Using GigaSECURE to Detect WannaCry Infected Hosts in Your Network
Updated October 14, 2021.
On Friday May 12, a major ransomware attack affected many organizations across the world, including big names like Telefonica in Spain, the National Health Service in the UK, and FedEx in the US. The malware responsible is a ransomware variant known as WannaCry.
In this blog, we will examine how organizations can use Gigamon’s GigaSECURE Security Delivery Platform to spot the WannaCry ransomware in their network and take steps to mitigate it.
How WannaCry Works
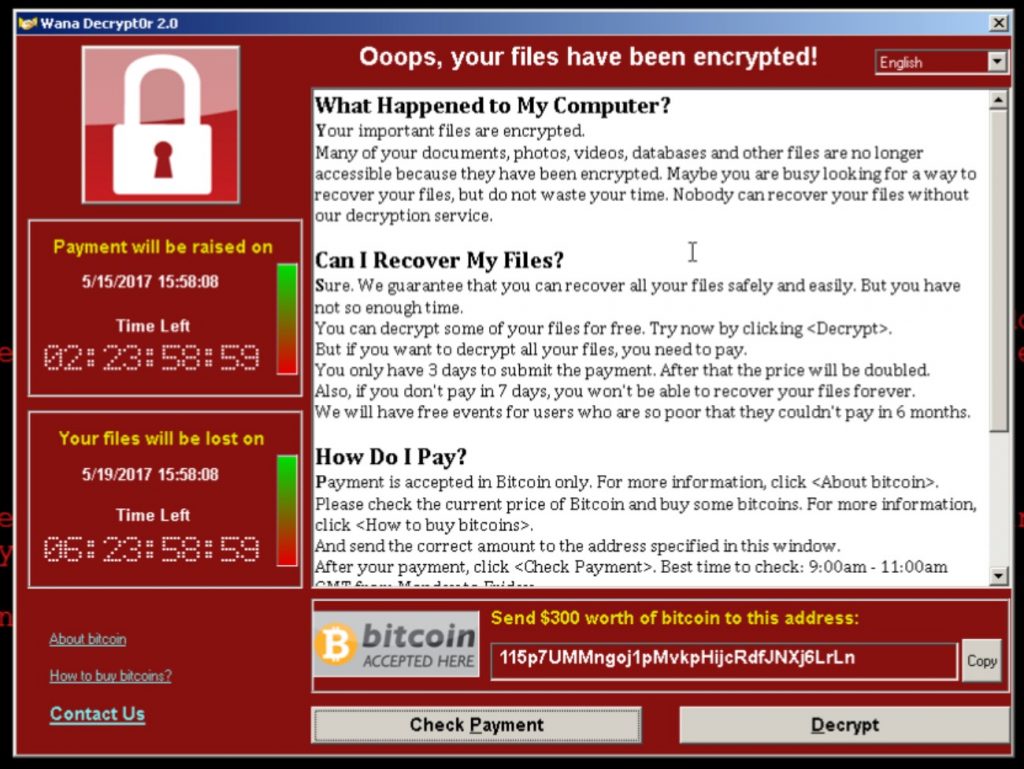
The WannaCry malware typically enters an organization’s network using a phishing or drive-by Web download. Once in, it uses Microsoft’s Server Message Block (SMB) protocol to start scanning the network file shares and removable storage devices, after which it encrypts these files. With encryption complete, it then displays to the victim a pop-up containing a ransomware note. Upon receipt of the ransom, the criminals promise to provide the decryption key that can then be used to unlock and recover the files in the victim computer.
Figure 1: A sample WannaCry pop-up dialog (courtesy of Forbes)
Just as with a real-life kidnapping involving a ransom, payment is no guarantee that the kidnapped person or, in this case, your data will be recovered.
Using GigaSECURE to Detect and Mitigate WannaCry
The WannaCry malware has been known to exhibit two forms of network behavior.
First, when the victim’s computer tries to access the network file shares, it uses the Microsoft SMB protocol, which uses TCP ports 139 and 445.
