7 Key Things to Know for Effective Decryption
Today more than 96 percent of web traffic is encrypted. As the amount of encrypted web traffic has increased, attacks leveraging malware in encrypted traffic have gone up significantly. In fact, 90 percent of malware uses encryption. This results in data breaches, which cost an average of $9.5M each. Lack of visibility into encrypted traffic is a huge problem for organizations. You can’t secure what you can’t see.
How can you solve this challenge? You must decrypt encrypted traffic to protect your organization from these hidden threats. The NSA recommends controlling plaintext traffic, policies should be built around insider threats, and decryption must be centralized with privacy requirements and regulations. In addition to the NSA guidelines, below are seven key things to know for effective decryption.
1. Know Your Traffic
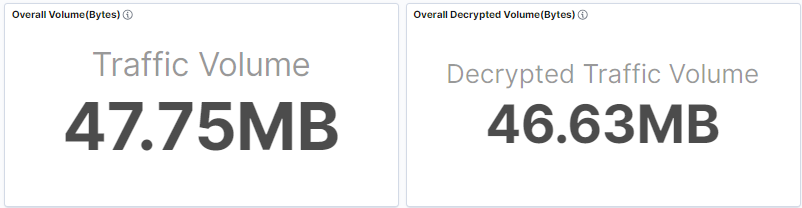
First, before deploying any TLS/SSL decryption solution, know the total volume of traffic in your network and the amount that is encrypted. Gigamon TLS/SSL Dashboard provides you with granular visibility into your encrypted traffic. It delivers insights into the total traffic volume and decryption rate.
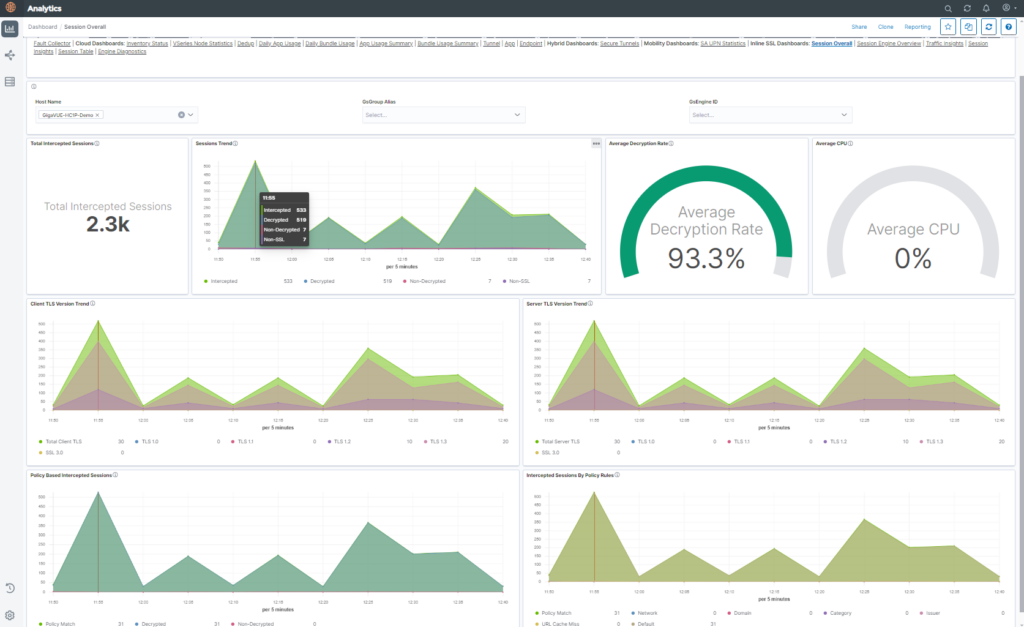
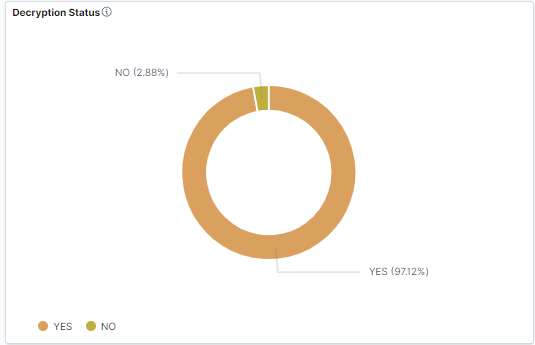
2. Know the Direction
Second, know how and where your traffic is traversing the network. For a TLS/SSL solution to work flawlessly, it needs to see both directions of the traffic. Asymmetric traffic can cause incomplete TLS/SSL decryption if all traffic is not combined and fed to the solution.
Gigamon Resilient Inline Arrangement capability with GigaSMART TLS/SSL solution addresses this by decrypting and correlating traffic before forwarding it to the inspection tools, ensuring complete visibility without intrusive network changes.
