Security Isn’t a Fair Fight: Data-Centric Security
This article is the third of a series on Zero Trust.
In the previous post in this series, “Deep Dive into the Attacks That Generated ZT and BeyondCorp,” we talked about how highly successful attacks attributed to the Chinese government against Google and over 20 other major companies changed the game in enterprise security.1 These leveraged zero-day attacks and supply chain compromises to bypass prevention technologies and controls. Once inside of these networks, the threat actor Elderwood was able to steal intellectual property and customer data, a doomsday scenario for any network defense team. In this blog we will look at how defenders can leverage data-centric security architectures to gain advantages against advanced threats.
Not a Fair Fight
In our last post, we reviewed how nation-state attackers have more resources and better technology than defenders — the impact of this being that it is largely a question of when and not if they will be able to breach a network’s defenses. It’s important to understand how and in what ways attackers have more resources than defenders; the Symantec report on Elderwood estimates they have 2 operational teams with at least 50 trained personnel.5 Out of the gate, most small- and medium-sized business are at a disadvantage because they don’t have anywhere near 50 trained defense personnel.
Another dimension is Elderwood’s technology, where they were able to continually leverage cutting-edge technology (zero-day exploits and a custom tool stack) that was kept constantly up to date and nearly undetectable. This is in direct contrast to network defense, where most defenders are saddled with legacy technologies and limited control over business applications and information systems built by IT teams.
While Elderwood demonstrated an ability to attack third-party supply chains to affect target organizations, network defenders generally have no supply chain defenses nor an ability to interact with their security vendors. When Bit9 (a security software company now known as Carbon Black) got in the way of Elderwood’s ability to operate, they exploited the company and injected malicious code signatures into the product source, and therefore downstream into Bit9’s commercial and defense industrial base clients as well. This example shows that there really isn’t a level of trust that can be assumed by defenders in the tools they are using, and they must spend additional defensive resources to verify security (and other) software they run in their environments.
Responding to Attacker Capabilities: Establish a Logging Boundary
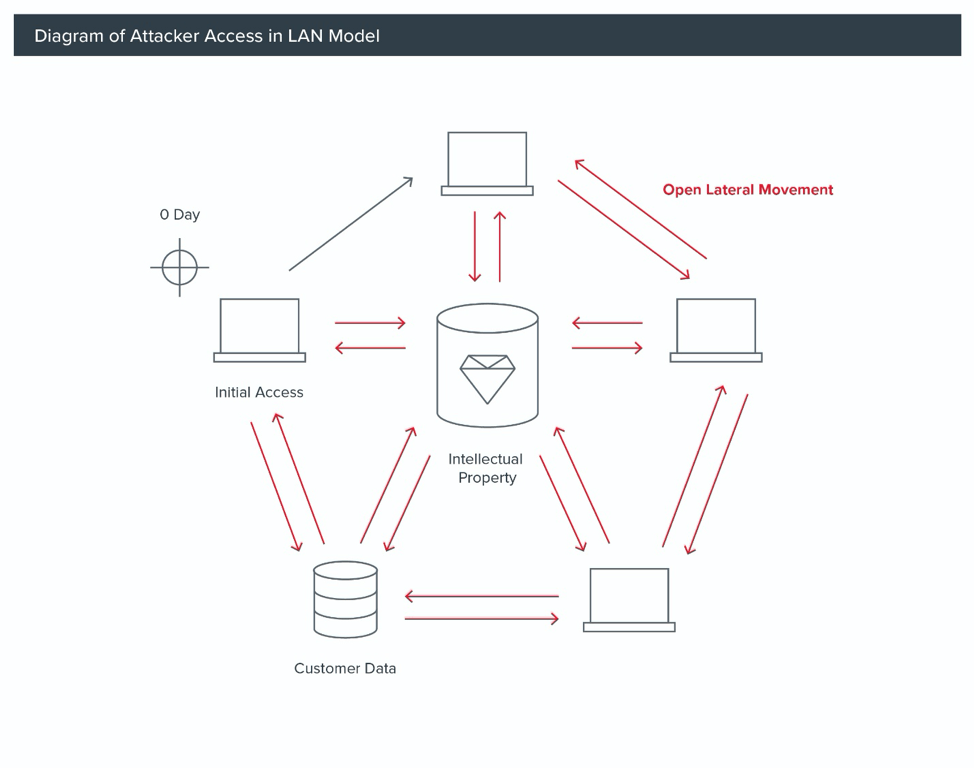
When attackers having better technology and resources, this requires defenders to shift to an “assume breach” mindset. Prior to the APT1 report and Operation Aurora, most enterprises leveraged firewalls, antivirus software and intrusion detection and prevention systems (IDS) to establish a perimeter around their entire enterprise, much like the walls of a medieval castle. More importantly, many enterprises monitored traffic at the ingress/egress points (North-South) edges of the perimeter (castle gates) but did not monitor the inside of the internal network environment (food or weapons stores within the castle). For an attacker with zero-day exploits, this kind of perimeter can be trivially breached, and with custom tool sets there is very little risk of detection by IDS/antivirus technologies. Logging and monitoring are the only effective tool that defenders can deploy to establish a clear understanding of their defensive position; they must define a defensive perimeter focused on their crown jewels.
