Parental Monitoring Gone Bad — Analysis of an Unassuming Mobile Threat
As a part of detection research, our team routinely hunts for new and unknown malicious network activity. While hunting for malicious HTTP, Gigamon Applied Threat Research (ATR) spotted a pattern of network behavior that revealed an interesting mobile-based threat. ATR was able to identify the source of the traffic as an Android application known as Taslal, which seems to be marketed towards parents wanting to keep tabs on their children. However, in this case ATR noticed exfiltration of audio files, recorded by the device itself from a sensitive engineering environment, and we’re fairly certain that our victim was not being monitored by his or her parents.
In this blog, we’ll provide a general overview of the malware and its capabilities, highlighting several notable features we observed and a possible spyware family relationship. Additionally, we hope to shed some light on what is not necessarily a sophisticated threat, but perhaps an under-appreciated vector borne by mobile devices, and one that may be particularly applicable in bring your own device (BYOD) environments.
Installation & Configuration
As ATR did not witness exploitation or installation. It is unknown how the actors placed the application onto the victim device, but there are methods available for surreptitious installation. Root exploits for Android devices have been previously documented and observed in use with malware campaigns. Additionally, malware has been seen being installed through other trojanized applications.
ATR performed dynamic analysis of the application with the assumption that the initial configuration and installation could be performed programmatically. Unintended installation, on the other hand, is unlikely, as it prompts for an array of excessive permissions. Upon being initialized, the app accepts an “activation code” to associate it with a particular account and performs two installation methods:
- Requests permission to add a device administration application (reference one and two). Specifically, this will grant the application the ability to:
- Erase all data
- Change the screen-unlock password
- Set password rules
- Monitor screen-unlock attempts
- Lock the screen
- Requests permission to add an accessibility service. Accessibility services on Android provide the ability for the application to interact with user interface elements and monitor additional actions. In the case of Taslal, it specifically
Upon activation and registration, the application will reach out to the URL hxxp://frzix[.]com:8080/Sys/Registers/Activate.php and perform an HTTP POST with user and device information.
public Registration getRegistrationInformation(Context context) {
TelephonyManager telephonyManager = (TelephonyManager)context.getApplicationContext().getSystemService("phone");
Registration registration = new Registration();
registration.setCity(null);
registration.setCountry(null);
registration.setDeviceSerial(Build.SERIAL);
registration.setDob(0L);
registration.setFirstName(null);
registration.setGender(1);
registration.setImeiNo(telephonyManager.getDeviceId());
registration.setLastName(null);
registration.setOsVersion(Build.VERSION.RELEASE);
registration.setPlatformType("Android");
registration.setRegistrationIP("192.168.0.100");
registration.setServiceModel(Build.MODEL);
registration.setServiceName("Android");
registration.setSimId(telephonyManager.getSimSerialNumber());
AppPreferences.savePreferences((Context)context, (String)"SIM_ID_KEY", (String)telephonyManager.getSimSerialNumber());
registration.setSocialInfo(null);
registration.setSoftwareBuildVersion(RegistrationManager.getVersionName((Context)context));
registration.setTimeZoneId(AppUtility.getTimeZoneID());
registration.setTimeZoneOffset(AppUtility.getTimeZoneOffset());
if (AppRootUtility.isRooted()) {
registration.setBuildType(Integer.valueOf(2));
return registration;
}
registration.setBuildType(Integer.valueOf(1));
return registration;
}
Figure 3: Application configuration function.
Next, the application will reach out to the server to update local settings by making a request to hxxp://frzix[.]com:8080/Sys/Controls/GetSettings.php. These preferences are stored in the application’s database. The preferences include all of the default controls for what will be monitored on the device.
Once the settings are up to date, the phone will beacon back letting the server know it has been registered by posting to the URL hxxp://frzix[.]com:8080/Sys/Registers/PushRegId.php. Once registered, the application will communicate to the server to get timezone information from URL hxxp://frzix[.]com:8080/Sys/Controls/Service.php.
The last step of registration is to execute the default tasking of uploading the browser history from the device. This is done by performing an HTTP POST to URL hxxp://frzix[.]com:8080/Sys/ADats/Br.php with a JSON list of history elements.
