Gigamon ThreatINSIGHT: Highlighting the Value of Reporting for Security Operations
Updated September 30, 2021.
The value of reporting can never be overlooked. One of the most difficult challenges for security operations is to consistently communicate and illustrate their security posture to executives and other teams that rely on accurate, current, and actionable data. Assessing an environment on its whole is difficult because very few solutions have comprehensive and consistent visibility, but Gigamon ThreatINSIGHT™ is uniquely positioned to empirically measure an organizations health and preparedness for incidents. With visibility to an organization’s hybrid cloud, core network, and remote users, ThreatINSIGHT can analyze the network traffic of every device and assess the organizations security posture over time.
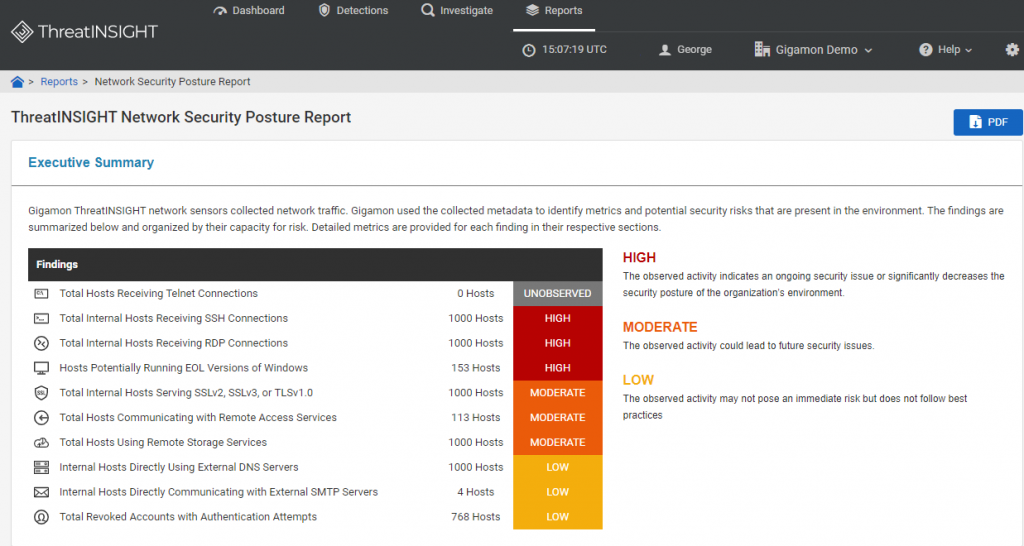
ThreatINSIGHT Security Posture Report
The ThreatINSIGHT Network Security Posture Report exposes hidden risks where improved hygiene can close gaps that can be abused by adversaries. Due to ThreatINSIGHT’s ability to assess Layer2 through –Layer 7 traffic, it can identify suspicious connections (TCP, SSH, RDP, etc.), unsupported software or activity (EOL OS, Deprecated SSL, revoked accounts with authentications, etc.), and hosts involved in high-risk communications (using external DNS servers, external SMTP servers, remote access services, etc.). Examining periodically and addressing the hidden risks allow security teams to illustrate improvement to their security posture over time.
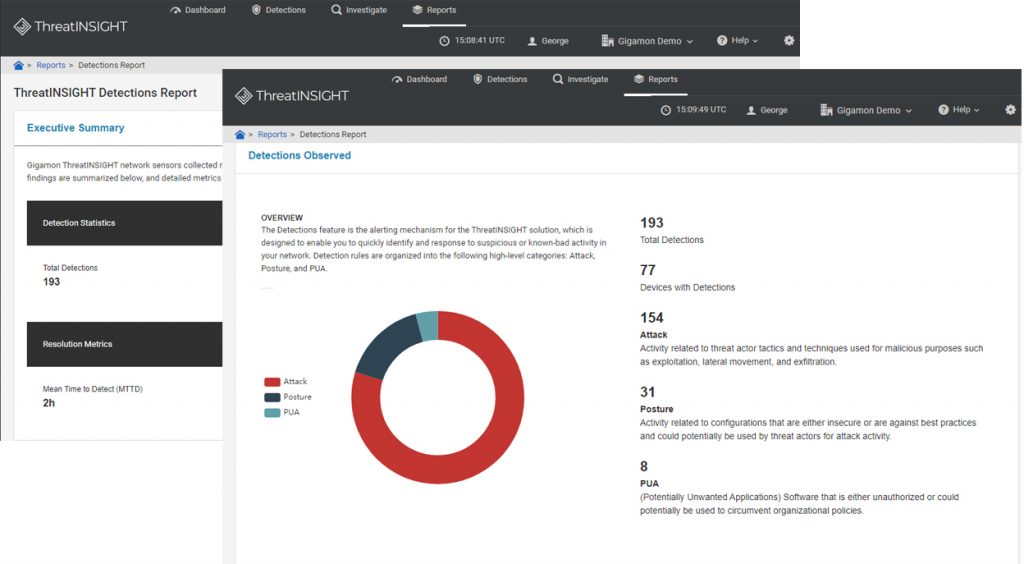
ThreatINSIGHT Detections Report
Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) combine to represent the time in which an adversary can negatively impact an organization and are important metrics in security operations as they illustrate a team’s efficiency and effectiveness in dealing with threats. Over the years reports such as the Verizon Data Breach report and Ponemon Institute studies show scary enterprise MTTD and MTTR numbers, the reality is that it is not easy for SOCs to measure as it requires extensive visibility. However, Gigamon ThreatINSIGHT’s ability to observe all devices over time and retain historical network activity allows organizations to measure their improvement in dwell time. Further, ThreatINSIGHT provides the critical capabilities allowing SOC and IR teams to rapidly triage and respond to threats:
- Capture and retention of rich contextual L2-L7 network metadata for all device activity
- Automatic enrichment of the retained network metadata with entity (user, hostname, geolocation, etc.) and event intelligence (external threat information, passive DNS, whois, etc.)
- Guided Next Steps to aid SOC analysts to triage detections rapidly.
- Robust omnisearch query capabilities and graphical visualizations of the adversary’s activity to perform thorough investigations.
- For active high-risk incidents, access to Gigamon security analysts and incident responders to receive information about the threat actor and incident investigation best practices.
The ThreatINSIGHT Detection Report provides a comprehensive review on detections, attack stages, severity levels, confidence levels, and resolution metrics. Because of the comprehensive visibility provided by ThreatINSIGHT, organizations can obtain a true representation of the time adversaries are active in their environment (MTTD and MTTR) and overtime illustrate the improved efficiency and effectiveness of their security and incident response operations.