Gigamon Guide: Advanced Techniques to Detect App Traffic Behavior, Including SolarWinds, in Your Network
We released this blog last week on Gigamon methodologies to uncover traffic that may need additional scrutiny by security and monitoring tools. Subsequently, we have had requests for a similar guide that focused on SolarWinds traffic monitoring, which we are providing here.
However, we need to remind readers that supply-chain compromise attacks are likely to become more prevalent as we move forward and this is not focused on SolarWinds. Gigamon believes that a quickly deployable tactical capability to detect and triage issues like this is a valuable tool in an increasingly hostile threat landscape.
With Gigamon IT’s permission and support, we set up an isolated environment where we were able to inspect SolarWinds traffic and behavior. Based on that analysis, we’ve created the following guideline to detect “plain” SolarWinds traffic, as well as ways to detect “residual” indicators based on traffic and application metadata. This will identify activity generated by SolarWinds-related assets in your infrastructure, should they start communicating in the coming weeks and months.
Our intent is to provide a best-practices template that Gigamon customers can deploy to monitor all network traffic and detect any SolarWinds-related traffic, should it appear in the future. We are aware of at least one situation where IT was surprised to see SolarWinds running in part of their network that was not being actively monitored.
The goal of this guide is to help customers build a “mental model for situational awareness” and use Gigamon as another layer of detection to complement existing security tools and use Gigamon deep packet inspection to help shed light that other tools may not cover well.
Questions we can help you answer:
- Is there any SolarWinds traffic on your network today?
- If yes, what kinds of DNS activities does it generate?
- How are SSL/TLS certificates being used?
- How can you use Kerberos information for this purpose?
Note: For this guide we are using the Splunk SIEM for historical analysis, but other analytical tool can be used, including open-source ones.
I. Plain SolarWinds Traffic
Let’s start by detecting plain SolarWinds-related communications, such as SolarWinds client-to-management UI usage or monitoring agent communications.
A) To isolate SolarWinds Orion traffic, look at its designated TCP ports: 17775 to 17799.
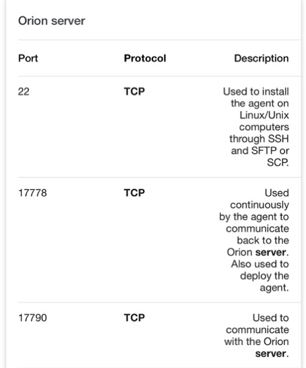
In this case we are sending that traffic to our FortiGate tool, in addition to Riverbed.
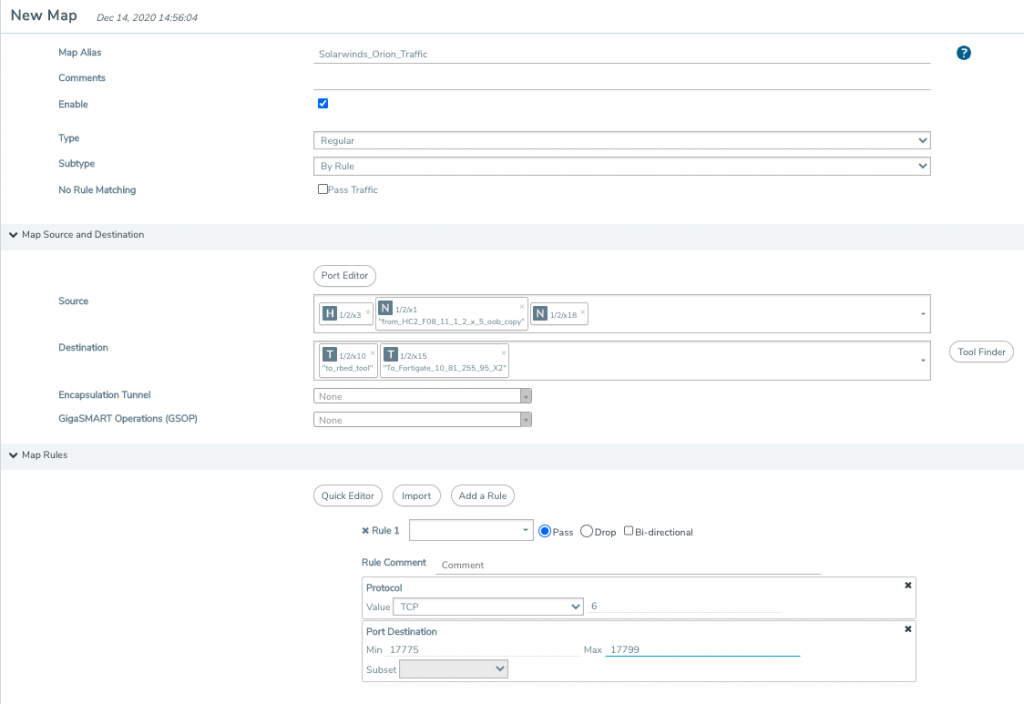
B) Next, use Gigamon Application Filtering Intelligence to identify SolarWinds traffic traversing over non-standard TCP ports. After identifying that traffic, you can apply a similar flow map to monitor that traffic, should it appear in the future.
