Gigamon ThreatINSIGHT 3.0
We are pleased to announce the release of the latest version of the Gigamon ThreatINSIGHT™ solution. Gigamon has enhanced ThreatINSIGHT with new functions and features that help organizations keep secure by addressing an all-important need within today’s environments: adapting your security to your changing environment. The features are as follows.
New Features and Functionality
Dashboards
Dashboards are better than ever: Default Dashboards bring key information regarding compromised devices to the forefront, and widgets can now be resized, changed and saved as a Custom Dashboard specific to an account, allowing users to tailor it according to their needs.
>> Learn more about Gigamon ThreatINSIGHT and request a demo
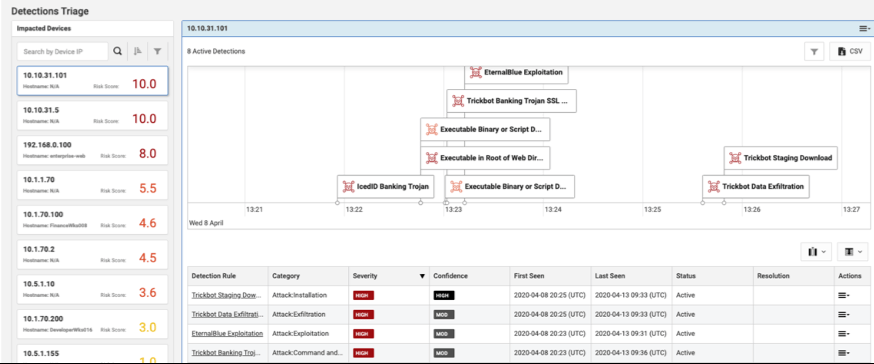
Device Triage View
ThreatINSIGHT now has a Device Triage view that provides a device-centric timeline of detected threats and allows analysts to focus attention on the most critically impacted assets in the environment.
Device Risk Calculation
In order to help analysts properly prioritize response, we have added a Risk Score. This score is calculated based on the number, severity and activity of currently active detections on a device. The score is updated automatically if new device activity is detected, allowing teams to adjust response actions according to the most severe threat activity.
Event Entity Extraction
Event context is critical (for example, when did something happen, the “who, what, how”). To help teams derive these answers as quickly as possible, ThreatINSIGHT extracts critical values (those that indicate possible compromise) from data fields and groups them in one location and view for quick analyst review.
Dynamic Device Tracking and Hostname/MAC Searches
Analysts must track a device’s IP continuously (who had that IP at the time of detection, what IP(s) did a device have next, and so forth). ThreatINSIGHT now uses visible DHCP data to dynamically track device IP changes.
In addition, ThreatINSIGHT now provides analysts with the ability to search via a device’s hostname or MAC address. These three properties (IP address, hostname and MAC address) are now associated across each tracked device, allowing quick data searches (for all data related to a device, independent of IP changes) to be performed.
New Detection Capabilities
Gigamon’s Applied Threat Research (ATR) team is continuously engineering and releasing detection capabilities to provide continuous threat detection improvements. ThreatINSIGHT 3.0 incorporates a number of detection improvements that include new behavioral analytics, expert systems and statistical models, used to identify suspicious patterns of DNS request/response activity and suspicious SSL session activity associated with compromise and command-and-control (C2) activity.
Improvements
Sensor Deployment
ThreatINSIGHT now grants administrators the ability to download virtual sensors from the UI as well as self-provision any sensor (physical or virtual) in a straightforward manner. This allows teams to add or remove sensors as necessary without requiring additional support from Gigamon.
Additional Updates
This release offers numerous additional improvements that help teams efficiently detect and investigate a network. For more information, please consult our release notes, available from the ThreatINSIGHT portal.
How to Get Started
To learn how ThreatINSIGHT can help secure your organization, visit the ThreatINSIGHT webpage or request a demo.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Network Detection & Response group.
Share your thoughts today