Five Top Concerns in Private Cloud Visibility
Are You Really Seeing All Your East-West Traffic?
For many years, security professionals and spending have been focused on the network perimeter. The perimeter and endpoints have been hardened to keep the bad guys out. And that’s been the right thing to do, but now that most organizations have achieved reasonable levels of perimeter and endpoint security, they are turning their focus to what’s happening on their private cloud networks.
Why? Because industry statistics consistently show that many network threats (56 percent1) are due to insider behavior, whether malicious or unintentional, resulting in 90 percent2 of organizations feeling exposed to insider threats. And with insider breaches costing three times as much as outsider breaches at an average of $16.2 million,3 these threats come at a heavy cost.
Many organizations assume that they know what’s happening on their private cloud network — after all, it’s their private cloud network, running their applications and workloads, managed by their tools. But in practice, this is not always the case. Gigamon helps secure and manage some of the largest and most sophisticated private clouds in the government and commercial sectors. This blog will look at five of the top concerns we hear from these customers as we help them secure and manage their private clouds.
#1. Are You Really Seeing Everything in Your Private Cloud?
The tools that come built into your private cloud platform, and the third-party security and observability tools that you’ve added, are good as far as they go. The key question is whether they go far enough to give you what you need to detect patterns of user, asset, or network behavior that indicate an attack or breach has occurred and to identify as precisely and quickly as possible the nature and extent of the problem.
For example, tools that rely on MELT (metrics, events, logs, and traces) don’t see what’s happening at the network level of your private cloud. In fact, event- and log-based security tools such as SIEMs may not see up to 96 percent of the East-West (lateral) movements on your network,4 leaving one of your primary security tools blind to much of what is happening. The Gigamon Deep Observability Pipeline works with your SIEM and all your security tools but adds the ability to see what’s happening down to the network packet level. This provides the complete visibility essential to detecting, identifying, and remediating security issues and troubleshooting availability, performance, and customer experience problems.
#2. How Do You Secure Ephemeral VMs and Containers?
Most organizations are committed to using VMs and containers to scale their applications. Using orchestration and automation mechanisms, new VMs and containers are spun up for minutes, seconds, even microseconds, then disappear just as quickly. But these time windows are more than long enough for sophisticated malware to detect a vulnerability and potentially use a VM or container to access a high-value asset that can be ransomed or exfiltrated.
#3. Do You Have Visibility into Your Encrypted Traffic?
Encryption is a powerful technology that most organizations use extensively to safeguard both data in motion and data at rest on their private clouds. However, encryption is a double-edged sword. Just as it’s a powerful tool for NetOps and SecOps, it’s also a powerful tool for attackers who use it to set up encryption to hide their presence on a network and, for example, set up encrypted tunnels that allow them to navigate the network — undetected — as they seek out high-value data targets.
Gigamon has been delivering inline and out-of-band decryption solutions for a decade. We deliver our solution as a decentralized service that removes the burden of decryption from your tools, enabling them to focus on the primary function. Additionally, in 2023, we went back to the drawing board to rethink the real-world problems created by key-based decryption solutions and launched our unique PrecryptionTM technology. Using Precryption, Gigamon opens secure tunnels within your private network to pipe plaintext data between applications and alleviate the overhead of encryption/decryption in many situations.