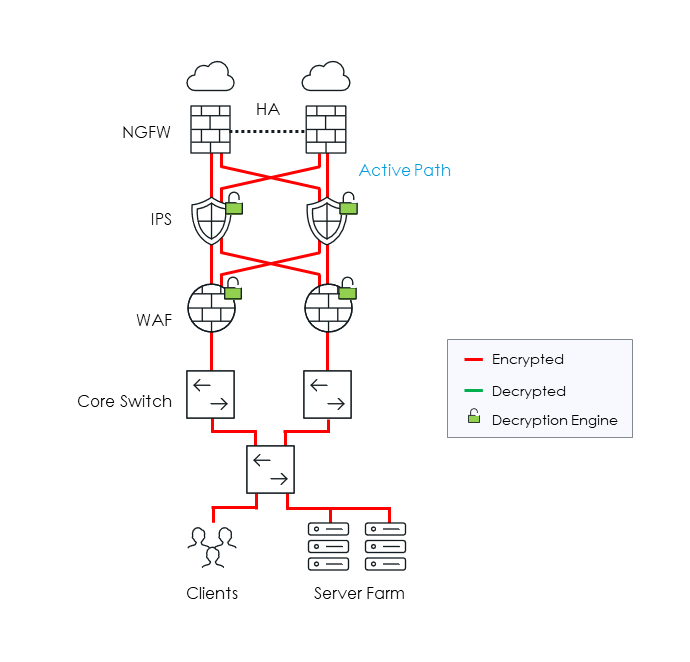
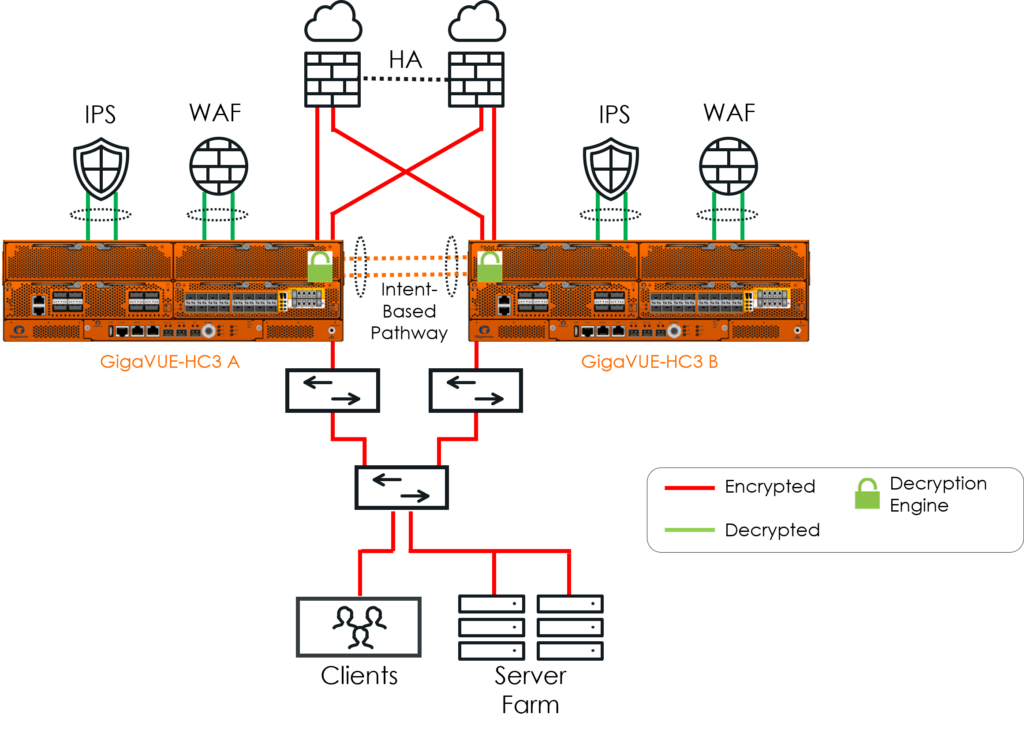
3. Know Your Limits
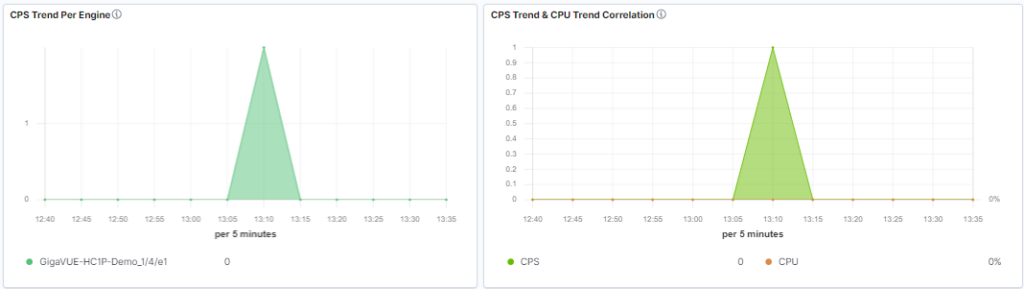
Different solutions offer different TLS/SSL decryption capacities for inbound or outbound traffic. It’s important to know how much traffic can be decrypted by a solution based on the active number of connections and volume of TLS/SSL traffic.
