NotPetya: What We Know So Far
A new global cyber attack is underway. It seems to have begun in the Ukraine and is rapidly spreading throughout Europe and Asia. It’s not WannaCry and it’s not, as originally reported, Petya either. Instead, it’s a new variant of ransomware dubbed NotPetya. And unfortunately, this attack is much more sophisticated and clever than its minimalistic moniker suggests.
https://twitter.com/nicoleperlroth/status/879746749123964928
The outbreak looks to have been initiated by means of a malicious software update for M.E.Doc, a popular accounting software package used by Ukrainian companies, with initial reports of infection surfacing the day after an update was released. Many sources, such as Cisco Talos, ESET, MalwareHunter and Kaspersky Lab, have reported and even the Ukrainian Police has tweeted that an unknown attacker likely compromised the M.E.Doc update servers and pushed a malicious software update to customers. M.E.Doc, however, vehemently denies, on both its website and Facebook page, that this is true.
Кіберполіцією попередньо установлено, що перші вірусні атаки на українські компанії могли виникнути через вразливості ПЗ M.E.doc. pic.twitter.com/MXV7ODtaoM
— Cyberpolice Ukraine (@CyberpoliceUA) June 27, 2017
Sad to Think the Term “Global Cyber Attack” Has Become a New Normal
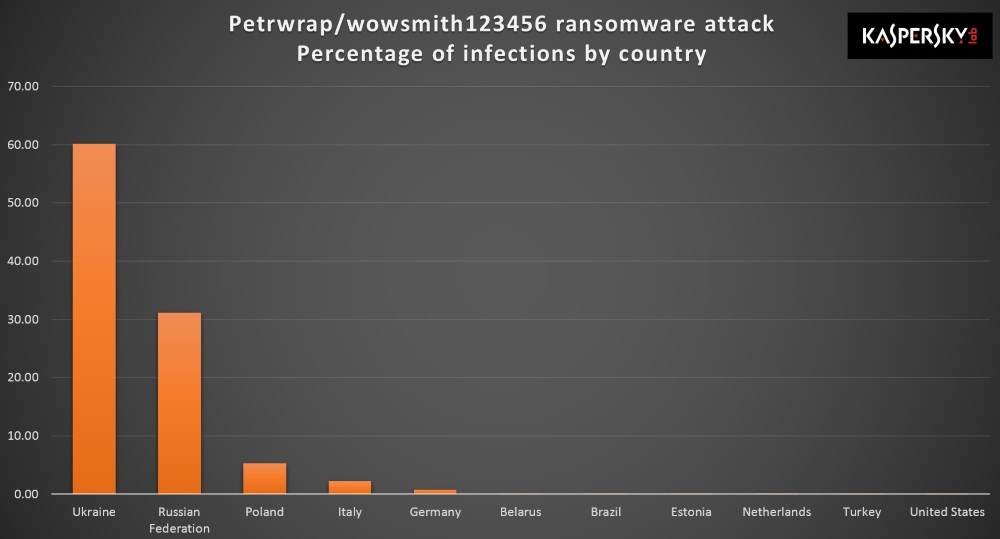
So far, the greatest concentration of victims is in the Ukraine and Russia, but once again, we’re seeing a global impact with new reports of infections in multiple countries.
While some organizations are choosing to publicly deny falling victim to the NotPetya attack, social media was full of examples of compromise today:

A tipster sends along this photo taken outside DLA Piper’s D.C. office around 10am. #Petya pic.twitter.com/HWS4UFlvQR
— Eric Geller (@ericgeller) June 27, 2017
Old Malware. New Tricks!
Unfortunately, we’re starting to see more and more attacks like this. Older malware or ransomware is being combined with a new attack vector to wreak global havoc. Petya, for example, has been around for over a year in the wild, but was primarily delivered via phishing attacks, which substantially limited its ability to spread.
This new variant is leveraging similar exploits to those used by WannaCry, only these authors were much more thorough with their work and included a few additional tricks, such as adding the EternalRomance exploit – a remote code execution exploit targeting Windows XP to Windows 2008 systems over TCP port 445. No doubt, these modifications help account for the rapid and global infection rate.
So, How Does NotPetya Work?
Much like WannaCry, NotPetya leverages the ExternalBlue exploit from the Shadow Brokers’ dump in April. Of course, everyone should have patched their systems against this back in March when Microsoft released Security Bulletin MS17-010, but what makes this attack unique is that it also has a backup proliferation mechanism for spreading within a network.
The NotPetya payload includes the ability to look for cached usernames and password credentials in memory and use them, via WMI/WMIC and PSEXEC, to move laterally to access other network systems. If the malware is lucky enough to capture privileged credentials, it can spread easily and rapidly to additional systems, even those that have been patched against the EternalBlue exploit.
Unlike WannaCry, a single exposed and infected system on a network can provide a means for NotPetya to infiltrate a network and move laterally to infect all other systems via WMI or PSEXEC. This makes it a far nastier threat than WannaCry.
