Zero Trust: What It Means in 2020
This article is the first of a series on Zero Trust.
Security is a moving target. One of the most important lessons that we’ve learned in the last 20 years is that unsegmented or “flat” networks lead to large-scale breaches. This has remained true across advanced persistent threat (APT) attacks and, more recently, crippling ransomware attacks against major corporations. The root cause is that flat networks lack the boundaries and logging needed to prevent small breaches from becoming big ones, and therefore don’t protect sensitive and business critical data.
Zero Trust at its highest level is a strategy for understanding and managing perimeters and access in modern computing environments. Most corporate and government networks have inherited a legacy of IT and security infrastructure and configurations that conflate devices, users, networks, identities, access and permissions to the point that they’re described as flat networks. Flat network design is not without benefits; it optimizes for accessibility, performance and maintenance. On a flat network, anyone in the environments is given (or can easily gain) access to any other users’ information, data or applications, keeping administrative overhead low but drastically increasing risk. Zero Trust provides a target framework to address complexity introduced by enterprises that are increasingly embracing mobility, cloud and web-facing applications and services.
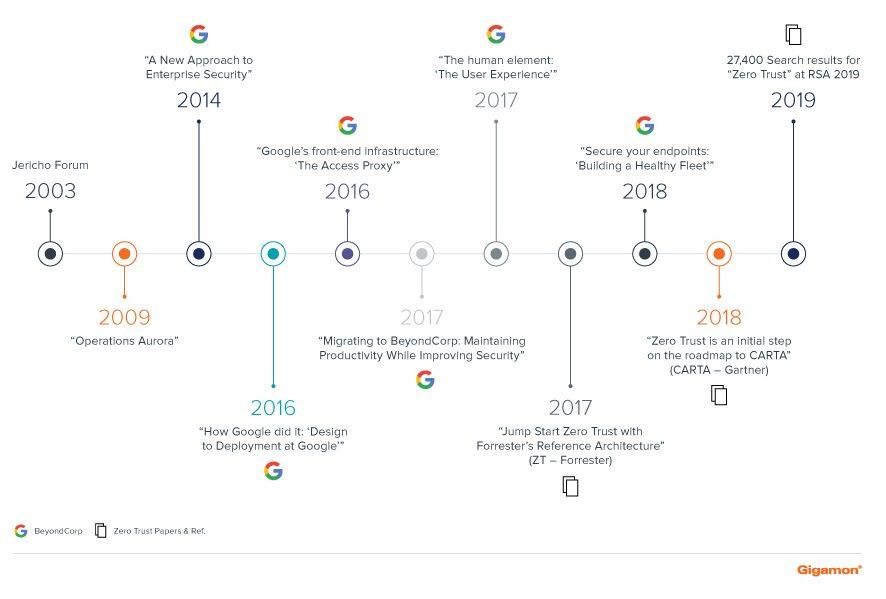
Zero Trust is sometimes more of a moniker than a strategy, and it’s important to understand the difference between marketing and reality. Google’s BeyondCorp is the best-documented implementation and reference architecture of what it means to truly understand and manage implicit trust in a real-world implementation. A reaction to 2009’s Operation Aurora attacks, BeyondCorp represents a top-down mandate to architect and build one of the most secure enterprises on the planet with a complex and modern technology stack.
A Brief History of BeyondCorp and Zero Trust
In 2020, the industry is still asking a lot of the same strategic questions around best practices such as “assume breach” and “defense in depth.” Zero Trust ultimately falls in the same lineage of strategic paradigms; however, it appears to be getting much more industry airtime. Enterprise customers need a strategy that doesn’t depend on the local area network (LAN) for access and trust, and massive marketing dollars are putting Zero Trust in many RFPs and vendor pitches. The underlying customer need is that modern enterprise users require simple, secure and constant access to applications and data from anywhere in the world.
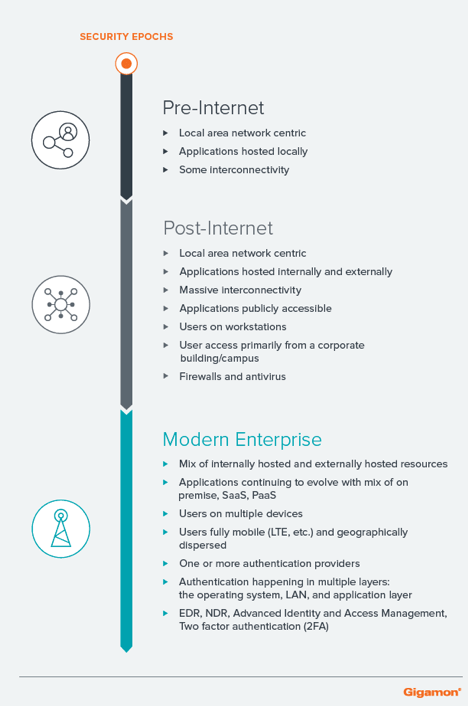
The shift to a modern enterprise is influenced heavily by three well-known underlying trends:
- Mobility and remote work
- Applications that are overwhelmingly web-based
- SaaS, IaaS, PaaS and cloud
These trends challenge our traditional idea of what securing the enterprise looks like. If we look at the security epochs we see:
The Zero Trust journey starts by IT and Security asking, “Where does implicit trust exist in our environment?” In my experience, implicit trust exists in one or more of the areas below and, with a risk-based approach, enterprises can effectively stack rank and prioritize their efforts:
- VPN connectivity
- LAN/network core
- Network segmentation (or lack thereof)
- Authentication and directory services (Active Directory)
- Service accounts
- Single-factor authentication
When we look at a Zero Trust roadmap, many executives, architects, engineers and vendors want to jump directly into new technologies and designs; however, without a deep understanding of the environment, that approach is unlikely to be successful in any established IT and security environment. The best approach is to first start with understanding the devices, identities, applications and data that exist in an environment, to help design a set of controls that can be operated to decrease implicit trust and associated risk through monitoring.
In future posts, we’ll explore what it takes to start tackling the different phases of the customer journey, as well as the complexities of building and running different Zero Trust architectures.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today