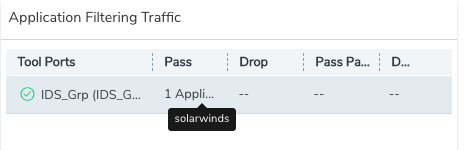
After that you should see SolarWinds traffic in your tools:
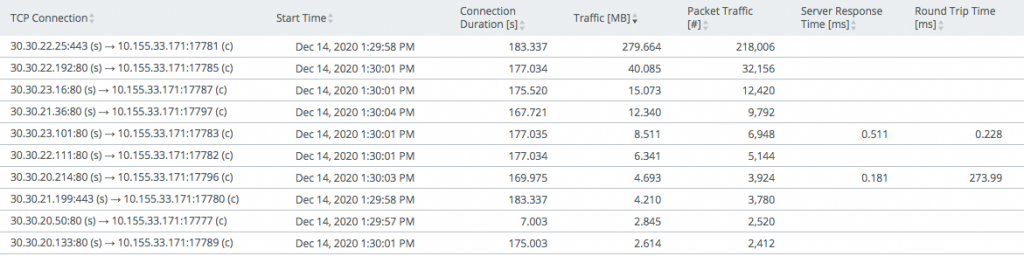
II. Scrutinizing DNS Traffic
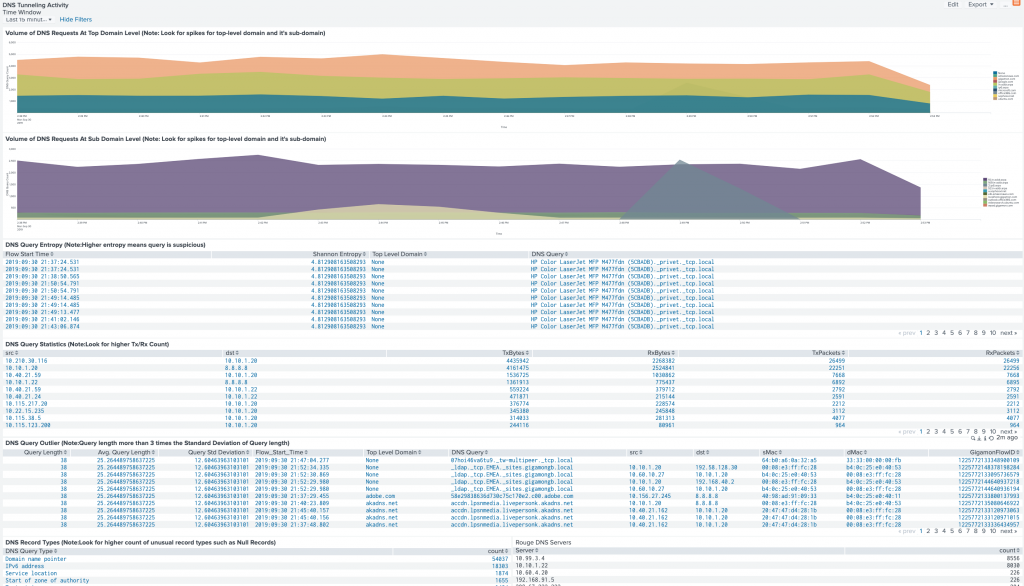
The first step towards scrutinizing DNS traffic is to identify DNS activities to look for future compromised server names or outlier DNS activities. For example, hosts on your enterprise network should be using only enterprise DNS servers, and attempts to use others should be considered an issue requiring urgent investigation, even if you’ve blocked DNS traffic at the firewall.
A) Use Gigamon Application Intelligence to see DNS traffic and to extract metadata from that traffic using deep packet inspection.
