Solidify Your Security Posture with Visibility into Virtual Machines and Containers
News stories about cybersecurity breaches are always tough reminders of the importance of having a complete security posture. One day, we hear how a widely used food delivery service was breached, resulting in customer personal information, delivery addresses, and partial payment information being stolen. (DoorDash, 2022: 4.9 million customers were affected.) Another day, we hear about how a public school district was breached, resulting in the compromise of student names, dates of birth, class schedules, and course assessment scores. (Chicago Public Schools, 2022: 550K students and staff were affected.) Regardless of the scale of the breach, reading these announcements never fails to make us ponder if our institution and personal details will be next.
Security postures are hard to orchestrate, given the many variables involved in keeping an infrastructure secure from attackers. It’s an extremely difficult challenge to manage — and one that needs constant modernization as new attack methods are presented in the threat landscape. But at the core of every effective security posture is visibility.
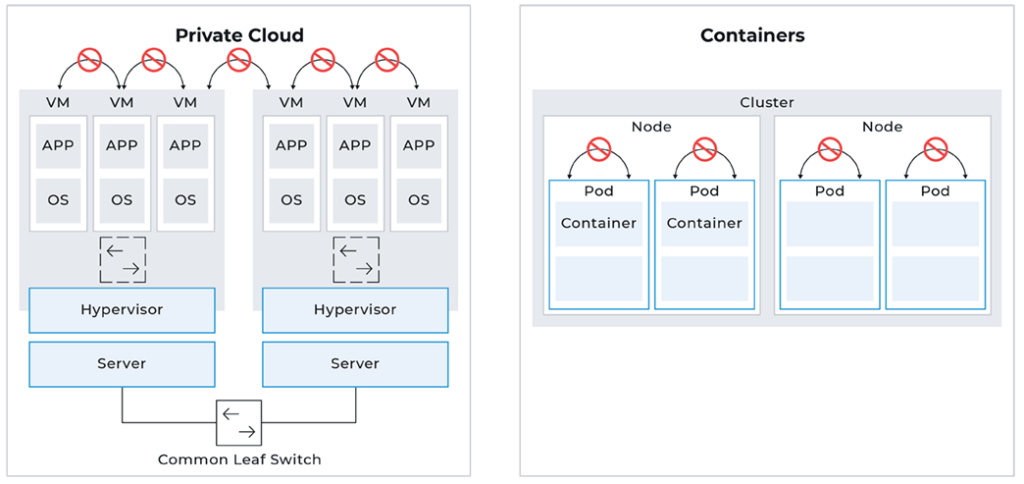
Visibility without blind spots is foundational to all security postures and is a necessity to limit the opportunities for attackers to go completely undetected. This coverage goes past the visibility at the perimeter you get from a firewall and includes the East-West traffic (lateral movement) communicating between virtual machines (VMs) and between containers.
The Importance of Virtual Machine and Container Visibility
Visibility into lateral movement between VMs and between containers is often overlooked. Why would an organization need visibility into this East-West traffic? It’s important for a variety of important reasons, such as:
- Security: VMs and containers are potential targets for cyberattacks and create blind spots for all organizations that do not have complete visibility into this East-West traffic. By gaining visibility between VMs and between containers, organizations can identify potential security threats in these areas and take proactive measures to address these risks.
- Performance: Application performance is directly impacted by the efficiency of VMs and containers, and it’s important for organizations to be able to monitor and optimize performance across these environments. Organizations can leverage visibility into this East-West traffic to efficiently pinpoint performance bottlenecks and take measures toward optimizing application performance.
- Resource management: VMs and containers both consume a significant amount of resources, including CPU, memory, and storage. Visibility between VMs and between containers ensures organizations use resources efficiently and effectively.
- Compliance: Many organizations are subject to regulatory compliance requirements that mandate specific security practices. Organizations can ensure they are meeting requirements and avoid costly penalties for noncompliance by eliminating these blind spots.
Visibility without blind spots is essential for any security posture. But the benefits of having complete visibility extend past security to also support performance monitoring and compliance.
Gaining VM and Container Visibility Is a Challenge
Organizations face two main challenges when trying to gain visibility into the East-West traffic communicating between VMs and between containers: a lack of unified tools for end-to-end visibility and the sheer number of VMs and containers.
VMs and containers are distinct environments that each have their own unique architectures, management tools, and monitoring systems. Each environment is managed via a stack of tools native to that environment. Because of this, end-to-end visibility into the lateral movement between VMs and between containers can be hard to access since each environment is siloed.
As organizations scale their infrastructure to meet current business needs, the challenge of managing the sheer number of VMs and containers is always present. With the rise of virtualization and containerization, organizations can now spin up hundreds or even thousands of VMs and containers in a matter of minutes. This makes securing and monitoring VMs and containers a nightmare because it’s so easy to spin up and down a VM or container.
How Organizations Can Gain VM and Container Visibility
- Leverage the Gigamon Deep Observability Pipeline: Gigamon provides organizations visibility into the East-West traffic across their entire infrastructure, including on-premises, areas between VMs, the public cloud, and areas between containers, by accessing the intelligence needed and feeding it to all tools simultaneously through a centralized orchestration
- Use container orchestration platforms: Platforms like Kubernetes have native mirroring capabilities that can provide visibility into the traffic between containers
- Deploy monitoring tools: Monitoring tools like Prometheus, Grafana, and Datadog can be used to provide metrics on CPU usage, memory usage, disk I/O, and network traffic based on the intelligence provided to them by Gigamon or native mirroring capabilities
- Implement logging and tracing: By collecting logs and traces, organizations can analyze application performance, detect anomalies, and troubleshoot issues
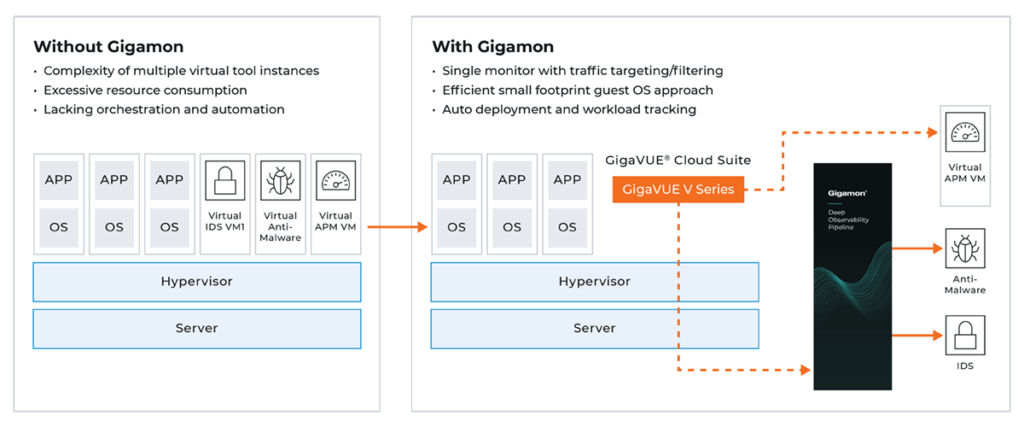
Gaining complete visibility for our security postures is a challenge for the many reasons listed above. But we must all take the initiative to gain complete visibility across everything — including between VMs and between containers — for the sake of keeping our infrastructures secure and functioning at an optimal level. As we continue modernizing our security and monitoring postures, may we all put visibility first and response strategies second.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today