Second, some WannaCry variants include a “kill switch” routine where upon execution of the malware for the first time on the host, it attempts to establish a connection to the domain http[:]//www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com. While newer variants have stopped using this domain, it is still worthwhile looking for this domain as well as other kill switch domains observed to have been used by the malware.
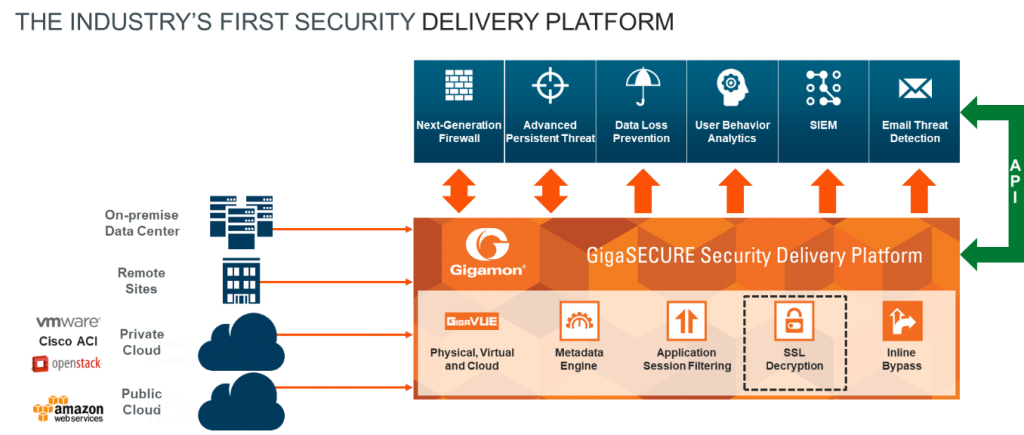
The GigaSECURE Security Delivery Platform—designed to provide pervasive reach across the infrastructure, spanning cloud, on-premise data centers/locations, and remote sites—has an arsenal of functions to help spot these network behaviors. Specifically, security appliances simply connect into the GigaSECURE platform to receive a high-fidelity stream of relevant traffic and metadata from anywhere in the network infrastructure. Advanced filters in GigaSECURE can be used by a security administrator to quickly spot malicious network activity in the infrastructure.
Figure 2: GigaSECURE Security Delivery Platform
Contextual Information Improves Analysis to Find Threats Faster
Let’s now look at the specific GigaSECURE functions that can help narrow down the WannaCry attack.
As the majority of organizations refocus their network security efforts on the insider threat and compromise detection, NetFlow (IPFIX) becomes a rich and important source of contextual information about the traffic, helping augment analysis in order to determine where compromise has occurred.
The GigaSECURE platform can furnish a complete picture of the network at line rate, including all packets and their NetFlow records without loss. A typical NetFlow record reveals traffic source and destination as well as protocol or application, time stamps, and number of packets.
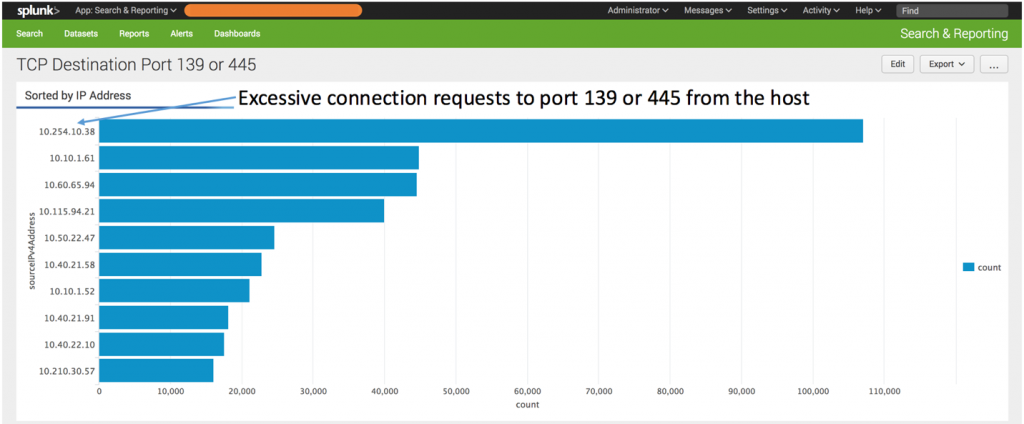
By generating NetFlow for the entire network and examining the output either in a Security Information and Event Management (SIEM) system such as Splunk Enterprise or a NetFlow analyzer such as Cisco StealthWatch or Plixer Scrutinizer, one can spot hosts connecting to TCP ports 139 and 445. The usual number of legitimate SMB accesses from a network host should be fairly small. If the number climbs much higher than the normal threshold, one could suspect that these hosts have been infected by the WannaCry ransomware and they should be taken off the network or placed in quarantine. Further, if any of these SMB connections happen to be initiated from the Internet to internal hosts, that should be doubly suspicious.
