Definitive Guide to Hybrid Clouds, Chapter 5: Threat Detection and Response in the Hybrid Cloud
Editor’s note: This post explores Chapter 5 of the “Definitive Guide™ to Network Visibility and Analytics in the Hybrid Cloud.” Read Chapter 1, Chapter 2, Chapter 3, and check back for future posts covering Chapters 6 and 7.
For all the good it does in helping your business run more leanly and agilely, the cloud can also create more work for your security team by expanding your network’s attack surface.
Attackers are laser-focused on accessing and exfiltrating sensitive data in the cloud, and they’re using increasingly sophisticated malware-based espionage and other exploits to maintain a persistent presence within cloud networks.
Are You Making It Easier for Threat Actors?
Unfortunately, the answer could very well be yes. If your security team doesn’t have pervasive cloud network and event visibility, threat actors have more leeway to:
- Zero in on cloud administrators, engineers, and DevOps teams that have privileged access to deployment pipelines and internal services
- Use cloud services as a delivery mechanism for malware and other malicious content
- Abuse overly permissive identity policies in cloud environments
- Find vulnerabilities in misconfigured cloud environments
- Disguise attacks as insider behavior
As a result, advanced malicious actors are using cloud services for major elements of their targeted campaigns, including denial-of-service efforts, command-and-control (C2) systems set up in the cloud, cryptocurrency mining, and password cracking systems. And without cloud traffic visibility, your SecOps team can’t detect, hunt, or investigate attacker behavior effectively.
Protect Your Hybrid Cloud Network with a Sustainable Strategy
To stay on top of increasingly complex and stealthy behavior, your SecOps must adopt new processes and tools that improve cloud monitoring, threat detection, and event remediation, starting with:
- Deep packet inspection and analysis at all layers, based on rich metadata extracted from network flows — both inbound-outbound (North-South) and lateral (East-West) traffic.
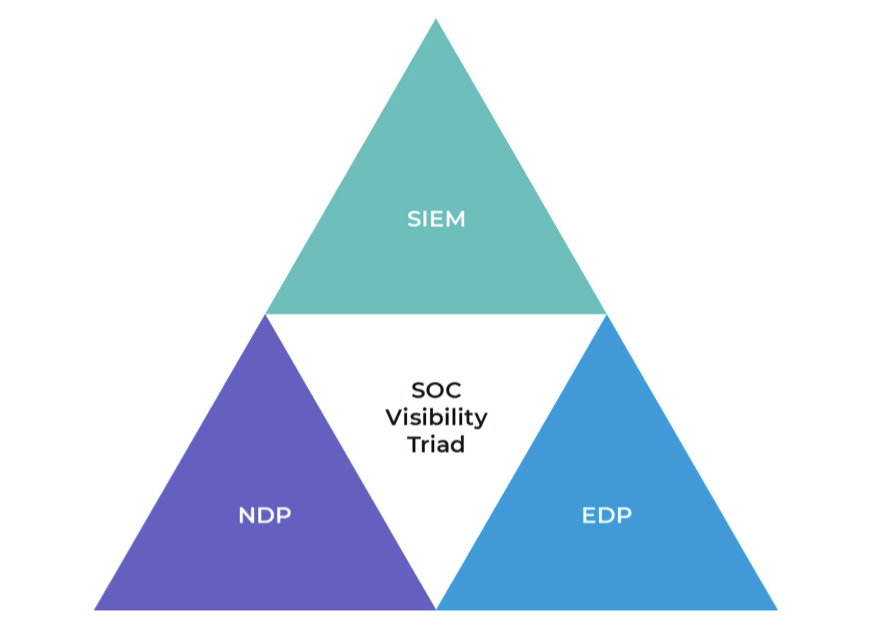
- Extended detection and response (XDR), which combines network detection and response (NDR), endpoint detection and response (EDR), and SIEM (as depicted in Figure 1) and extends NDR and EDR to incorporate deep correlation and analytics and create a more holistic analysis capability.
- SSL/TLS inspection for both cloud and on-premises that identifies the encryption in place and forwards it to network monitoring devices
- Historical network metadata collection to ensure organizations can rapidly analyze events in context and conduct thorough investigations
Make sure you have all the details you need to develop a future-proof hybrid cloud security strategy. Read the Definitive Guide™ to Network Visibility and Analytics in the Hybrid Cloud.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Hybrid/Public Cloud group.
Share your thoughts today