MITRE ATT&CK Is About Incident Response. It’s Not an NDR Vendor Measuring Stick
The MITRE ATT&CK framework has become the tool of choice that allows cybersecurity specialists to all speak the same language and have a better understanding of the techniques used by our adversaries, ultimately enabling teams to increase the speed and accuracy of active threat response.
But alas, we are also seeing it being misused as a security vendor measuring stick.
Table 1. Dispelling myths about what the MITRE ATT&CK framework is and is not.
| MITRE ATT&CK framework is: | MITRE ATT&CK framework is NOT: |
| A globally accessible knowledge base of adversary tactics and techniques based on real-world observations | A unique vendor feature |
| A collection of cyber adversary behaviors and a taxonomy across an adversary’s lifecycle | An endorsement of a vendor’s solution |
| A foundation for the development of specific threat models and methodologies | A replacement for cyber frameworks or models |
| A common “language” to bring communities together to help security operations, threat intelligence, and security architectures | A checklist of techniques you must be able to detect. (Note: Some parts of ATT&CK are for intel purposes only and you cannot or should not try to detect them.) |
As an example, here are common misleading statements by network detection and response (NDR) vendors:
- “[Vendor/product] covers 97 percent of the network techniques identified by the ATT&CK model.”
- “By checking a potential detection tool against which TTPs it’s able to spot, you’ll be better able to understand how that tool will perform in the wild.”
- “[Product] provides especially strong coverage of late-stage TTP categories, with 89 percent coverage of the TTPs in the lateral movement, command and control, and exfiltration stages, and 100 percent coverage of TTPs labeled as ‘Requires Network.’”
Unfortunately, vendors point to detecting a single procedure for a technique as if they have coverage for the entire technique or every adversary’s use of the technique. This simply is not true and provides a false sense of security.
Fair and Accurate Representation of NDR Technologies and the MITRE ATT&CK Framework
With the fog lifted on what MITRE ATT&CK is and is not, we can now speak to how security teams can effectively use MITRE ATT&CK along with NDR technology to improve their security posture.
1. NDR technologies should annotate detections against specific MITRE ATT&CK techniques.
While it is inaccurate to use the ATT&CK framework as a detection measuring stick, the annotation of ATT&CK technique by the NDR vendor is critical. It allows the vendor and the security team to speak the same language. The security analyst will immediately understand the behavior of the attacker being identified by the NDR.
2. NDR technologies should:
- Guide security teams on how to triage detections based on the ATT&CK techniques
- Guide security teams on best practice next steps for investigations based on the ATT&CK techniques
- Facilitate hypothesis-based hunting against ATT&CK techniques
NDR’s focus is not only detection but also response. Response includes the ability to hunt, triage, and investigate. By first annotating detections against the ATT&CK techniques, the vendor should provide guidance to the security analysts on how to both triage and investigate the threat. If the NDR vendor does not give this guidance, they are not truly helping with response. Secondly, as the ATT&CK framework is a catalogue of adversarial techniques, it serves as a phenomenal starting point for any hypothesis-based hunting efforts. As such, an NDR should provide a fast, comprehensive search capability that allows a hunter to quickly assess their hypotheses.
3. NDR technologies should highlight which ATT&CK techniques are being used by adversaries in an organization so security teams can take preventative steps to eliminate those attack surfaces going forward.
NDRs along with EDRs close the SOC visibility gap by providing a comprehensive view into the activity on an organization’s assets and network. By exposing the techniques used successfully by adversaries in their network, security teams can take countermeasures making it more difficult for adversaries to be successful.
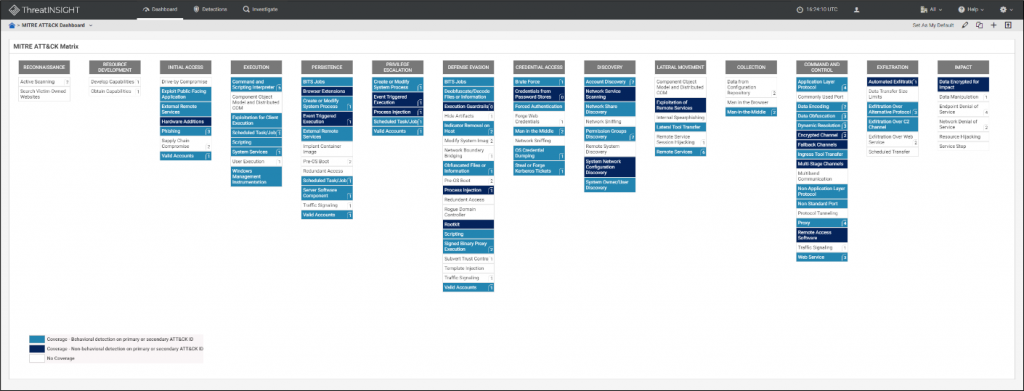
Gigamon ThreatINSIGHT and the MITRE ATT&CK Framework
At Gigamon, we indicate that ThreatINSIGHT “identifies network activities broadly across the MITRE ATT&CK framework, with focus on post-exploitation stage techniques.” While we do have detection capabilities across the MITRE ATT&CK framework, we do not claim a false percentage of coverage, as every attacker’s approach to a technique is different.
