Gigamon ThreatINSIGHT: How Not to Ignore the “R” in NDR
In the world of Security Operations when dealing with preventing data breaches, ransomware, or insider threats, much is made about Detections. It is natural to want to talk about what techniques can be used to identify the adversary. Detection is fundamental – no doubt. However, in the world of Network Detection and Response (NDR) so many vendors pass the buck on “Response” by providing limited triage, investigation, or hunting capabilities and simply passing the detection information over to a SIEM or SOAR platform. Gigamon ThreatINSIGHT™ Guided-SaaS NDR has powerful machine learning, behavioral analysis, and proprietary threat intelligence that all work together to deliver high fidelity true positive detections, but that is just the beginning. ThreatINSIGHT delivers the “R” in NDR.
Some argue that NDR’s do not offer “Response” at all because as a solution they are not the technology taking mitigating actions on traffic or hosts. In contrast, we consider the tasks and responsibilities of the incident responder whose job is to threat hunt, investigate triaged detections, and form a comprehensive response plan for implementation. By their job title and core responsibilities they are doing “response” and thus in parallel if NDRs deliver capabilities that enable them to threat hunt, investigate triaged detections, and form comprehensive response plans then NDRs are certainly delivering “Response”.
ThreatINSIGHT Guided-SaaS NDR is designed to offer an end-to-end detection and response platform for the identification and removal of adversaries. For this blog, we will focus on the “response” steps and how ThreatINSIGHT provides value.
Triage
Whether a detection originates from ThreatINSIGHT or from other security solutions, SOC analysts must triage the detection and determine if it is real. For all detections identified by ThreatINSIGHT, the solution provides guided next steps unique to each threat. These steps provide clear instructions on how to validate the detection is real, enabling the SOC analyst to proceed with confidence and speed.
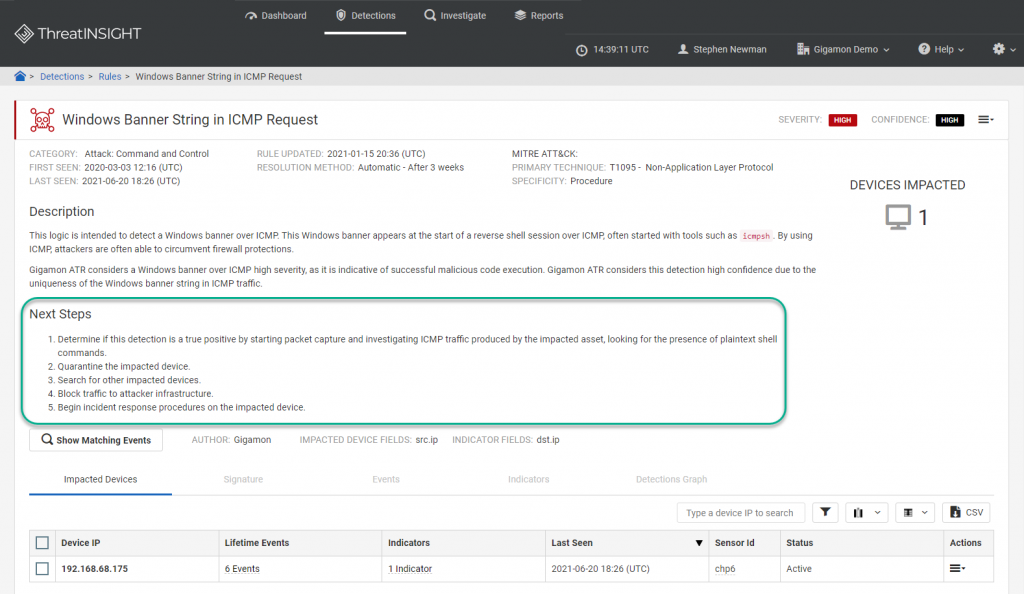
Hunting
ThreatINSIGHT provides incident responders with tremendous abilities to hunt for adversaries. By observing all devices over time, capturing, and retaining L2-L7 network metadata on their activity, responders have the necessary visibility to hunt. ThreatINSIGHT goes further by providing Observations to serve as starting points for hunting expeditions. Observations are activities that the ThreatINSIGHT machine learning or behavioral analysis techniques have flagged as potentially malicious, but lack to corroborated evidence to confirm as a detection. Hunters can quickly begin with an “Observation” and use the ThreatINSIGHT solution’s robust omnisearch query capabilities and visualization techniques to determine if an adversary is present.
