Gigamon Guide: Advanced Network-Centric Techniques for Early CL0P C2 Detection
Whether you’re a current Gigamon customer or responsible for cybersecurity, you’ll want to know about the new CL0P ransomware gang exploits as reported by CISA and Unit42 of Palo Alto Networks. We highly encourage you to read both sources for background and technical information on CL0P tactics, techniques, and procedures (TTPs).
This guide demonstrates how you can use Gigamon Application Metadata Intelligence (AMI) to not only detect known CL0P techniques but also other threat actors’ TTPs that are often overlooked with traditional measures. Our intent is to provide a best practices guide Gigamon customers and others can use to monitor and detect some of the known techniques common to many threat actors that are otherwise difficult to detect with classic logging methods.
Gigamon is uniquely situated in networks to broadly see lateral traffic, and AMI offers deep packet inspection of known and unknown applications and protocols on both known and unknown ports. These capabilities provide the depth of observability that customers require to secure multi-cloud deployments.
Setting the Stage
As with most data breaches, the CL0P exploit is the tip of the spear. To use an exploit, the threat actor must get within striking range and then piggyback on standard applications and protocols baked into workloads for stealthiness and lateral movement. Based on the data size and torrent sites, it’s clear that CL0P had significant dwell time within networks and was able to move laterally without detection. BitTorrents or torrents are a distributed data file sharing protocol that can transport large data over high speeds via public networks.
The Role of AMI
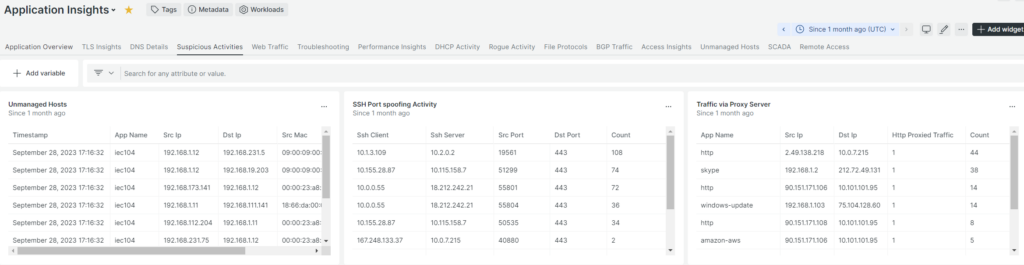
Organizations using the Gigamon Deep Observability Pipeline with AMI are well positioned to detect this kind of lateral movement through visibility within their networks. AMI extracts Layer 4–7 application and protocol metadata through deep packet inspection. Screenshots below are on Splunk, Dynatrace, and New Relic, but you can use any observability SIEM tool to ingest and analyze the metadata.
We will cover known observed techniques, and then help you detect those on your network. These are best practices for a network-centric security posture for hygiene, which Gigamon makes much easier. Note that these recommendations may change as more information becomes available.