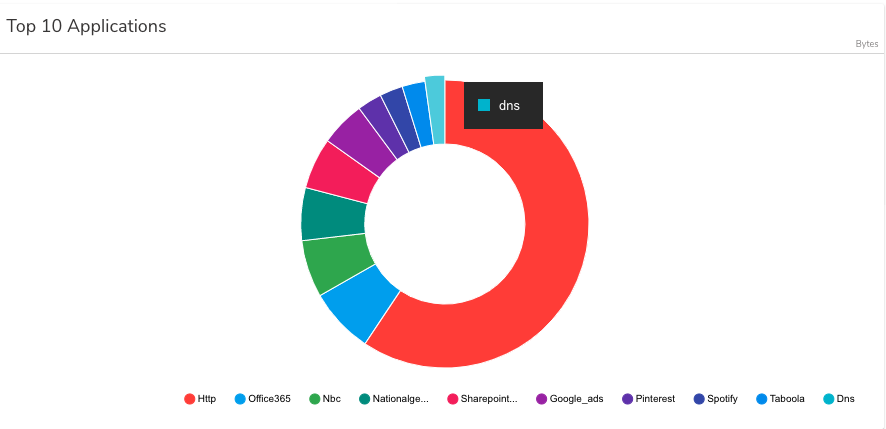
B) Keeping tabs on DNS entropy
As you probably know, inspecting DNS traffic can help identify C2 communications and DNS tunneling by looking for things like high-volume DNS queries, large DNS-query length and high-entropy domains.
First, here is the list of Gigamon Application Metadata Intelligence attributes to send DNS logs to your SIEM:
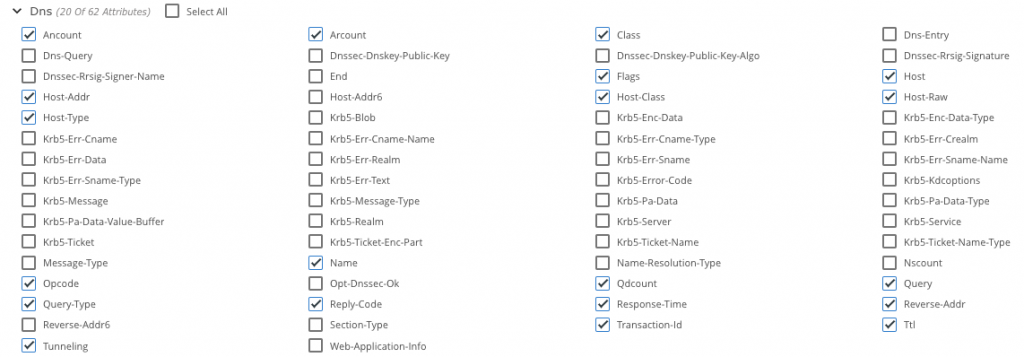
From that you can determine high entropy, which may indicate domain-generated algorithms. The following is generated by the Gigamon Splunk app:
III. How Are SSL/TLS Certificates Being Used?
You can also use Gigamon Application Metadata Intelligence to export SSL-related information Server Name Indication (SNI) or digital certificates. To do so, select the following attributes. We chose them for our template, but you can select others, depending on the tool that’s ingesting this information.
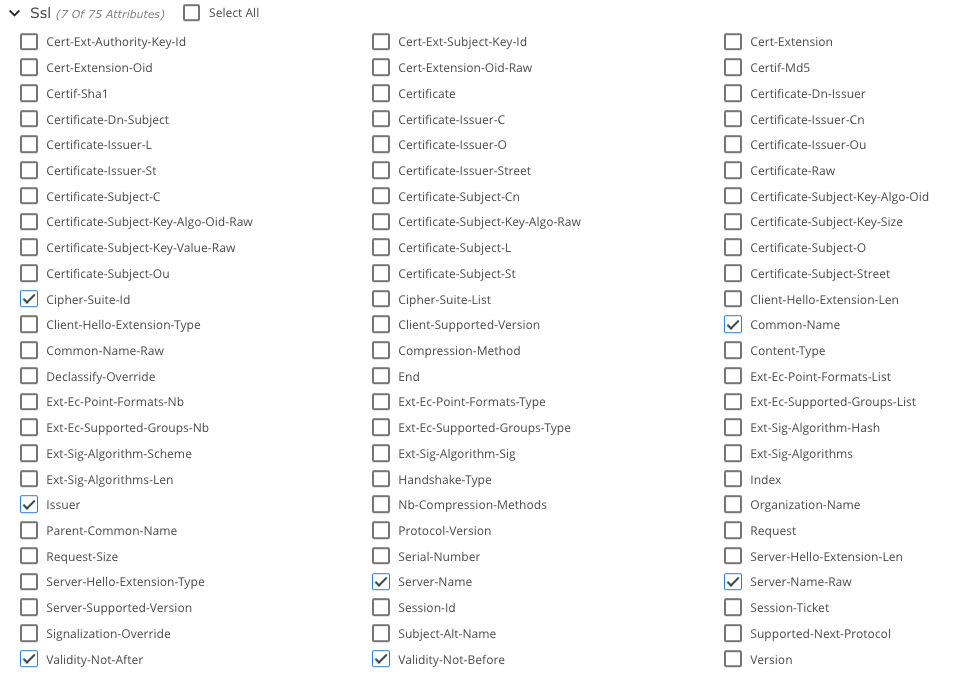