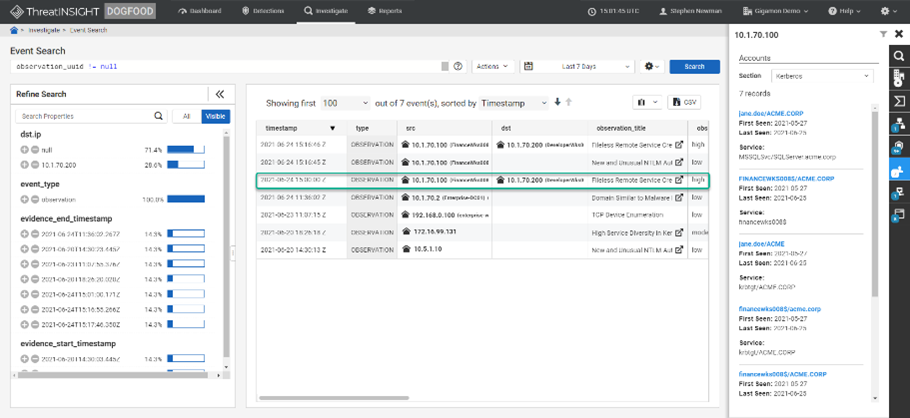
Investigations
ThreatINSIGHT provides two robust methods to investigate threats (also valuable for hunting). The first is the fast omnisearch capability powered by the Insight Query Language (IQL). With faceted search results the investigator is provided with pre-grouped, guided selections to quickly narrow the focus or targeted lines of inquiry. This ability to access historical enriched network metadata, incident responders can extract the evidence to the impacted devices, users, and systems to formulate a comprehensive understanding of the adversary’s activity.
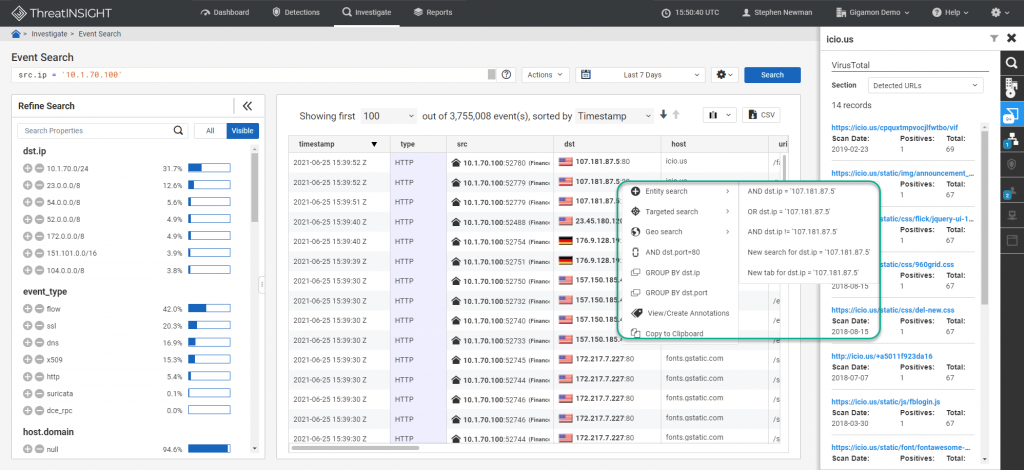
While queries are powerful, sometimes lists and search results contain but do not easily expose relationships. ThreatINSIGHT’s Visualizer allows incident responders to both hunt and investigate with graphs that illustrate node relationships that otherwise might be missed. Powered by the same L2-L7 enriched network metadata, responders can observe lateral spread, reveal similar indicators, and ultimately determine a strong response p
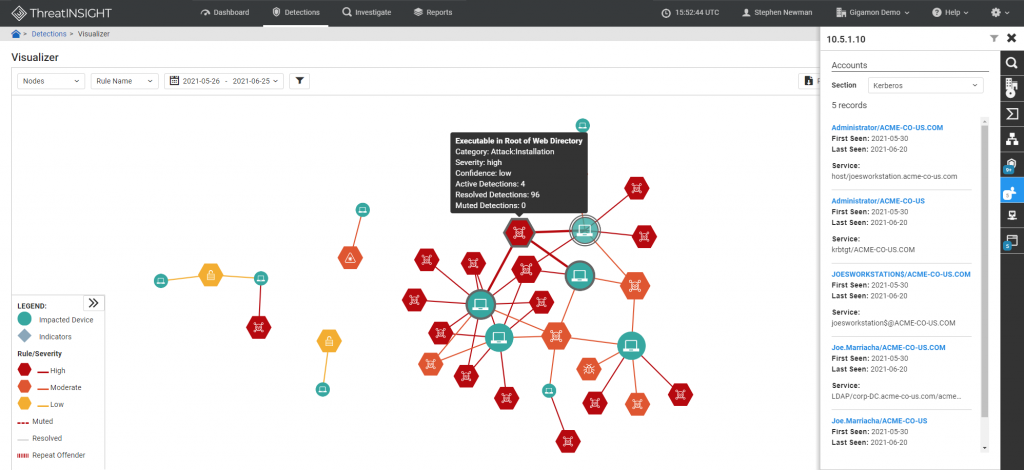
Guidance
Sometimes, even with the most powerful technology, security analysts and incident responders need assistance. The pressure is immense and uncertainty about how new and evolving threats behave or how best to carry out an investigation can slow a responder’s actions. During high-risk active incidents, ThreatINSIGHT Guided-SaaS NDR provides security teams with access to experienced Gigamon security analysts and incident responders (Technical Success Managers – TSMs) who upon request can provide up to the minute information on the threat actors TTPs and intent as well as guidance on how best to investigate the threat. The result is that responders can move forward with certainty and respond faster to reduce dwell time.