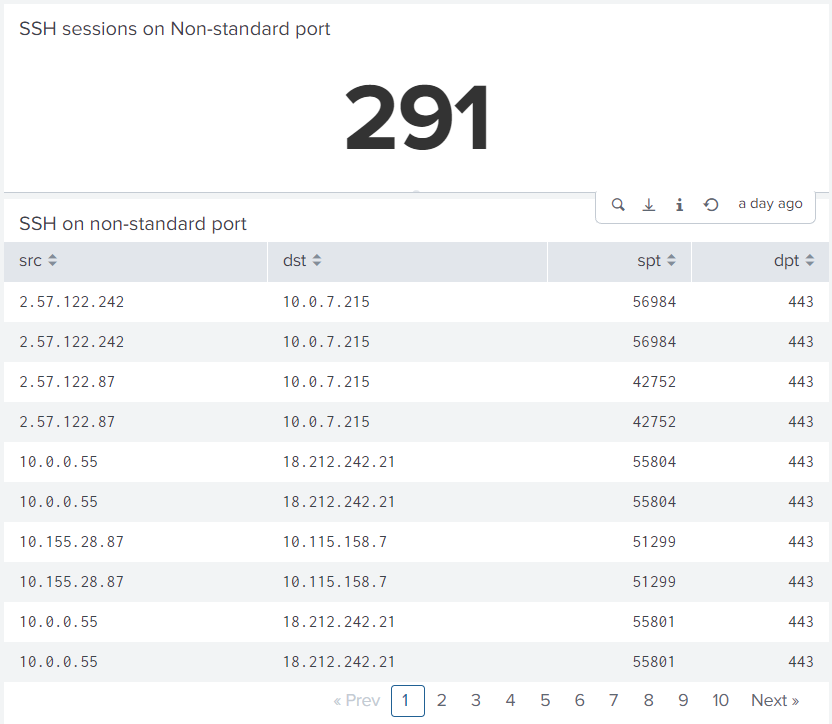
I. Non-standard port traffic (port spoofing)
- Use of SSH (Secure Shell) traffic on non-standard ports
- A command-and-control server was seen briefly running SSH 8423 and port 123
- It is a reasonable assumption that SSH was used laterally to:
- Navigate networks
- Locate targets
- Use the MOVEit exploit
- Stage data for exfiltration
II. vsftp (Very Secure FTP) traffic
- vsftp/FTP was likely used to stage the data internally and exfiltrate the data
- vsftp was used to exfiltrate data to external staging locations
