Applied Threat Research and Guided-SaaS NDR
As the new Director of Gigamon Applied Threat Research (ATR), and second-year member of ATR, I wanted to share what ATR’s role is in the delivery of the ThreatINSIGHT Guided-SaaS NDR offering. First you might ask what this new term “Guided-SaaS” means? From ATR’s perspective, Guided-SaaS means:
- Designing, honing, and QAing all our detection techniques to provide rapid identification of attackers inside your network
- Removing SOC/IR distractions by providing high-quality detections, without the need for customers to have to perform training or detection tuning
- Delivering our knowledge about threats directly into the product to facilitate rapid response
- Supporting our Technical Success Management team when customers experience high-risk incidents and request advisory guidance such as intimate knowledge about an attacker’s intent and methods
As a result, ATR is one of the teams that works on our customers’ behalf in our Guided-SaaS network detection and response (NDR) offering.
What I think is powerful about ATR is our approach/methodology. We’ve shared some components of our methodology before in blogs such as:
- So, You Want to Be a Detection Engineer?
- Quality Control, Keeping Your Detection Fresh
- Dialing in Your Detection Coverage with MITRE ATT&CK
But today I thought sharing our ATR Charter would help explain how we contribute to the ThreatINSIGHT Guided-SaaS offering:
Mission: Dismantle an adversary’s ability to impact customers
Methodology: Gigamon ATR pairs security experts who track adversary activity and behaviors with specialized data scientists to create efficient, actively managed high-fidelity detection techniques that span the breadth of the MITRE ATT&CK framework.
- Threat Research to Accelerate Detection
- Research threat actors, their tools, and their infrastructure to produce leading ATR proprietary threat intelligence and knowledge
- Curate public and private intel feeds to augment ATR’s threat intelligence
- Provide ThreatINSIGHT with knowledge of threat actors’ intents, TTPs, and tools
- Detection Engineering to Achieve High-Fidelity
- Research, build, and maintain high quality machine learning and behavioral analysis engines
- Apply all techniques to global INSIGHT Cloud Data Warehouse datasets, enabling identification of emerging threats
- Rigorous QA to all detection techniques and intelligence to ensure high-true positive rates without customers needing to perform detection tuning
- Security R&D to Innovate
- Continuous research, prototyping, and validation of future detection and investigation capabilities
Expertise: The ATR team is composed of trained experts in incident response, forensic analysis, threat research, engineering, and data science. The pairing of these disciplines delivers accurate network detections of adversary behavior and knowledge of the adversary’s intent and tactics to help your SOC/IR team triage, investigate, and respond with certainty.
Threat Researcher/Intelligence | Detection Engineer | Data Scientists | |
Passion | Dismantling cyber adversaries | Solving difficult problems with agility | Apply ML to real world scenarios |
Experience |
|
|
|
Responsibilities |
|
|
|
Measured: We hold ourselves accountable for both the scope of threat detections we provide and the subsequent performance of our detection techniques.
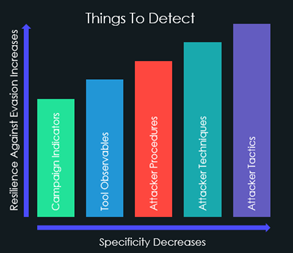
- Scope: We examine all threats through the lens of “Detection Specificity” versus “Resilience Against Evasion.”
- Performance: Threats change, so our detection capabilities must change with them. By measuring baseline performance, we constantly assess our detection content to ensure high quality. This allows us to be able to quickly identify dormant, noisy, or no-longer-accurate detection techniques.
We have a saying at Gigamon that ThreatINSIGHT was built by responders for responders. Whether it is in the technology we provide, the unique, modern SaaS management experience we provide, or the advisory guidance we make available to our customers, enabling fast detection of adversaries and rapid response is at the heart of everything we do.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today