Deep Dive into the Attacks That Generated ZT and BeyondCorp
This article is the second of a series on Zero Trust.
Operation Aurora is one of the largest and most successful cyberattack campaigns against global technology and defense companies. The attack impacted at least 20 companies in addition to Google.1 Google described the attack as “a highly sophisticated and targeted attack on [Google’s] corporate infrastructure originating from China that resulted in the theft of intellectual property from Google.”1 This is the first and last time that Google has disclosed being successfully and extensively compromised by an outside attacker. The threat actor, Elderwood, was active since (at least) 2008, suggesting that Google and others may have been compromised for one to two years before detecting the attack and disclosing the breach.2
Rolling back the clock to the 2008–2013 time period, there was a general belief that while defense-in-depth was a good idea, perimeter security was enough to keep crown jewels safe. Highly effective nation-state attacks, especially those against Google (one of the best resourced corporate security teams in the world) changed that attitude. In this post we will dive into the origins of BeyondCorp and Zero Trust through the lens of Operation Aurora (aka “the Google hack”). The activities and unmatched success of the Elderwood and APT1 (Chinese) nation-state threat actors shaped the next generation of security technologies and strategies.3
From the Attacker’s Perspective
Reviewing Zero Trust and BeyondCorp from the perspective of the attackers of that time enables us to use threat activity as a guide to understand Google’s motivations for BeyondCorp and Forrester’s motivations for Zero Trust. Deeper understanding of the threat landscape helps build understanding of the strategies that are advocated as well as the tactical options defenders have to help us mitigate attacks like these in the future.
Operation Aurora
Perpetrated by Elderwood, also known as:
- The Elderwood Gang
- Elderwood Project
- Ephemeral Hydra
- Axiom
- Hidden Lynx
- Aurora
- Shell Crew
- Deputy Dog
- APT17
- Aurora Panda
- Tool/references and names (sometimes used to
describe the threat actor)
- Hikit
- Gh0st RAT
- Hydraq
- Dersubi
Public information through a variety of threat and intelligence reports from different vendors (Mandiant, FireEye, Symantec, McAfee) enables us to get a fairly clear picture of the Elderwood’s resourcing, targeting and activities.
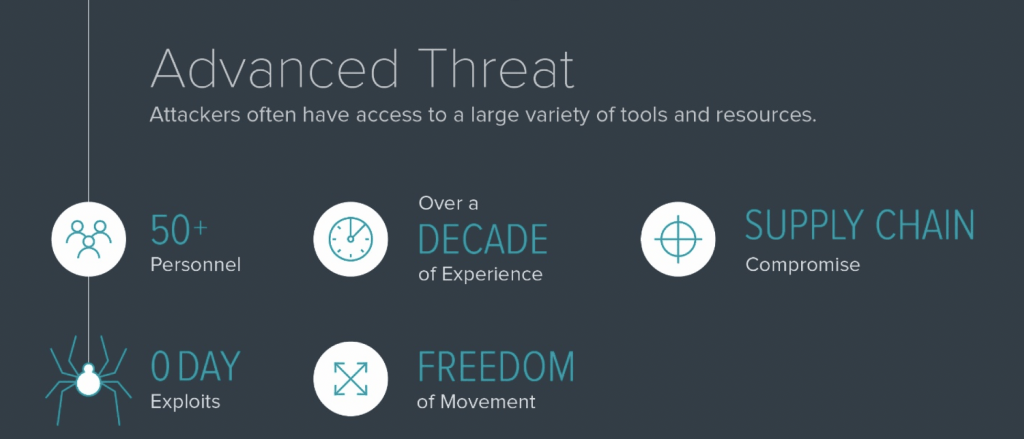
Digging into the attacks a bit deeper, the information security community have a high degree of certainty that Operation Aurora originated from China and was sponsored by the Chinese government.4 The level of tradecraft demonstrated shows that the attackers leveraged multiple teams and skill sets, and consisted of at least 50 trained personnel.4 Initial access was achieved through a variety of techniques, from mundane SQL injection attacks5 to the use of zero-day exploits delivered through email spear phishing and extensive watering hole campaigns.6 Many of the exploits are linked to ZoxPNG tool activity showing that the group and this generation of tools was active since 2008.2
With highly advanced technology and processes, a large number of people and the financial backing of a nation-state, defense against Elderwood (and its ilk) is neither trivial nor easy. Google’s updated security architecture, BeyondCorp and concepts like Zero Trust provide us a reference model and strategic framework for defense against advanced threats. It’s important to note that many companies cannot invest the time, effort and resources that Google did after their breach, so in the next article in this blog series, we’ll focus on a deep dive into how data-centric security can be effective at defending against advanced threat activity.
References
- David Drummond. “A New Approach to China.” Official Google Blog, January 12, 2010. https://googleblog.blogspot.com/2010/01/new-approach-to-china.html.
- Novetta. “ZoxPNG Analysis.” Novetta Corporation, 2014. https://www.novetta.com/wp-content/uploads/2014/11/ZoxPNG.pdf.
- Mandiant. “APT1 Exposing One of China’s Cyber Espionage Units.” Mandiant, 2013. https://nsarchive2.gwu.edu/NSAEBB/NSAEBB424/docs/Cyber-083.pdf.
- Stephen Doherty, Jozsef Gegeny, Branko Spasojevic, Jonell Baltazar. “Hidden Lynx – Professional Hackers for Hire.” Symantec Corporation, 2013. https://www.wired.com/images_blogs/threatlevel/2013/09/hidden_lynx_final.pdf.
- Brian Krebs. “Security Firm Bit9 Hacked, Used to Spread Malware.” Krebs on Security RSS, February 8, 2013. http://krebsonsecurity.com/2013/02/security-firm-bit9-hacked-used-to-spread-malware.
- Novetta Operation SMN. “Operation SMN: Axiom Threat Actor Group Report 公理队.” Novetta Corporation, 2014.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today