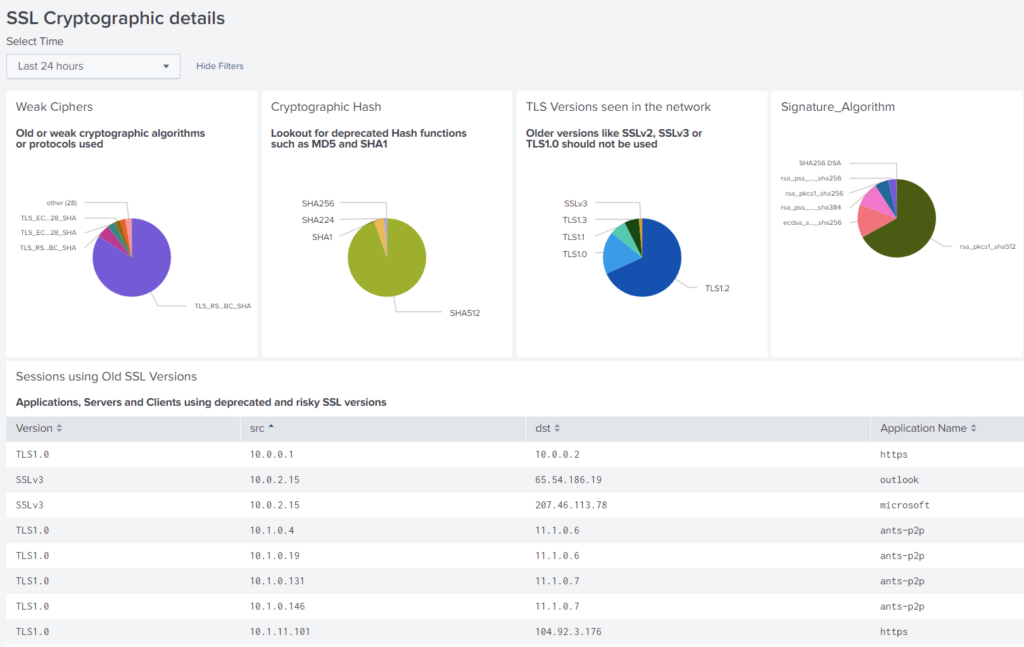
III. Self-signed certificates
- vsftp was seen using self-signed TLS certificates
- Self-signed certs included:
- Certs containing *.example.ru
- Certs under three months old
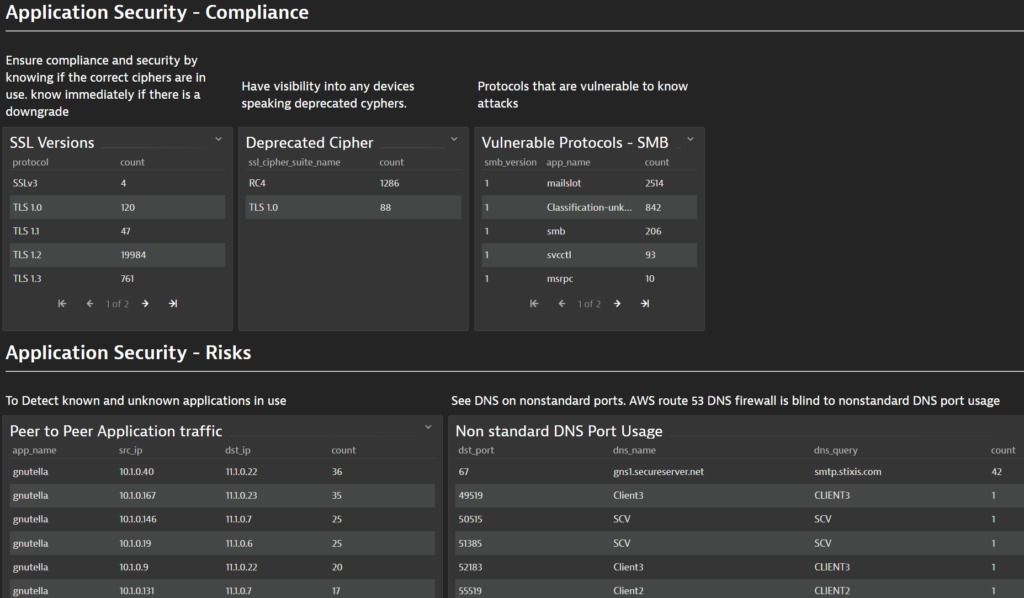
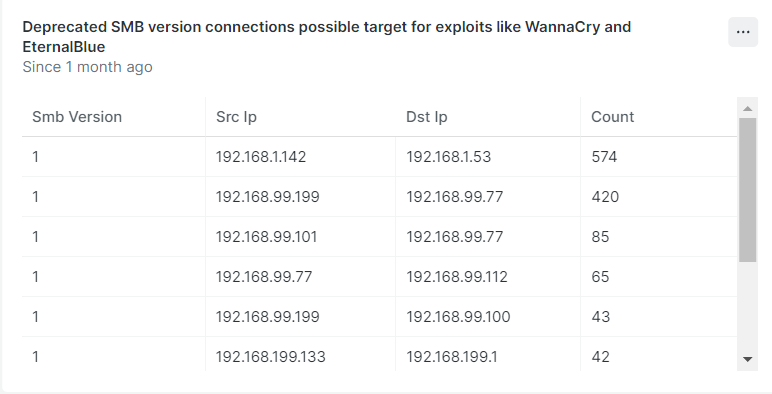
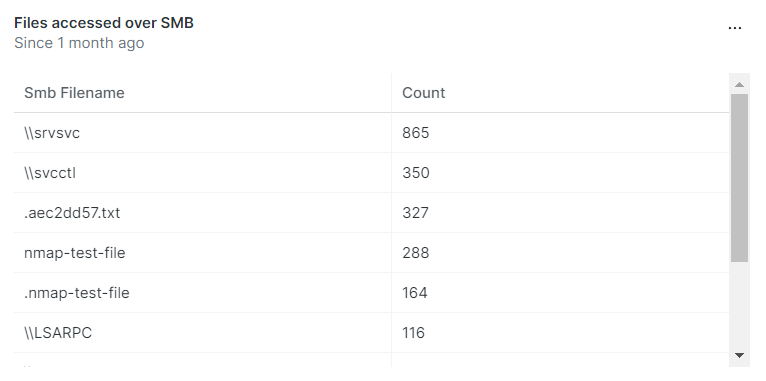
IV. Use of deprecated SMB
Compromising AD servers using SMB (Server Message Block). CISA had reported that AD servers running vulnerable versions of SMB are attacked with Cobalt Strike to gain access.