Beaconing Command and Control
After installation, the application enters a command loop where it regularly checks in to look for tasking from the C2 servers at the URL hxxp://frzix[.]com:8080/Sys/Controls/. The tasking will be returned as a JSON string including an element named “command” that will include a command code. Figure 4 shows the command codes present in the application. Some functionality from these commands will be discussed later.
public interface COMMANDS
{
public static final String DISABLE_LOCATION_SERVICES = "4-10-2";
public static final String DISABLE_WIFI = "4-11-2";
public static final String ENABLE_LOCATION_SERVICES = "4-10-1";
public static final String ENABLE_LOGGING_TO_ROOT_MODULE_PATH = "4-7-3";
public static final String ENABLE_LOGGING_TO_SERVER = "4-7-1";
public static final String ENABLE_LOGGING_TO_SERVER_DB = "4-7-2";
public static final String ENABLE_WIFI = "4-11-1";
public static final String LOCK_DEVICE = "4-3-1";
public static final String PAUSED_SERVICE = "0-0-0";
public static final String PREFERENCE_APP_WHITEBLACK_SYNC = "3-1-2";
public static final String PREFERENCE_GEOFENCES_SYNC = "3-1-3";
public static final String PREFERENCE_MDM_PROFILE_SYNC = "3-2-1";
public static final String PREFERENCE_SYNC = "3-1-1";
public static final String PREFERENCE_WATCHLIST_NO_SYNC = "3-1-4";
public static final String PREFERENCE_WATCHLIST_WORD_SYNC = "3-1-5";
public static final String SCREEN_SHOT = "4-8-1";
public static final String SET_PASSWORD_ON_DEVICE = "4-3-1";
public static final String START_SERVICE = "0-0-1";
public static final String SURROUND_RECORDING = "4-1-1";
public static final String WIPE_DEVICE = "4-2-1";
}
Figure 4: Android interface definitions.
Additionally, the application regularly communicates a status update by performing an HTTP POST to URL hxxp://frzix[.]com:8080/Sys/ADats/Sttus.php. The status update will include key device details like:
- Network information
- Network location
- Operator information
- Device uptime
- Wifi information
- Battery status
Action and Event Logging
During installation and through interactive tasking, the application registers a number of explicit intents on the system, essentially providing callback functionality when a certain action happens on the device. Taslal leverages these intents to log actions the user is performing. By default, in the application manifest file, the application registers the following intents:
- intent.action.MAIN
- intent.action.BOOT_COMPLETED
- intent.action.USER_PRESENT
- intent.action.TIMEZONE_CHANGED
- intent.action.TIME_SET
- intent.action.NEW_OUTGOING_CALL
- intent.action.PHONE_STATE
- intent.action.NEW_OUTGOING_CALL
- intent.action.USER_PRESENT
- intent.action.SCREEN_OFF
- intent.action.SCREEN_ON
- intent.action.PACKAGE_ADDED
- intent.action.PACKAGE_REPLACED
- intent.action.PACKAGE_REMOVED
- intent.action.PACKAGE_DATA_CLEARED
The intents provide the spyware a basic capability of logging actions to the database for later query and retrieval.
Additionally, Taslal includes a custom watchlist capability and a notification manager that allows an attacker to add event level notifications. This manager communicates notifications to hxxp://frzix[.]com:8080/Sys/Alerts/Alert.php. Figure 5 includes a list of notification codes that gives you a quick overview of what event level capabilities it possesses.
public interface NOTIFICATION
{
public static final String GEO_FENCE_VISIT = "2-3-1";
public static final String NEW_CALL = "2-1-1";
public static final String NEW_EMAIL_MESSAGE = "2-5-1";
public static final String NEW_FACEBOOK_MESSAGE = "2-15-1";
public static final String NEW_GEMAIL_MESSAGE = "2-10-1";
public static final String NEW_IMESSAGE_MESSAGE = "2-9-1";
public static final String NEW_LINE_MESSAGE = "2-14-1";
public static final String NEW_SKYPE_MESSAGE = "2-8-1";
public static final String NEW_SMS = "2-2-1";
public static final String NEW_VIBER_CALL = "2-7-1";
public static final String NEW_VIBER_MESSAGE = "2-6-1";
public static final String NEW_WATCHLIST_CALL = "2-1-2";
public static final String NEW_WATCHLIST_EMAIL_MESSAGE = "2-5-2";
public static final String NEW_WATCHLIST_FACEBOOK_MESSAGE = "2-15-2";
public static final String NEW_WATCHLIST_GEMAIL_MESSAGE = "2-10-2";
public static final String NEW_WATCHLIST_IMESSAGE_MESSAGE = "2-9-2";
public static final String NEW_WATCHLIST_LINE_MESSAGE = "2-14-2";
public static final String NEW_WATCHLIST_SKYPE_MESSAGE = "2-8-2";
public static final String NEW_WATCHLIST_SMS = "2-2-2";
public static final String NEW_WATCHLIST_VIBER_CALL = "2-7-2";
public static final String NEW_WATCHLIST_VIBER_MESSAGE = "2-6-2";
public static final String NEW_WATCHLIST_WHATSAPP_MESSAGE = "2-4-2";
public static final String NEW_WHATSAPP_MESSAGE = "2-4-1";
public static final String SIM_CHANGE_NOTIFICATION = "2-12-1";
}
Figure 5: Android notification hooks
Notable Malware Capabilities
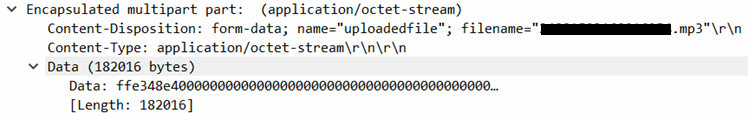
Some of the more interesting capabilities include the ability to record room audio, as mentioned in the introduction, read messages from various communication applications, and send SMS messages. Figure 6 shows an example of MP3 encoded audio being uploaded to the attacker server.