Figure 3: Observing SMB scans using Gigamon Netflow in Splunk Enterprise
Drill down into URL and DNS Metadata to Discover Offending Hosts
The WannaCry malware has a hardcoded kill switch. If the malware makes a request to this domain name (just as if it were looking up any website) and the request comes back and shows that the domain is live, the kill switch takes effect and the malware stops spreading.
Gigamon has enhanced NetFlow into a full-blown Metadata Engine that sits inside the GigaSECURE platform and provides information about DNS, HTTP URLs, HTTP response codes and SSL certificate activity in the network. Gigamon has extended the NetFlow (IPFIX) format by adding private extensions to capture the URL information embedded in HTTP connections along with DNS and certificate information.
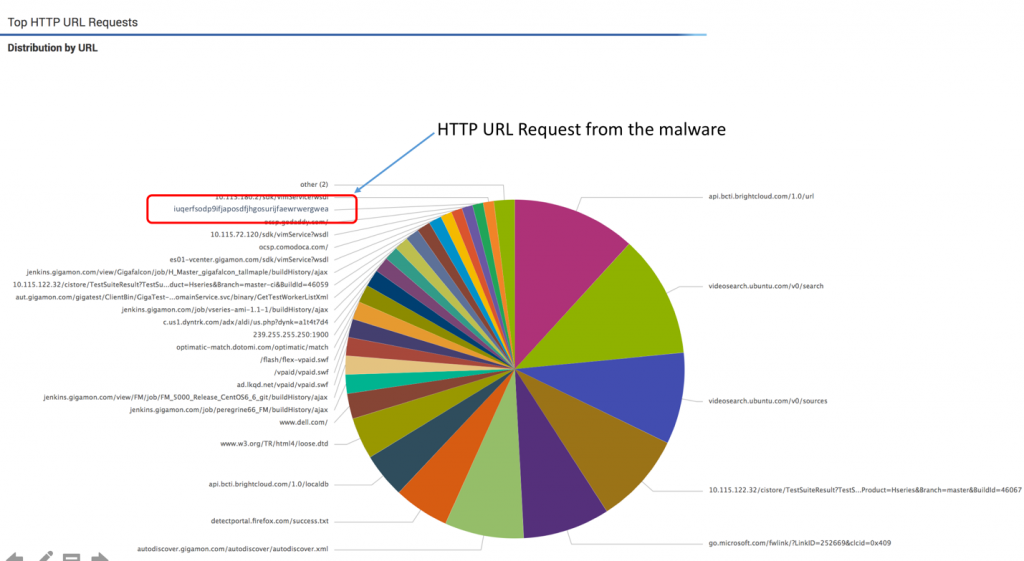
These URLs can be extracted from the network and fed to a SIEM. Using functions such as entropy provided by Splunk Enterprise, it’s possible to see if these URLs are machine-generated or unusually long and abnormal. One can then drill down into these unusual URLs and discover the offending hosts that are connecting to them. Alternately, an administrator can set up an alert to fire up whenever any host tries to access this domain.
