Doing More With Less, Part 1: The Network Security Opportunity
If you’re concerned about getting the maximum security coverage possible in the face of budget constraints, then this blog post is for you. At Gigamon we frequently hear from customers who want to see “all of the data” — an understandable desire given the possibility that something may slip through unnoticed. In fact, Gigamon provides such full fidelity by eliminating blind spots such as in encrypted and virtual traffic (more on that below).
The fact is, however, few organizations have the budget they’d like for all of the security tools — including ingestion costs in some case — and security experts needed to analyze all traffic all the time. The reality is that a portion of this traffic is irrelevant (like duplicate packets) or may be from lower-risk applications. In addition, this irrelevant traffic is essentially excessive network noise, which can slow down teams in pinpointing security or network issues.
And, as experience with Gigamon customers shows, you don’t need to see all traffic. That is, not all traffic needs to be analyzed all the time — but you do need to analyze all of the vulnerable traffic all the time. Within that distinction lies opportunity for 1) a stronger security posture within 2) limited budgets and 3) the possibility of saving money down the road.
This post examines how a new Tool Efficiency Wizard can help you to establish a plan on how to maximize security tool effectiveness within budget constraints. Two of our featured methods are:
- Reduce noise to pinpoint network and security issues faster
- Eliminate security blind spots
Note that the first relies on optimizing traffic flowing to security tools using techniques like packet de-duplication, flow mapping, and application filtering. The second is about visibility to all data-in-motion, regardless of medium.
Reduce Noise to Pinpoint Network and Security Issues Faster
For SecOps teams, excessive noise is the distraction that can lead to failure. Noise causes security teams to expend precious time chasing down false positives. It bogs down security tools with floods of irrelevant data — all of which must be analyzed no matter the importance.
According to research by the Public University of Navarre,1 for example, duplicate packets represent more than 50 percent of network traffic. In other words, from the start nearly half of all network traffic is irrelevant noise.
Instead, the goal should be to reduce network noise to provide tools only the data they need and reduce the false positives that plague SecOps teams. Security issues can be identified earlier, with fewer false-positive alerts.
Using the Network Tool Efficiency Wizard, you can get more insights on how to reduce noise in traffic to optimize your tools with only the essential data they need.
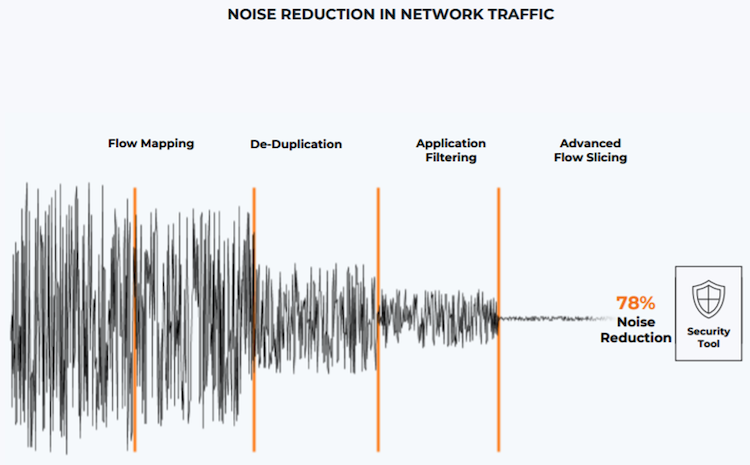
The chart below illustrates that Gigamon Flow Mapping, De-Duplication, Application Filtering, and Advanced Flow Slicing work successively to significantly reduce irrelevant data to your tools.
To learn more about the importance of visibility and security in a hybrid cloud world, we also recommend reading this report by Omdia as an important learning opportunity about this and other topics.
How to Eliminate Security Blind Spots
As mentioned above, another major impediment for security teams are network blind spots. Why are network blind spots so detrimental? It’s simple: You cannot secure what you cannot see. Furthermore, blind spots make it difficult, if not impossible, to effectively troubleshoot performance and availability problems.
For example, network security tools are often configured to ignore encrypted East-West traffic, even though encrypted traffic comprises the bulk of traffic inside the network. Yet Gigamon’s Annual Review of Corporate North-South and East-West Traffic report states that 65 percent of all internal traffic is encrypted.
Also mentioned above, eliminating blind spots does not mean sending all traffic to your security tools. Instead, you want to send all relevant traffic — including encrypted, East-West, and virtual traffic — to tools while eliminating irrelevant traffic.
Again, the Tool Efficiency Wizard offers important insights.
Are You Ready to Increase Your Tool Efficiency?
Getting your network and security tools, and associated spend, evaluated with the Tool Efficiency Wizard is the first step for your NetOps and SecOps teams to maximize your security posture within your budget constraints.
Check out this three-minute video to see a breakdown of the Tool Efficiency Wizard’s customized report:
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today
1 Úcar, Iñaki, Daniel Morato, Eduardo Magaña, Mikel Izal. 2013. “Duplicate detection methodology for IP network traffic analysis.” Conference paper, IEEE International Workshop on Measurements and Networking Proceedings, October 2013. https://www.researchgate.net/publication/258519875_Duplicate_detection_methodology_for_IP_network_traffic_analysis.