TLS by the Numbers
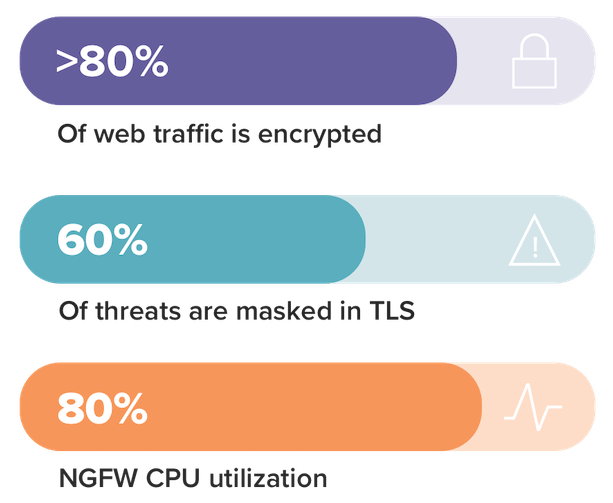
TLS (Transport Layer Security) is becoming a de facto standard on the web1 for ecommerce, online banking, email, search, social media, voice over IP (VoIP), file storage and many other public-facing applications.
With enterprises deploying more software to private and public clouds and making wider use of software-as-a-service (SaaS) applications, TLS is increasingly used for internal network traffic as well. (Note: The Internet Engineering Task Force has deprecated SSL in favor of TLS; though the acronyms are often used synonymously, I’m using TLS throughout this blog post.)
However, TLS, the very technology that makes the internet secure, can now be a significant threat vector. Sixty percent of malware communications are estimated to be hidden within TLS-encrypted traffic.2 Ops teams are aware that bad actors are exploiting TLS sessions to:
- Conceal malware
- Hide command-and-control traffic
- Cloak the exfiltration of stolen data
To gain visibility and control of the sharply rising TLS traffic numbers — and the attending security threats — it’s important to consider decrypting incoming and lateral traffic. However, before turning on decryption, you’ll want to weigh some factors.
The first is resource usage: Decryption is a processor-intensive function that steals a large amount of resources from security tools. In a study of eight leading next-generation firewalls, NSS Labs found that turning on SSL decryption degraded the firewall performance by as much as 80 percent, and reduced transactions per second by as much as 92 percent.3
Another factor to bear in mind is that privacy regulations mandate that personally identifiable information (PII — e.g., data to which GDPR, financial and HIPAA regulations apply) can never be disclosed, meaning decryption must be selective.
A great solution for both of these potential pitfalls is the Gigamon Visibility Platform. Using the platform, you can offload decryption processor needs and ensure that security tools focus on what they were designed for — detection and mitigation of malware. The Gigamon Visibility Platform decrypts the traffic once and then shares with every tool. This blog post goes through the cost of decryption in much more detail, but the upshot is that offloading decryption to the Visibility Platform vastly improves performance and latency on your network.
But what about PII? The Gigamon Visibility Platform can use Application Filtering Intelligence and Application Metadata Intelligence to selectively decrypt traffic using URL categories, IP addresses, whitelists, blacklists and other criteria. So, while decryption is available, customers have the ultimate control, using policies to ensure sensitive data remains secure.
Using the Gigamon Visibility Platform, Beacon Health was able to be very granular in selecting which traffic could be decrypted. Completing it centrally ensured that no security tool needed to take on the processing burden; data was decrypted once and shared across multiple tools in a very controlled environment.
TLS decryption is just one of the many features offered with the Gigamon Visibility Platform. In future blogs I will discuss other favorites that our customers use to maintain performance and availability for their networks.
Continue the Discussion
People are talking about this in the Gigamon Community’s
TLS/SSL Decryption topic. Share your thoughts today.
1. Google. “HTTPS encryption on the web.” Google Transparency Report. Accessed April 25, 2019. https://transparencyreport.google.com/https/overview?hl=en.
2. Desai, Deepen. “SSL/TLS-based Malware Attacks.” Zscaler. August 2, 2017. Accessed April 25, 2019. https://www.zscaler.com/blogs/research/ssltls-based-malware-attacks.
3. Stowe, Jen. “NSS Labs Expands 2018 NGFW Group Test with SSL/TLS Security and Performance Test Reports.” NSS Labs, Inc. July 24, 2018. Accessed April 25, 2019. https://www.nsslabs.com/news/2019/2/25/wwihrm3z1u70ei2pu1jotpvhtsloe6.