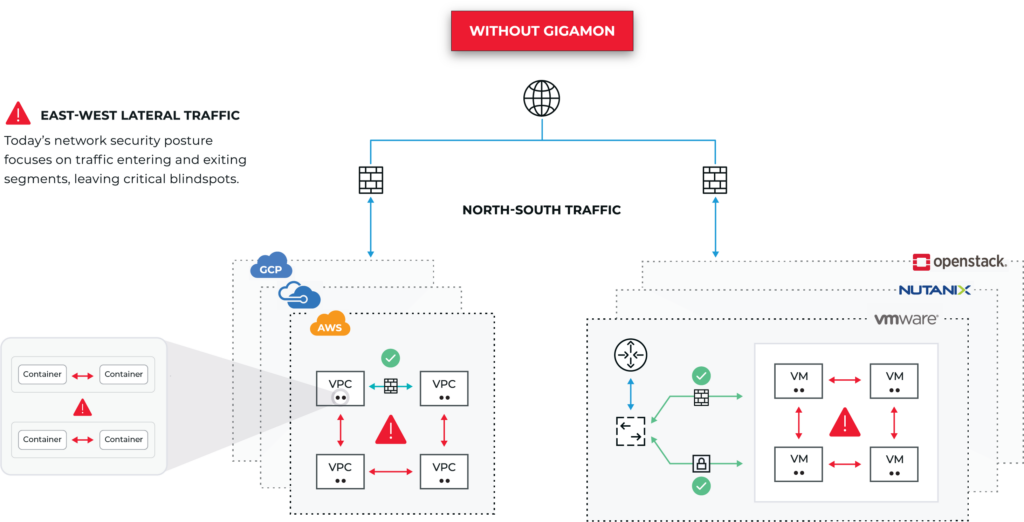
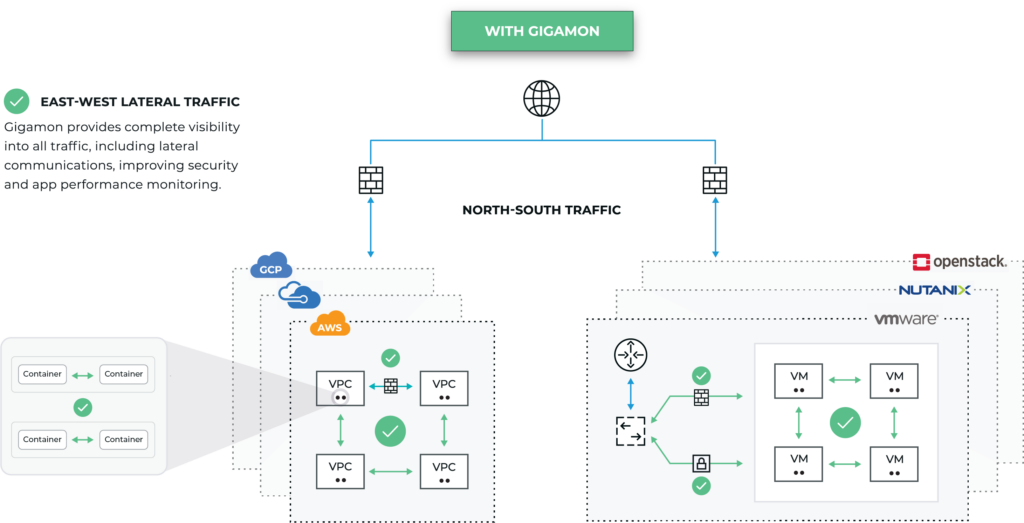
#4. Are Your Tools Showing You as Much as You Think?
Today’s security, observability, and performance management tools do a very good job of meeting their intended purposes. But times and situations change, and increasingly well-resourced, motivated, and agile attackers are poised to take advantage of these changes. New examples — indeed, new classes — of AI-powered malware are being launched with alarming frequency, perpetuating the attacker’s advantage and leaving your organization more exposed.
To combat these threats, you need to have all your tools working together to correlate all the data they are seeing individually so you can detect and identify anomalous behavior at the user, application, or network level in real time and, in many cases, preempt an attack. The Gigamon Deep Observability Pipeline does exactly that. We ensure that all your tools are seeing exactly — and only — the data they need to see to operate at the highest level. We also deliver network-derived metadata intelligence to these tools that correlates and provides context and meaning these tools might otherwise miss.
#5. Can You Get a Comprehensive, Consistent View of All Private Cloud Activity?
The old cliché “You can’t secure what you can’t see” is a cliché for a reason — because it’s true. In the world of private cloud security with multiple private cloud instances, ephemeral VMs and containers, and encrypted data, this is truer than ever before. Although individual tools can give you some of the visibility you need, what you really need is to consolidate your visibility data into a single window, so when security or performance events occur, you have a single point from which SecOps and NetOps teams can respond.
As we observed previously, bottom-up visibility needs to be added from the network level, and this is delivered using the GigaVUE-FM fabric manager. This is an essential component of the Gigamon Deep Observability Pipeline and provides a single user interface into all the servers, applications, and dataflows on your private cloud network. With this level of visibility, you can quickly and easily see exactly what’s happening on your network, enabling you to, for example, add new tools into data flows to provide additional visibility and protection.
Although this blog is focused on private cloud networks, Gigamon provides this same set of comprehensive capabilities across on-premises, public cloud, hybrid cloud, and multi-cloud infrastructures. To learn more about how we can help you secure the private cloud or any aspect of your infrastructure, visit the Gigamon Private Cloud Information Hub.
Citations:
1., 2. Top 18 Cybersecurity Statistics for 2024 That May Make You Question Your Online Safety. 2024. SMSCountry. https://www.smscountry.com/blog/cybersecurity-statistics
3. Cost of a Data Breach Report 2023. 2023. IBM. https://www.ibm.com/reports/data-breach
4.The Blue Report 2023. 2023. Picus Security. https://www.picussecurity.com/resource/report/blue-report-2023
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today