In the face of advanced and nation-state attackers, the only real perimeter is where we can monitor — a so called “logging boundary.” Moreover, the entire network cannot be protected, so a focus on the crown jewels is critical. In the case of Operation Aurora, this was the customer data and intellectual property that Google lost.
Data-centric Security
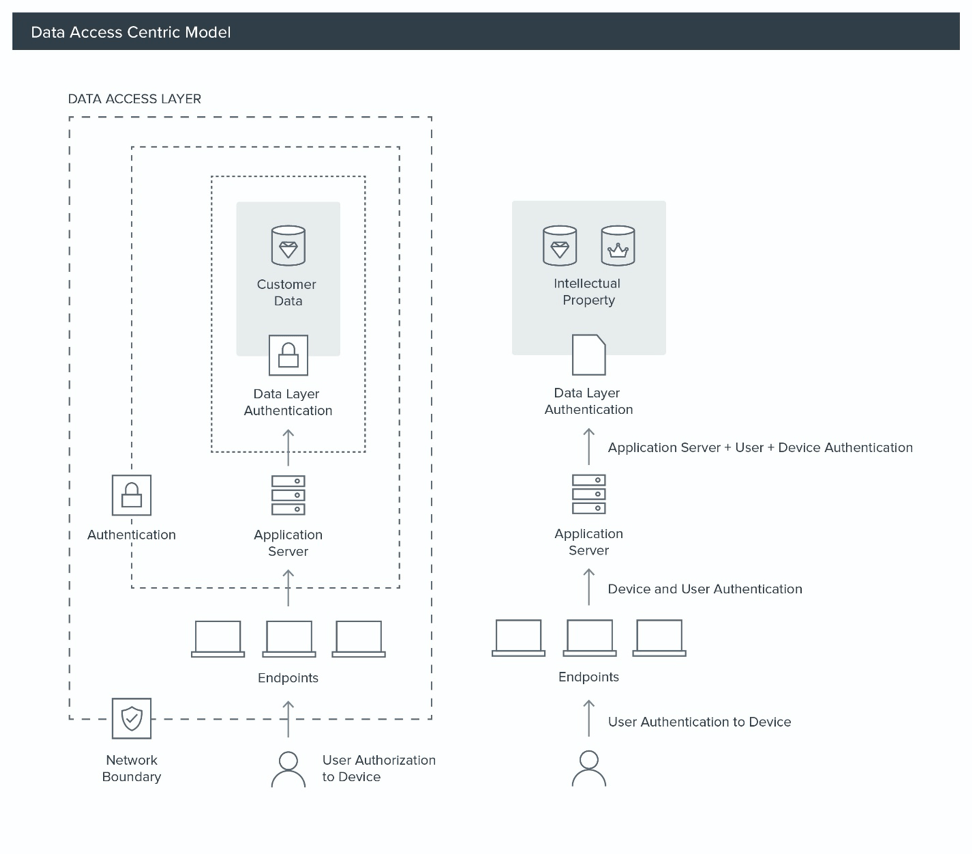
Through focusing on these crown jewels, defenders can build layered defenses from the data outward. This can be done with data access controls at the storage layer that enforce strong authentication for the data (allowing only certain users from certain locations and with other authentication factors), and centralizing authentication and monitoring data. Extending outward from the data to the applications, defenders want to make it so that only certain endpoints can communicate with the crown jewels, and slightly more can communicate with the crown jewel application servers, with a majority of endpoints (internal and external) unable to communicate with crown jewel applications or access data stores.
