Scaling Security and Network Visibility
“May you live in interesting times.” No, I’m not referring to any sort of curse. On the contrary, I’m referring to network transformation; never before has networking and network visibility gone through more interesting times. The old approach to network visibility was simple. As the network grew, all you had to do was to add network management tools, application performance management tools and security appliances. Life was good.
But network are like living organisms. They grow. They evolve. They change.
The old approach of adding more tools and security appliances has become too cumbersome and costly. Networks have grown faster, and in many ways they exceed the capabilities than the tools to monitor and appliances to secure them. The result – network blind spots and dark corners where the unknown occurs. And hence, the visibility gap was created.
Without question, with any modern network today, there is a visibility gap. Tools can only scale so much and security appliances can only be dropped into so many network segments. This visibility gap is what keeps security administrators and network architects up at night. They ask, “how do you secure what you can’t see,” or “how can I make my security investments more efficient, strategic and scalable?”
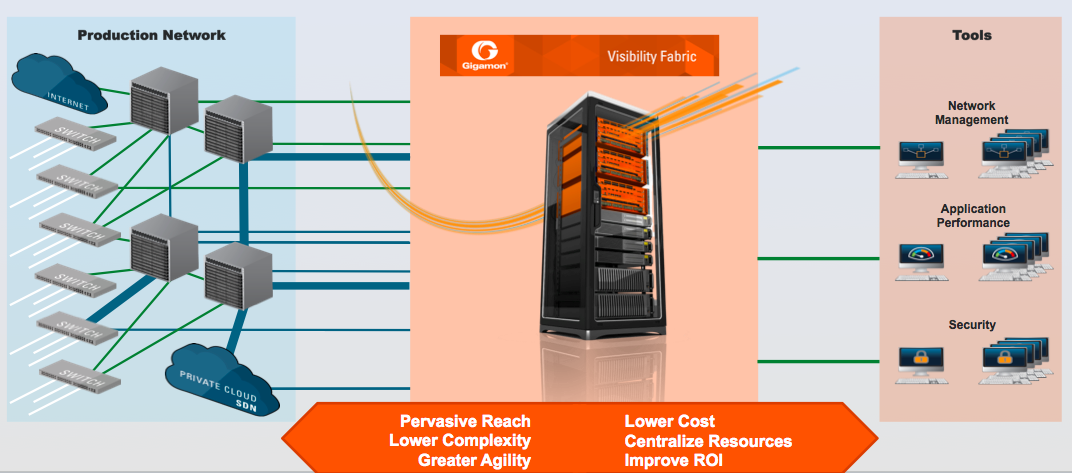
That’s where a Visibility Fabric comes into play. For today’s next-generation networks, the secret to maintaining high performance and security lies in how a Visibility Fabric connects and illuminates network traffic. It fills the gap between network sprawl and the tools that manage and secure the network.
With a Visibility Fabric in place, fewer tools and appliances can do the job more efficiently and effectively because the Visibility Fabric does the heavy lifting by performing packet aggregation and filtering the right traffic to the right tool. The Visibility Fabric modifies and transforms packets to optimize tool functionality and security capability.
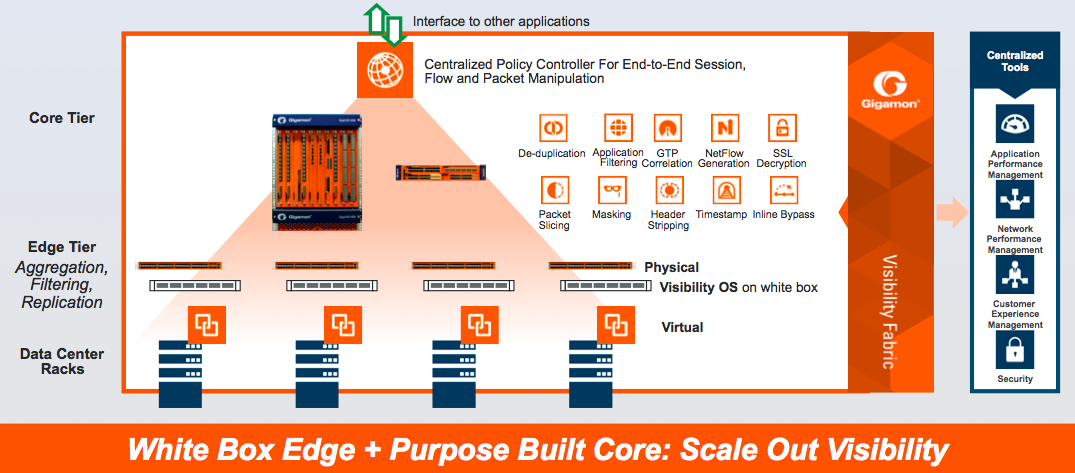
And as threats increase and become more sophisticated, and as network architectures change with SDN and virtualization, the need for visibility increases. To help solve this challenge, visibility nodes can be strategically deployed among virtual, edge and core locations. The software that powers these nodes, GigaVUE-OS, is what creates the Visibility Fabric, allowing for centralized for end-to-end session, flow and packet manipulation.
However, for large data centers and carrier networks, large-scale hardware deployment of visibility nodes may be cost prohibitive. For this reason, Gigamon decoupled its OS so that approved white box switches can function in the same capacity as any other type of visibility node, which enables the creation of a fully featured Visibility Fabric. This gives architects and admins the freedom to pick and choose the right visibility framework for their network, and as their network grows, so too can their Visibility Fabric.
These are interesting times. Network transformation may appear to be a daunting, if not a dangerous challenge, but with Gigamon’s Visibility Fabric and white box solutions, no network is too big, too dynamic or too interesting to not have pervasive visibility.