And here is what you will see in your SIEM:
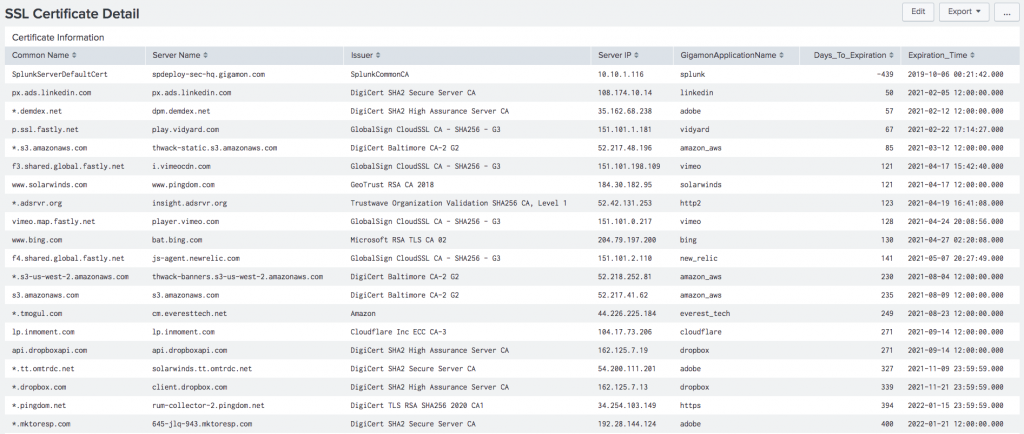
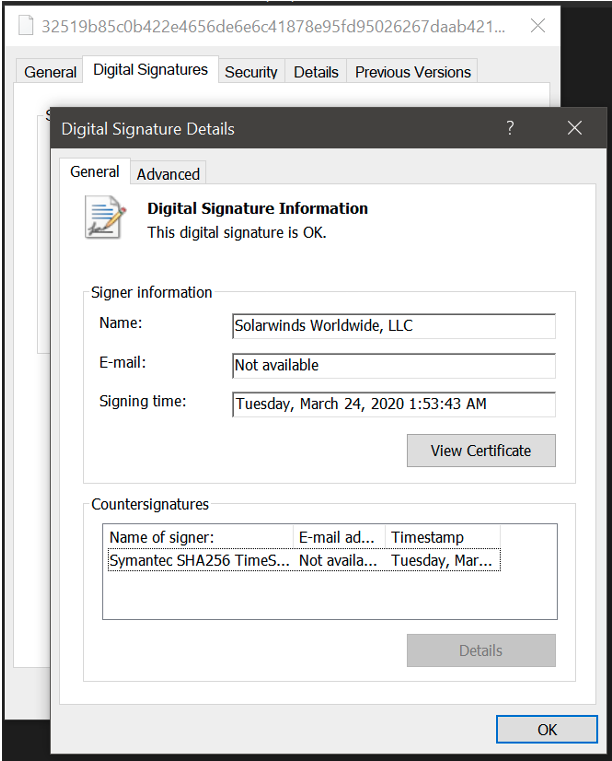
Certificates signed between March and May of 2020, like the one shown below, are likely to be compromised certificates.
IV. Using Kerberos
Lastly, here are the Kerberos-related metadata attributes to export:

You can use Kerberos metadata elements to identify unusual logins in the environment. In case you have a compromised SolarWinds Orion server in your network, you can isolate it based on IP address and use Kerberos metadata elements to closely monitor any unusual login attempts made by the server.
How to Get Additional Help
If you’d like help with these techniques or additional ideas, sign into and start a discussion at the Gigamon Community’s Security Group.
References
Sunburst — FireEye’s Discovery of Trojanised SolarWinds Software
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.