Data Access and Logging
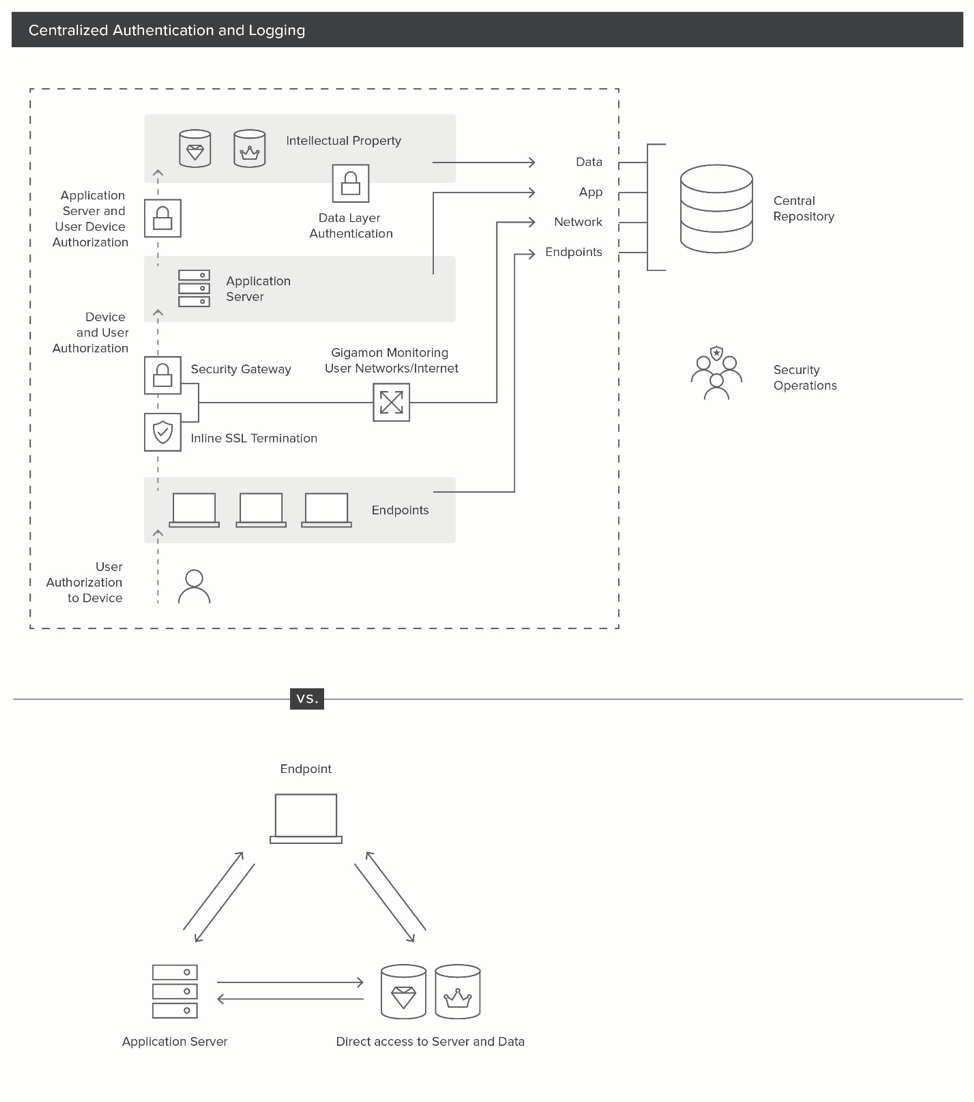
To extend the monitoring boundary, we must extend from the data access layer through the application layer, to the network access layer and ultimately to the endpoints themselves. When we look at this model, we can see that the key portions of the connection are on the endpoint and once the asset has network access/application access.
To support a data-centric security model, we need fairly extensive support to enforce controls and enable logging to rapidly detect unauthorized access to customer data and intellectual property. At the very least we need:
- Strong authentication at every layer
- Data
- Application
- Network
- Endpoint
- Centralized authentication and logging
- Application
- Network
- Endpoint
We can see that many of these concepts align with the BeyondCorp/Zero Trust model; however, they require extensive investment at the application, network and endpoint to be effective, and when not applied consistently and globally, their value is diminished.
With an understanding of Operation Aurora and its perpetrators, it’s clear to see that it’s not trivial or easy to defend against this type of advanced threat. BeyondCorp and Zero Trust provide us a reference model and strategic framework to engage many of the defensive concepts in this article. However, not many companies can invest the time, effort, and resources that Google did after their breach, so in the next article in this series, we’ll evaluate some starting points and road maps for Zero Trust and a framework for evaluating priorities and implementations.
References
- David Drummond. “A New Approach to China.” Official Google Blog, January 12, 2010. https://googleblog.blogspot.com/2010/01/new-approach-to-china.html.
- Novetta. “ZoxPNG Analysis.” Novetta Corporation, 2014. https://www.novetta.com/wp-content/uploads/2014/11/ZoxPNG.pdf.
- Mandiant. “APT1 Exposing One of China’s Cyber Espionage Units.” Mandiant, 2013. https://nsarchive2.gwu.edu/NSAEBB/NSAEBB424/docs/Cyber-083.pdf.
- Stephen Doherty, Jozsef Gegeny, Branko Spasojevic, Jonell Baltazar. “Hidden Lynx – Professional Hackers for Hire.” Symantec Corporation, 2013. https://www.wired.com/images_blogs/threatlevel/2013/09/hidden_lynx_final.pdf.
- Brian Krebs. “Security Firm Bit9 Hacked, Used to Spread Malware.” Krebs on Security RSS, February 8, 2013. http://krebsonsecurity.com/2013/02/security-firm-bit9-hacked-used-to-spread-malware.
- Novetta Operation SMN. “Operation SMN: Axiom Threat Actor Group Report 公理队.” Novetta Corporation, 2014.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today