Trust, but Verify: Detecting NotPetya Ransomware Variants in Your Network
The recent NotPetya ransomware has disrupted facilities like power grids and financial institutions across the world. Early analysis shows that it is an updated variant of the previous version of the ransomware, WannaCry.
Like WannaCry, NotPetya, too, uses the SMB (Server Message Block) vulnerability; however, unlike WannaCry, it also encrypts the host Master Boot Record (MBR). It spreads using the EternalBlue exploit. After a system reboot, the host becomes locked and denies user access. The ransomware takes advantage of the fact that SMB runs on port 445, which is usually left open for file sharing. Before the actual exploit traverses the network, it tries to open connections to TCP port 445.
How GigaSECURE Can Detect Systems on Your Network Vulnerable to This Attack
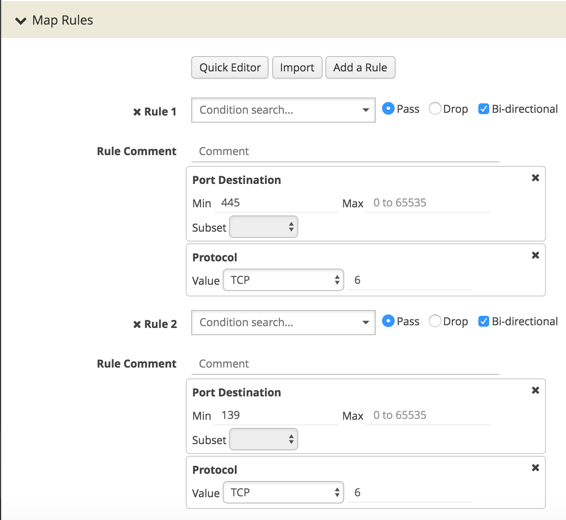
The Gigamon GigaSECURE Security Delivery Platform can help segregate SMB traffic in your network for inspection by security tools. Using GigaSECURE Flow Mapping Engine, an administrator can extract relevant flows in the network that match TCP port 445 – sending only SMB traffic to security tool(s) for inspection, thus cutting down on the noise to optimize tool performance.
Figure 1: Extracting relevant flows on TCP ports 445 and 139 for sending to security tools
Application Session Filtering
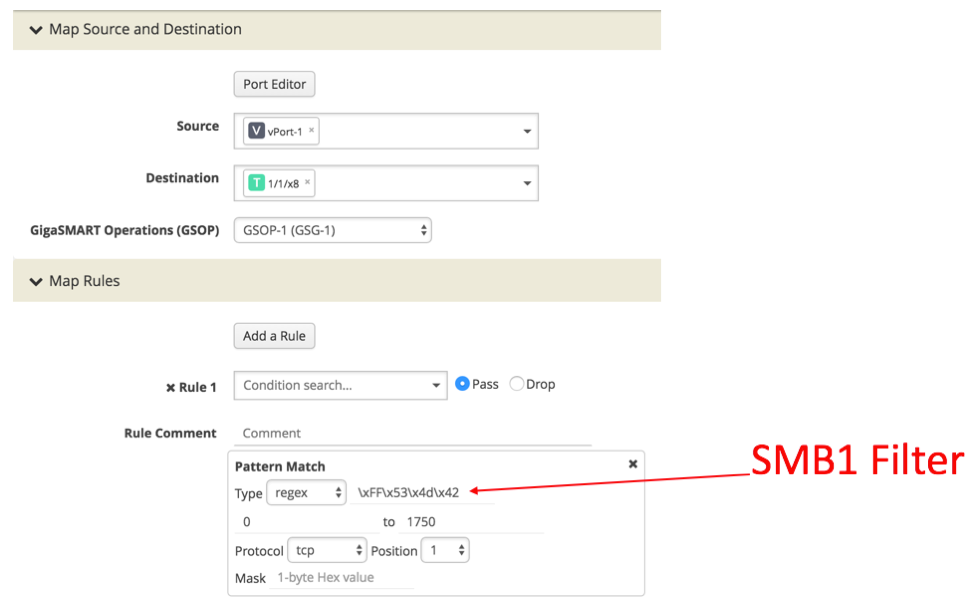
Further, Gigamon Application Session Filtering (ASF) can look for systems that are using SMBv1 and allow you to migrate to SMBv2 or isolate them until you’re able to migrate. With ASF, you can detect SMBv1 traffic by using our filtering criteria. For detecting SMBv1, the appropriate filter \xFF\x53\x4d\x42 can be used on the GigaSECURE Security Delivery Platform.
Figure 2: Filtering SMBv1 traffic for sending to security tools
Now that you’ve set this up, you will be able to detect and process any traffic matching this rule.
Remember: Trust, but verify.