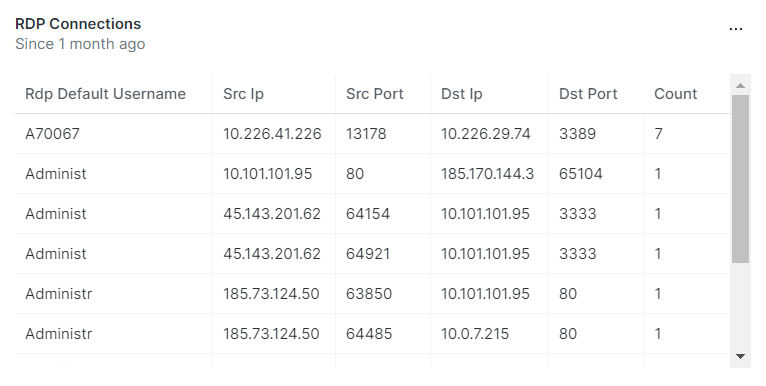
V. Remote Desktop Protocol (RDP) traffic
Using RDP to interact with compromised systems. CISA states that remote desktop is used to control compromised systems.
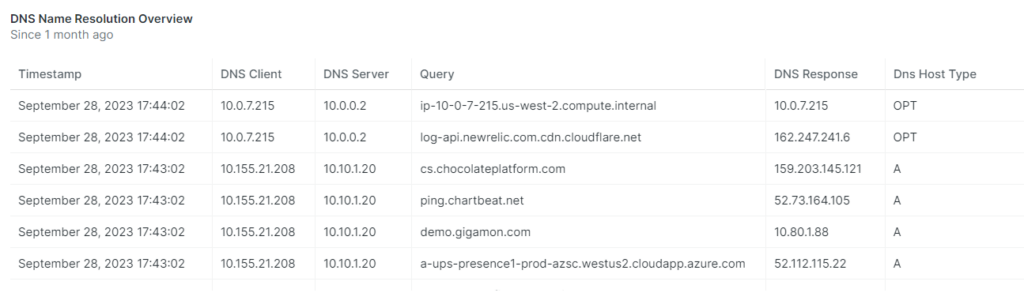
VI. Domain Name System (DNS) queries
DNS lookups to malicious domains. CISA lists several malicious domains as being part of initial malware drop sites. These serve as indicators of compromise.
Gigamon Recommendations
Based on current information, Gigamon recommends our customers turn on the Application Metadata Intelligence detection and look for the following:
- vsftp and secure FTP detections enabled; vsftp would be seen as a TLS connection on port 21
- FTP and vsftp traffic on ports other than 20 and 21, respectively
- Secure Shell (SSH) on any non-standard port both outbound and laterally
- Self-signed certificates
- Certificates containing *.example.ru
- Unknown or unclassified data on ports 20, 21, 22, 443
- TLS traffic on non-standard ports
- DNS lookups to known compromised domains on known and unknown ports
- Remote desktop connections inbound, outbound, and on non-standard ports
- Use of older SMB versions, such as v1 and v2
- Use of weak and deprecated ciphers, such as RC4
- Use of older Transport Layer Security (TLS) versions, such as TLS 1.1, 1.0, and any version of Secure Socket Layer (SSL)
In general, it’s best practice to monitor any non-standard port usage, which is something AMI is uniquely positioned to solve for. Gigamon provides the option to select over 7,000 metadata attributes through our GigaVUE-FM software.
In Closing
Although tactics and techniques are evolving, the most recent attack was observed using torrents for high-speed distribution after the data had been exfiltrated because of the data’s size. In the past, onion routing was the preferred method, but the exfiltrated data was too large for this to be practical. Gigamon has robust torrent detection that can provide an added layer of visibility.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.