Although the attacker we observed leveraged their access to download room audio with work conversations from a very sensitive environment, they apparently failed to understand the gravity of this access. They subsequently used the SMS functionality in the malware to send spam messages such as this example:
“73697 gereetei SKYmedia hereglegch tany 3 saryn tulbur 59101MNT. Ta 04/20ny dotor tulnu uu. QPay holboos: http://qpay[.]mn/q/?q=k6C2Fr4Zf7CXb4lerdeicbuM2sily3”
This failure to recognize target value leads us to believe the initial infection was opportunistic in nature, rather than targeted. If the attacker had known the value of this system, this access could have been exploited to move laterally within the target network and/or gain information of untold value to those engaged in economic espionage.
Spyware Family Relations
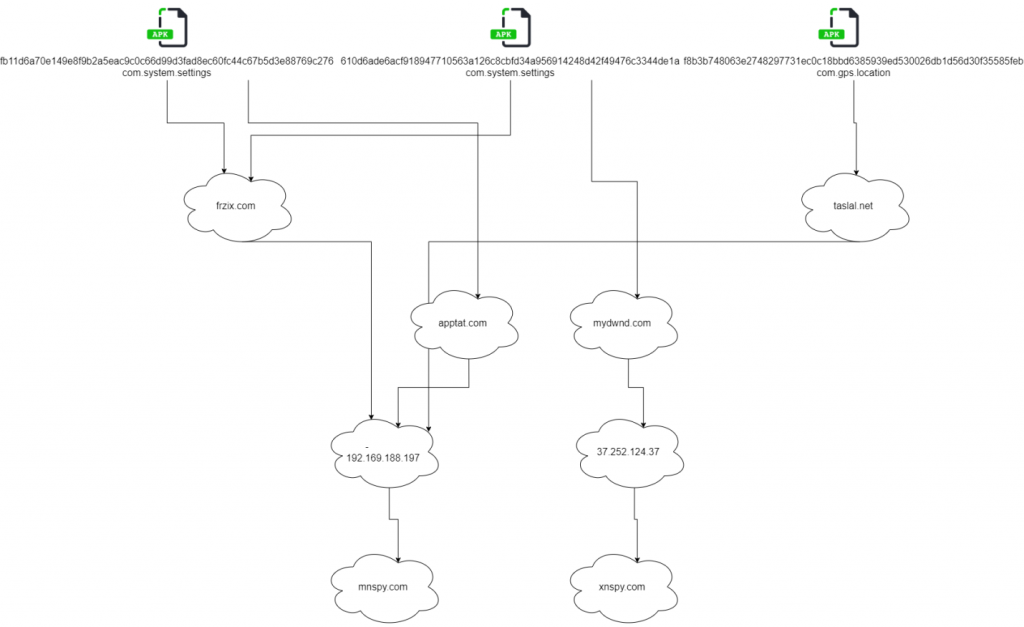
While investigating the Taslal application, several interesting relationships began to surface. At the time this threat was spotted in the wild, the hosting infrastructure served several different markets with the same basic application. Taslal itself is targeted at Mongolian-speakers, but mnspy[.]com existed on the same IP address and appeared to simply be an English-language version of the same tracker app. These applications also included hardcoded update URLs, the first of which was on apptat[.]com that shared the same IP address, and the other on a separately hosted domain mydwnd[.]com. The mydwnd[.]com site hosted an APK from a similar, but substantially different piece of tracking software called XNSPY. The exact relationship isn’t clear, but there may be a shared origin for Taslal, MNSPY, and XNSPY, be it code-theft or some kind of licensing agreement.
Indicators of Compromise
Android Packages
| Package Name | Display Name | Hash |
|---|---|---|
| com.system.settings | System Settings | fb11d6a70e149e8f9b2a5eac9c0c66d99d3 fad8ec60fc44c67b5d3e88769c276610d 6ade6acf918947710563a126c8cbfd34a 956914248d42f49476c3344de1a |
| com.gps.location | System Services | f8b3b748063e2748297731ec0c18bbd6 385939ed530026db1d56d30f35585feb |
Network IOCs
- User-Agent: iMaks_b9c70eb5aa2cc909659158fdf43fe6ad
- 169.188.197
- mn
- net
- com
- com
- com
- 252.124.37
- com