Once NotPetya Infects a System
NotPetya appears to wait about 10 mins after the infection takes place before it reboots the system. This delay is likely intended to avoid malware sandbox detection. Once it reboots, it begins to encrypt the MFT table on NTFS partitions, effectively making the system unresponsive and at which point it delivers the ransom note demanding $300 in Bitcoin.
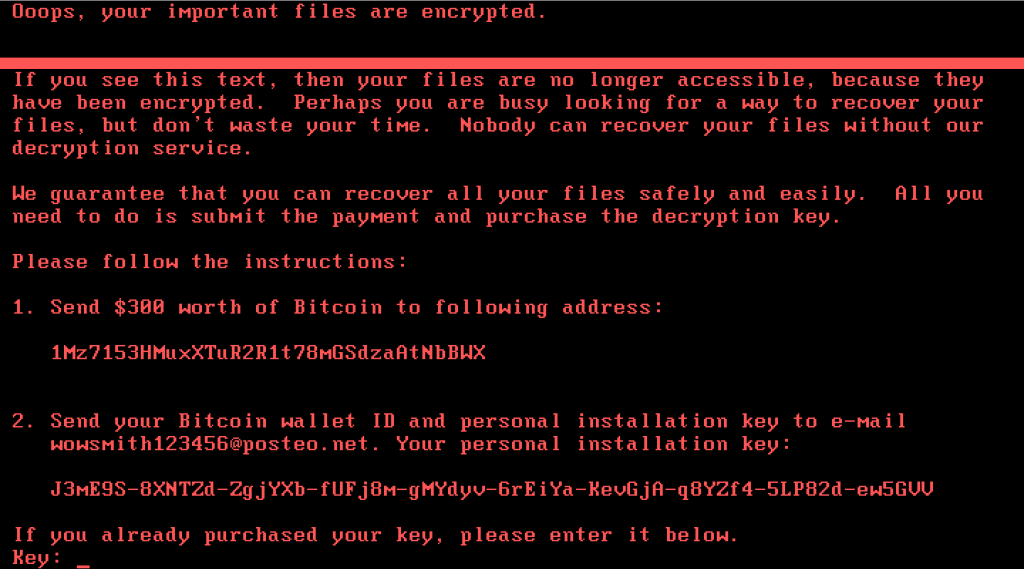
The attack then looks to propagate to other systems by scanning the network for potential infection targets. While doing this, the malware attempts to harvest user names and passwords from logged-in users to spread the attack via valid network credentials. This is extremely devious and surprisingly clever as once it is running wild on your network, it can propagate to systems that would have been impervious to the initial attack
What’s the Big Deal about NotPetya?
Let’s be clear, the WannaCry attack is not over by a longshot, with systems around the world still getting hit and infected every day. Now coming on its heels though is NotPetya, the second major global attack in less than a month that’s been fueled by exploits dumped by the Shadow Brokers and allegedly stolen from the NSA.
Why is this so frightening? My biggest concern about this attack is that it further demonstrates that cybercriminals now have access to intelligence-agency-level exploits and they are actively innovating their attack methods to include these exploits with increasing success. It is the cyber equivalent of handing out weapons of mass destruction to every professional and wannabe cybercriminal on the planet and letting them hack and modify them at will. Increasingly, we’re seeing the weaponization of attacks leveraging these exploits with escalating levels of sophistication and damage.
What Should Affected Users Do?
WannaCry’s kill switch was a design flaw, but counting on hacker ineptness isn’t really a sustainable security strategy. Patching your systems, however, is certainly a good start! No seriously … why are all of these systems still not patched after WannaCry? It boggles the mind and drives those of us in the cybersecurity profession nuts.
For those wondering, is there any hope for users to decrypt their files? Sorry (I’m Canadian), but probably not. These attackers seem to be coding pros and have used a solid encryption scheme. So unless someone finds a flaw in the code to develop a decryption method, victims may be out of luck.