4. Know Your Needs
It is important to know which traffic needs to be decrypted. Either you’re hosting on-premises web applications that are accessed internally or externally, or you want to decrypt all the traffic leaving your network.
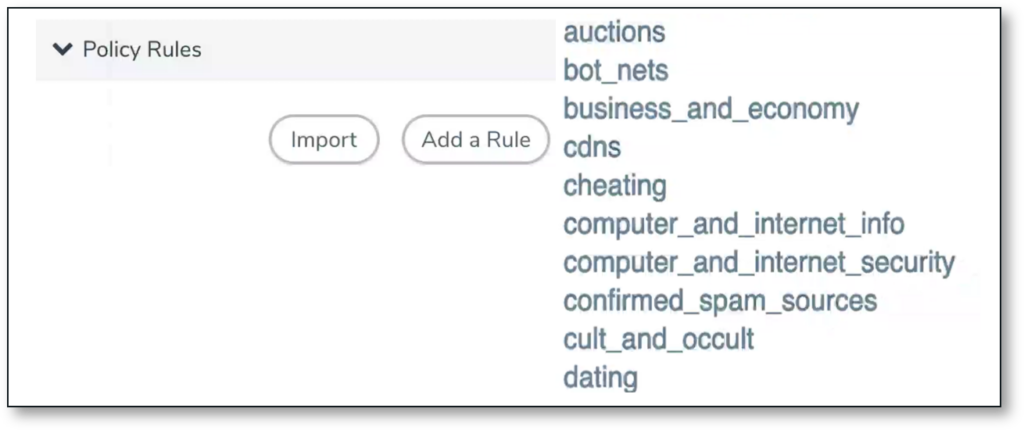
For compliance purposes, it becomes essential to decrypt only certain traffic. For instance, decrypting financial and health data violates privacy laws. Hence, it is important to have the flexibility to decrypt selectively.
Gigamon provides you with the flexibility to decrypt or not decrypt certain traffic. For instance, for PCI purposes you can choose to bypass decryption of financial data, such as credit card information.
Once you have the decrypted traffic, you can steer that traffic to the tool of your choice, whether it is just one tool or multiple tools.
5. Know Your Priorities
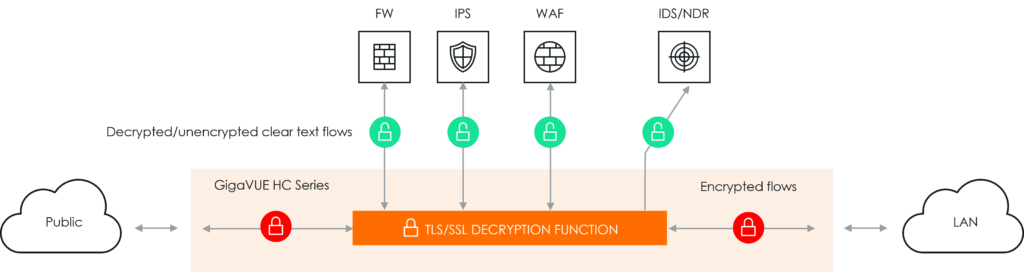
Many security tools and firewalls offer TLS/SSL decryption solutions. Howerver, exposing malware in encrypted traffic, thereby enhancing security and performance across the hybrid cloud.
6. Know Your Growth
TLS/SSL decryption may be easy to configure for your current setup, but what happens if your traffic volume grows? How easily could you scale your TLS/SSL decryption solution over time, and what would the cost impact be?
Decrypt once and feed many with centralized Gigamon TLS/SSL decryption. It is easy to scale up or down and feed any inline and out-of-band tools, including security and application performance tools.
7. Know Your Solutions
Do your research when deploying TLS/SSL decryption solutions. Different solutions offer varied performance with different ciphers. Some solutions are easier to deploy or scale better than others. Thoroughly research available solutions and their pros and cons.
Gigamon TLS/SSL Decryption brings deep observability to encrypted traffic. Learn how Gigamon helps streamline and boost the effectiveness of your security and monitoring tools with GigaSMART® TLS/SSL Decryption.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today