Figure 4: Observing URLS in Splunk Enteprise using Gigamon’s HTTP metadata
Prior to creating a Web request to the domain, the infected host will try to initiate a DNS request to resolve the IP address for the domain http[:]//www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com. This resolution is expected to fail, but capturing the DNS request would provide clues to the offending host. Unlike using DNS server-based logs (which cannot handle recursive DNS lookups and taxes the DNS server performance), this method provides precise identification of the infected host. That is, so long as traffic reaching each of the DNS servers in the network is fed to the GigaSECURE platform.
Finding Patterns and Uncovering Clues within Network Noise
Every security device wants to look at relevant traffic.
Unfortunately, relevant traffic that may contain clues to malware activity is oftentimes lost in the overall noise of the network. Using Gigamon’s Flow Mapping Engine, one can extract relevant flows, which match TCP ports 445 and 139, and send essentially all SMB traffic to the security tool. With the subset of traffic to SMB narrowed, the security administrator can then write scripts to sift through this data set to identify normal and abnormal connections.
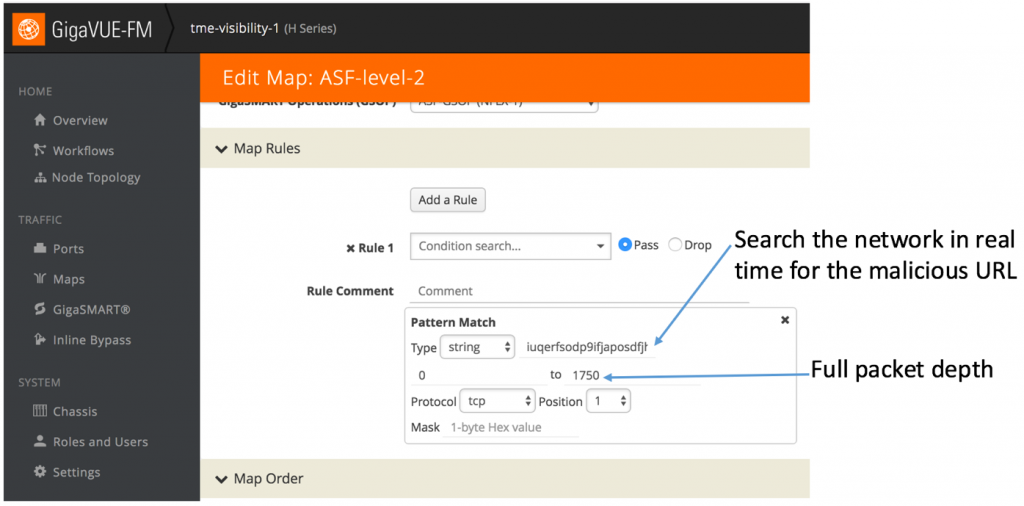
Application Session Filtering (ASF) is another GigaSECURE function that can be used to monitor for this ransomware. Simply put, ASF acts like a Google Search on network traffic and extracts the entire TCP/UDP stream even if a single packet in that stream contains a signature of interest. ASF provides a powerful filtering engine that identifies applications based on patterns that can appear across any part of the packet payload. These patterns can be as simple as a static string at a user-configured offset or as complex as an advanced Regular Expression (regex) at a variable offset.
With ASF, one can simply search the entire network traffic for multiple patterns. For the WannaCry ransomware, an administrator can program the ASF engine to search for transactions that have the domain “http[:]//www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com” (see figure below). Furthermore, if the malware writers were to keep changing the domains used for the kill switch patterns, one can immediately start monitoring the new patterns by programming them into the ASF engine.
Figure 5: Looking for patterns in TCP traffic using Gigamon’s Application Session Filtering
For more questions on how the GigaSECURE platform can assist your organization to detect malware activity such as WannaCry in your infrastructure, please contact your Gigamon sales team or authorized Gigamon channel partner.