The Attackers May Be Excellent Coders, but They’re Lousy Criminals
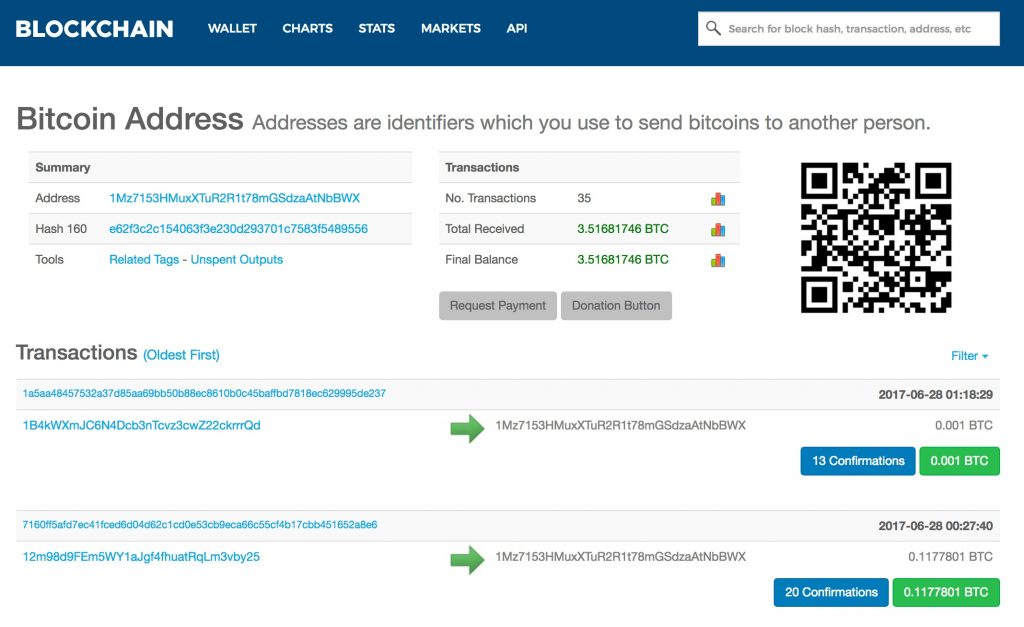
Most sophisticated ransomware attacks create a unique wallet for each individual infection. This makes it easy to track which victim has paid the ransom. NotPetya, however, is requiring each victim to send their $300 payment to a single Bitcoin wallet. The problem with this process is that having a single Bitcoin payment method will make it much easier for law enforcement to monitor the wallet should the attackers wish to withdraw their loot.
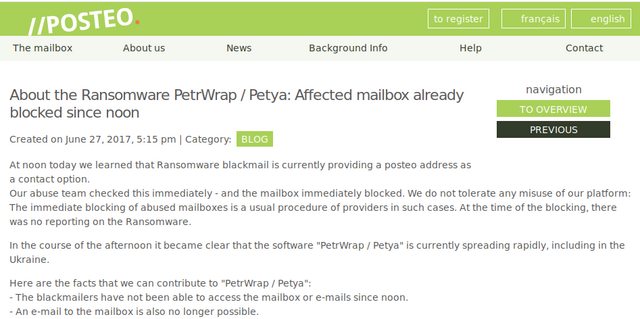
The next head scratcher is that the attackers ask victims to confirm payment by sending their wallet number via email to [email protected]. The problem with a single method of communication like this is that Posteo, the email provider who was hosting the attackers’ email account, has reportedly shut it down, which effectively, makes it impossible for the attackers to confirm payment and, unfortunately, for the ransom-paying victims to receive decryption keys.
This entire payment process is beyond puzzling, it’s downright stupid. Why would these people go to all of the trouble of creating a highly-sophisticated attack like this and not devise a better way to cash out?
At this point (June 27th, 11pm EST), the attackers have received 35 payments totaling 3.51681746 in Bitcoin, the equivalent of a mere $8862.38 USD.
Here’s the Bitcoin address: https://blockchain.info/address/1Mz7153HMuxXTuR2R1t78mGSdzaAtNbBWX
Like with WannaCry, how is it that a prolific, noisy attack with global impact just can’t seem to generate a significant profit? It makes me wonder what the real motivation behind these attacks is and if there is a more nefarious and long-term purpose other than simply making money.
A quick aside: It’s rumored that companies are beginning to stockpile Bitcoin and other cryptocurrencies in case they need to pay ransoms to unlock critical systems. If this is true, we are clearly moving into uncharted territory socially, economically and legally when it comes to the future of ransomware attacks.
How Can You Defend Against These Attacks in the Future?
Let’s start by reviewing this timeline:
- March: Microsoft releases a patch for an SMB exploit.
- April: The Shadow Brokers release an exploit dump that includes EternalBlue, which exploits the same SMB vulnerability Microsoft patched in March.
- May: #WannaCry hits and makes significant noise globally.
- June: Systems are still getting hit with WannaCry and now NotPetya is using the same exploit because people and organizations have yet to patch their systems.
We need to start applying a grown-up level of attention span to these attacks. When WannaCry hit, it was supposed to be a global wakeup call where consumers and users would finally understand the importance of cybersecurity … until a 22-year-old kid, uh, I mean, cyber-superhero found and activated the kill switch and everyone breathed a sigh of relief, and then basically did nothing.
So, what can you do to defend against these attacks in the future? To start, if you haven’t already, please stop what you’re doing right now and go patch everything!
Once your systems are updated, a next step to consider is incorporating a visibility-based security posture. With complete visibility over your network that the Gigamon GigaSECURE Security Delivery Platform provides, you can assess vulnerabilities, protect weak points and start to build better defenses by managing traffic across your extended network and getting the right information to the right security tools so they can better detect and rapidly respond to ransomware attacks like WannaCry and NotPetya.
For more information, please read Using GigaSECURE to Detect WannaCry Infected Hosts in Your Network.