With the ThreatINSIGHT 2021.3 release, we continue to extend annotation of threats using the MITRE ATT&CK framework technique descriptions. We use the MITRE ATT&CK framework to:
- Annotate all our detections and behavioral findings to facilitate faster response.
- Educate and inform, ensuring we are all speaking the same language in the battle against cyber adversaries.
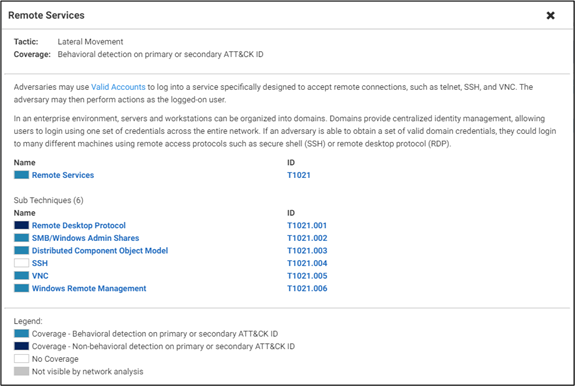
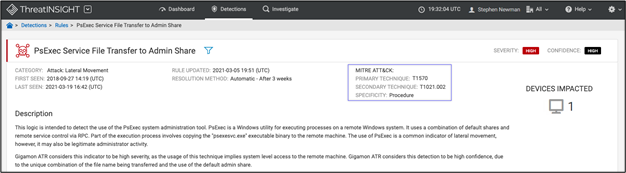
- Create new detection techniques that innovate and extend our ability to dismantle threats with our customers and label the detections with the specific MITRE ATT&CK Primary & Secondary Techniques. Example: Tactic: Lateral Movement Detection | Technique: Lateral Tool Transfer | Sub Technique: Remote Services: SMB/Windows Admin Shares.
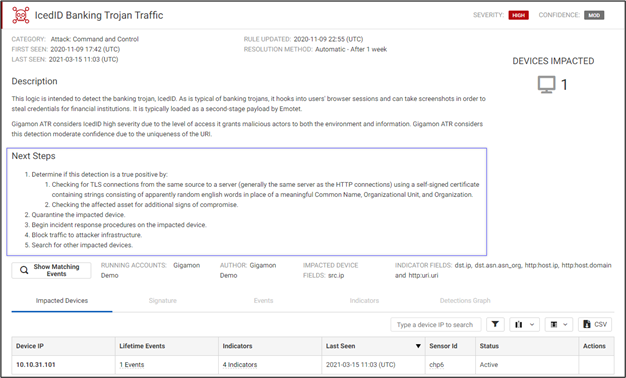
- Include clear, non-generic guided next steps to our clients for each finding. Example: Steps to triage and investigate IcedID Banking Trojan Traffic.
The Gigamon ThreatINSIGHT team is committed to helping our customers dismantle active threats. We are literally a team of responders who have built a solution for other responders. We are partners with our customers. We are proud of our solution and the value it provides to our clients, and we look forward to helping you.
Learn more about Gigamon ThreatINSIGHT and the team.
ThreatINSIGHT customers can read the full 2021.3 release notes in the Help section of the ThreatINSIGHT web portal.
“A tool built for SecOps, not marketing campaigns.” – Gigamon ThreatINSIGHT Customer
The Gartner Peer Insights Logo is a trademark and service mark of Gartner, Inc., and/or its affiliates, and is used herein with permission. All rights reserved. Gartner Peer Insights reviews constitute the subjective opinions of individual end users based on their own experiences, and do not represent the views of Gartner or its affiliates.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today