Eliminating Adversaries’ Dwell Time Advantage
During my time on a security team, working through ambiguity became an integral part of the job. With attackers constantly changing their tactics, our strategy had to adapt and accommodate new threats. One thing I love about being part of the Gigamon ThreatINSIGHT™ team is that we examine real problems facing security teams, build hypotheses, then deliver solutions into practice. The latest release of ThreatINSIGHT is both the culmination of a great team effort and the commencement of enterprises leveling the playing field against “low and slow” attacks by providing solutions to three real problems facing security operations teams today.
Real Problem #1: Dwell Time
For over a decade, we have seen disturbing reports that show adversary dwell time exceeding well beyond acceptable ranges (280 days, as reported by IBM), giving adversaries the opportunity to find and breach an organization’s most sensitive data and intellectual property, aiming to hold it for ransom.
In response to this, security teams would dig into their SIEM or log aggregator to try to find adversaries but fall short because, despite the volume of data stored (and disk space paid for), the data lacked the depth or richness to unearth the presence of an adversary.
Security teams then turned to NDR, whose metadata is richer in content and more compact than raw packets. However, most NDRs only focus on short-term detections and only retain the network metadata for a few weeks, if an on-prem solution, or 30 days, if a cloud-native NDR. This helped, but as illustrated by the SUNBURST kerfuffle, security operations teams often need 9 to 12 months of data to identify initial access.
It’s 2022 now, and cloud infrastructure allows us to retain data intelligently, so why are NDR tools only retaining data for such short periods?
The latest release of ThreatINSIGHT is disrupting the norm. It now provides rich network metadata for 365 days and gives security teams a simple way to save off data for cold storage if desired.
Real Problem #2: Lack of “R” in NDR
Despite record spend on security technology, 52 percent of SOC analysts report the need to access more out-of-the-box content from their solutions. When it comes to identifying and responding to the presence of adversaries inside an organization’s network, most NDRs seem to have forgotten the “R” in NDR. These ND_ vendors quickly suggest you use other tools to perform detection triage, hunting, or investigations because they lack out-of-the-box capabilities, but want you to trust them and allow them to automatically send a mitigation command via an API to an inline tool.
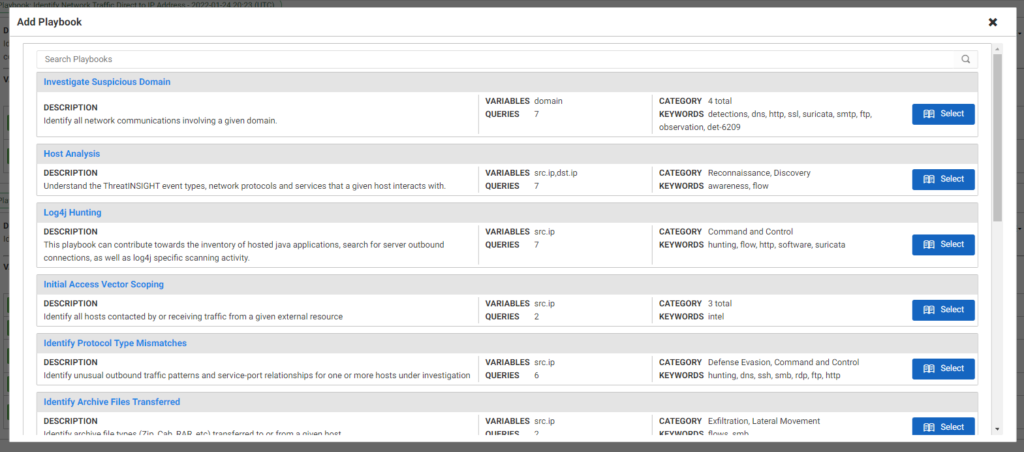
ThreatINSIGHT has never taken that approach. ThreatINSIGHT was built by responders, for responders and has always provided rich triage, hunting, and investigation capabilities. And we don’t rest on our laurels. The new release of ThreatINSIGHT now includes Guided Playbooks designed by Gigamon ATR (Applied Threat Research). These investigation and hunting playbooks guide investigators to identify attackers based on real-world behaviors, with just a few mouse clicks.
Real Problem #3: Serial Investigations and Hunting
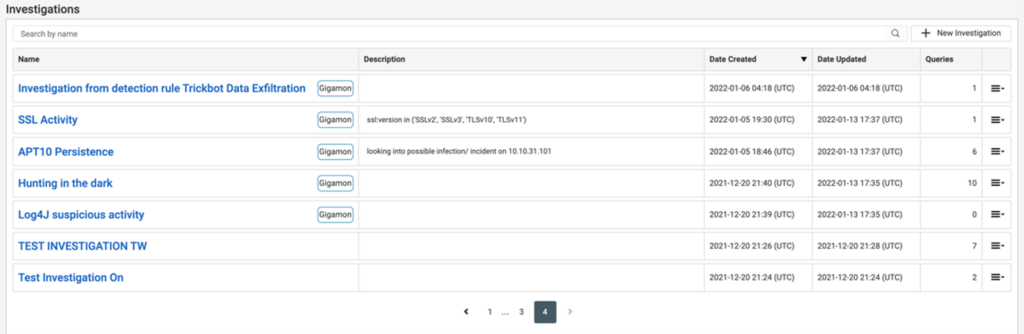
In conversations with our clients, we learned what they viewed as a limitation with ThreatINSIGHT. While they loved the ability to investigate and hunt through advanced queries against retained enriched network metadata, they wanted to speed up the response process by being able to run queries in parallel and allow global SOC members to all work together with the results.
ThreatINSIGHT now includes parallel hunting so SOC teams can coordinate threat hunting and investigation efforts across their worldwide team. Team members can see existing queries that are part of an investigation as well as the results. Additionally, we built in the ability to pivot to pre-designed queries with results already read for review.
Innovation
I’m proud to be part of ThreatINSIGHT’s approach. We listen. We empathize. We brainstorm. And we deliver solutions to help our customers identify adversaries and respond quickly with confidence. We changed how NDRs are deployed and operationalized with the introduction of Guided-SaaS, and now we are disrupting the market with 365-day network metadata retention. These advances are a big deal. They change the NDR market landscape. They change the way enterprises battle adversaries and win.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s ThreatINSIGHT group.
Share your thoughts today