Zero Trust for Federal
This article is the fourth of a series on Zero Trust.
The Defense Innovation Board (DIB) report “The Road to Zero Trust” and the American Council for Technology-Industry Advisory Council (ACT-IAC) “Zero Trust Cybersecurity Trends” have brought the concept of Zero Trust front and center for federal CIOs and CISOs. The concept fundamentally focuses on establishing new perimeters around sensitive and critical data. These perimeters include traditional prevention technology such as network firewalls and network access control (like 802.1x) but also include authentication, logging and controls at the identity, application and data layers, leveraging Identity Credential Access Management (ICAM), two-factor authentication through a token or hardware.
Many of these concepts may seem familiar, as they are effectively a new marketing spin on “defense in depth” and “assume breach,” and seek to both increase the number of controls between an adversary and critical data as well as the number of logging boundaries. Logging boundaries are visibility and control layers that log activity and require any legitimate user or attacker to interact with them to access data. For example, if a database requires a user to access it through an application and that application requires two-factor authentication.
Evolution to Zero Trust
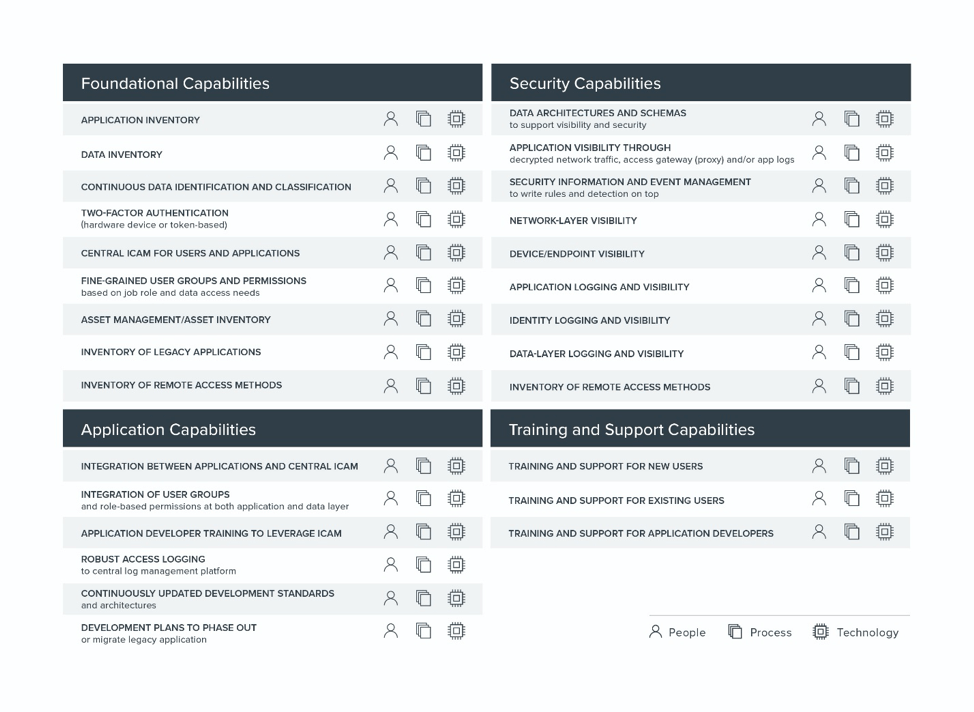
“Zero Trust” sounds simple as two words, and many information security vendors have popped up with marketing that claims to make Zero Trust easy if you purchase their products; however, the realities are much more complex. More than a plug-and-play security technology, Zero Trust architectures (ZTA) require extensive foundational investments and capabilities as well as extensive logging and control layers that are largely in the traditional IT stack.
At a foundational layer, ZTA requires:
Starting Mid-stride
Federal information and technology environments are complicated, and as CIOs and CISOs review the list above, they will see in many cases they’re already notionally on a path to Zero Trust. There are a number of foundational requirements that are not first-heard or unique to Zero Trust, and astute readers will recognize that many of the requirements above map to DHS’ Continuous Diagnostics and Mitigation (CDM) program. Since there are already resources laid out for CDM, Gigamon recommends starting with CDM Phase 1 requirements that focus on understanding what’s on the network.
CDM Phase 1
- Automation of hardware asset management
- Automation of software asset management
- Automation of configuration settings
- Common vulnerability management capabilities
Challenges and Recommendations
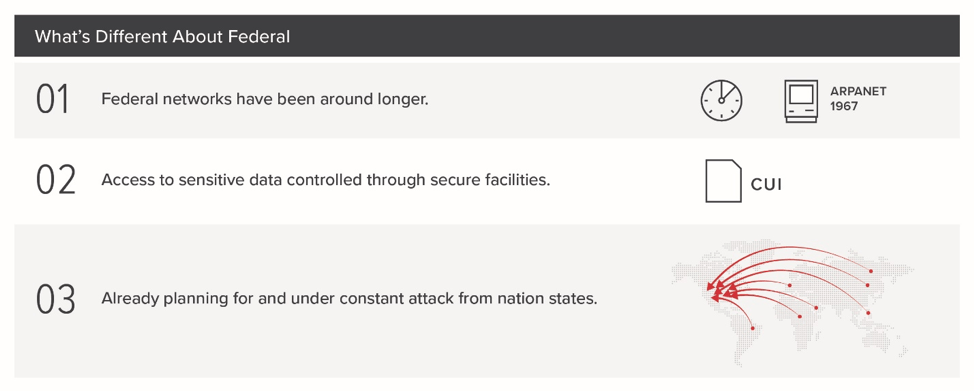
First and foremost, Zero Trust is a marketing term, not a well-defined technical paradigm or architecture. We can see this by looking at the number of non-vendor resources that are peer reviewed and openly available (limited to the Google BeyondCorp papers). ZTA as a marketing term also generally assumes that you’re an enterprise that has fully embraced concepts like DevOps, and have limited legacy data and applications. Federal networks are different, largely because they have been around longer and have more legacy technology than most enterprises, leverage secure facilities for access to sensitive data, and are already under constant attack from nation-state adversaries.
Federal CIOs and CISOs facing directives for ZTA should take recommendations from vendors with a grain of salt and may get the best results by focusing on the foundational areas already driven by existing efforts like CDM.
Gigamon recommendations for ZTA:
Gigamon offers a number of solutions to help you gain situational awareness of network traffic, data and applications in your environment, including:
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today