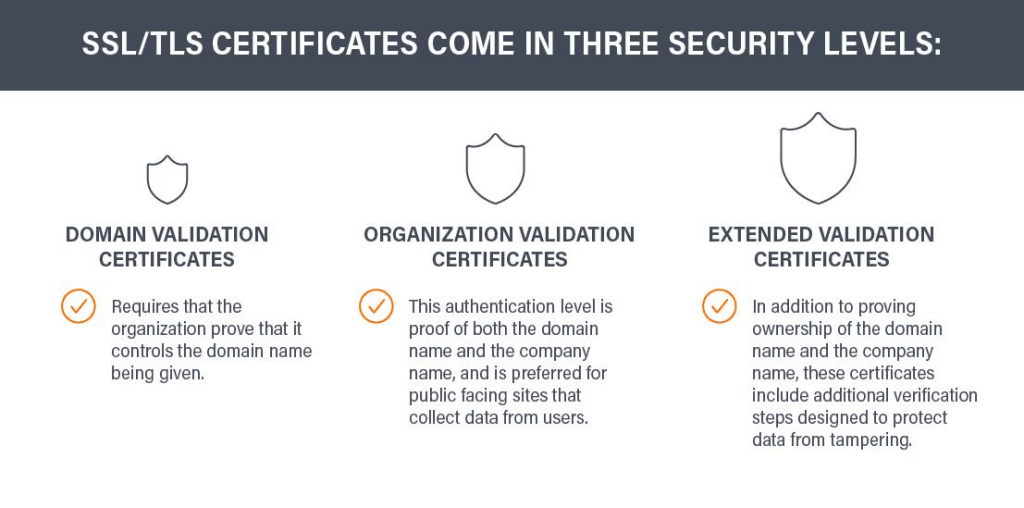
TLS/SSL certificates come in three security levels:
- Domain validation certificates
The most basic TLS/SSL certificate requires the organization to prove it controls the given domain name but does not confirm the identity of the organization. - Organization validation certificates
This requires the business to prove that it controls the domain name and that the company is legally registered as a business. This authentication level is preferred for public-facing sites that collect data from users. - Extended validation certificates
This is the most secure TLS/SSL certificate. In addition to proving ownership of the domain and company name, these SSL certificates include additional verification steps designed to protect data from tampering.
Of course, even with extended validation, TLS/SSL certificates may still be vulnerable in certain circumstances.
SSL/TLS Threat Vectors
Threat actors exploit TLS sessions to insert malware, conceal command-and-control traffic, and extract stolen data. To counter these threats and gain control over increasing TLS traffic, network administrators should consider decrypting incoming and lateral traffic.
However, before implementing decryption, it is crucial to consider key factors. Resource usage is the first factor, as decryption consumes significant processor resources, potentially impacting the performance of security tools. Privacy regulations are the second factor, requiring selective decryption to protect personally identifiable information (PII) governed by GDPR, financial, and HIPAA regulations.
Gigamon provides the solution with the Gigamon Deep Observability Pipeline.
With the deep observability pipeline, organizations can gain optimal visibility over SSL/TLS traffic, offloading decryption processor needs and freeing up resources for use by security tools. Using GigaSMART® traffic intelligence, the Gigamon Deep Observability Pipeline decrypts the right traffic and decrypts it once. It then shares relevant traffic with the right tools. This decrypt-once approach frees up network bandwidth and ensures that only authorized traffic is entering the network — effectively eliminating SSL/TLS as a threat vector.
Protect Your Users, Protect Your Business
Data shared on the internet is at risk of being targeted by cybercriminals and isn’t limited to e-commerce sites. SSL/TLS offers reliable data encryption and decryption to protect sensitive information. However, for effective communication security within your network, it’s important to have advanced network visibility plus the ability to decrypt traffic and direct it to appropriate security and monitoring tools.
The Gigamon Deep Observability Pipeline makes this possible. Giving every tool optimal visibility into all relevant decrypted traffic, Gigamon empowers security and analytics tools with increased accuracy and effectiveness. At the same time, the Gigamon decrypt-once approach improves performance and reduces latency, enabling fewer tools to handle the same amount of traffic.
After all, users put a lot on the line when they share data with your business. Protect their interests with Gigamon. Contact us to get a free demo today.
SSL/TLS Frequently Asked Questions
- Is SSL/TLS compatible across all browsers?
- Yes, all major browsers support SSL/TLS.
- Is SSL/TLS compatible with all devices and operating systems?
- Yes, SSL/TLS should be compatible with all devices and operating systems. Your certificate authority should be able to work with you to help you achieve optimal SSL/TLS configuration.
- Is SSL/TLS compatible with mobile?
- SSL/TLS should be compatible with all modern mobile devices, but some older devices may have compatibility issues when dealing with the newest protocols. Your certificate authority should be able to help you resolve any issues.
- How can I tell if a site has an SSL/TLS certificate?
- Many browsers will provide a “not secure” warning if the site is not HTTPS compliant. Even with browsers that do not issue such a warning, secured sites will be designated as “https://” instead of “http://” (followed by the rest of the address).
If you’re still not sure about a specific site or want more details, you can navigate to https://www.ssllabs.com/ssltest. This is a free service that allows you to check SSL/TLS certification for any site on the public internet.
- Many browsers will provide a “not secure” warning if the site is not HTTPS compliant. Even with browsers that do not issue such a warning, secured sites will be designated as “https://” instead of “http://” (followed by the rest of the address).
- How do I install an SSL/TLS certificate on my site?
- Depending on how and where a site is hosted, there are various methods used to add an SSL/TLS certificate. Your chosen certificate authority can guide you through the installation process and answer any specific questions you may have.
Relevant Terms:
- Asymmetric cryptography
- Ciphers that create mathematically related key pairs (consisting of one public key and one private key) for use during the encryption and decryption processes. These keys are very large (in terms of bits) and are not identical.
- Certification authority (CA)
- One of several groups officially authorized to distribute, renew, suspend or revoke SSL/TLS certificates.
- Cipher suite
- A set of algorithms designed to help secure network connections using SSL/TLS.
- Encryption
- The process of rendering data unintelligible to any and all outside observers, making the recovery of said data impossible without implementing a specifically designated decryption process.
- SSL/TLS handshake
- The process by which clients and servers are able to authenticate and verify one another, and establish encrypted communication.
- Symmetric cryptography
- Ciphers that use the same cryptographic keys for encryption and decryption. The keys must be shared between the sender and the recipient.
Further reading:
- “How Pervasive Visibility Reduces Network Downtime in the New Tomorrow”
- “How Do You Run Cryptography Faster and Stay Secure Without Tripping Over Hackers?”
References
- IBM. “Cost of a Data Breach Study.” IBM, 2019. https://www.ibm.com/security/data-breach.
- DOMO. “Data Never Sleeps 5.0.” DOMO, 2019. https://www.domo.com/learn/data-never-sleeps-5?aid=ogsm072517_1&sf100871281=1.
- Google. “Secure your site with HTTPS.” Google. Google Search Console Help. https://support.google.com/webmasters/answer/6073543?hl=en.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today








 Dan Daniels
Dan Daniels