Ten Critical Scenarios That Benefit from Gigamon Application Filtering Intelligence
Time Flies When You’re Having Fun
It has been nearly a year since Gigamon announced our groundbreaking Application Intelligence. By working with a broad swath of customers since then, we can now identify even more innovative ways to apply this unique app-aware solution. Based on that experience, below you’ll find the top ten real-world use cases.
Application Identification Is Paramount
Without visibility and control over applications, network and security operations teams may be compelled to feed all network traffic to their security and analytics tools. Processing all that traffic can overwhelm the available resources, which reduces performance and increases overall risk. Typical network traffic includes high-volume/low-risk traffic, such as video and social media streams and custom applications. Feeding these unnecessary types of traffic to all tools leads to their over-provisioning.
Deep Packet Inspection Is Key
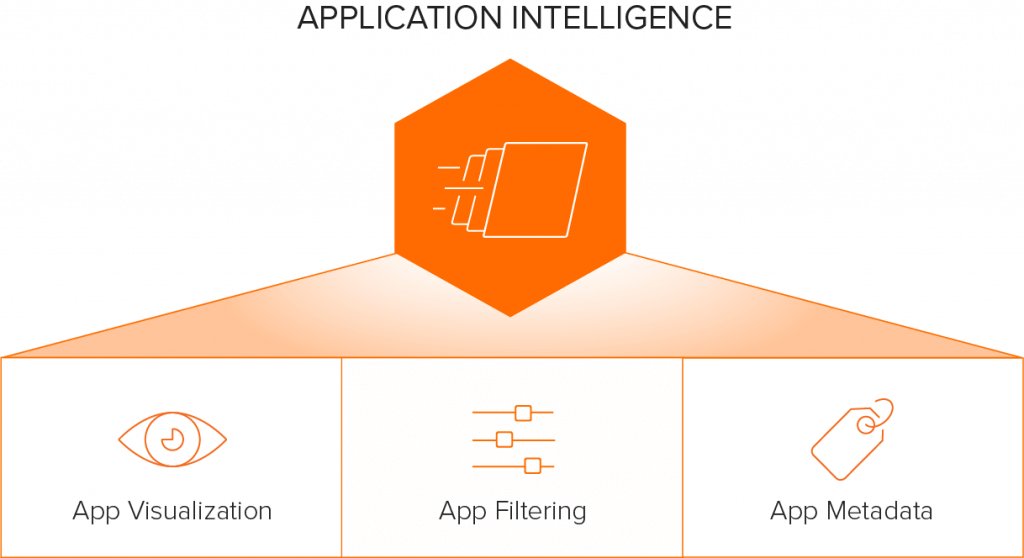
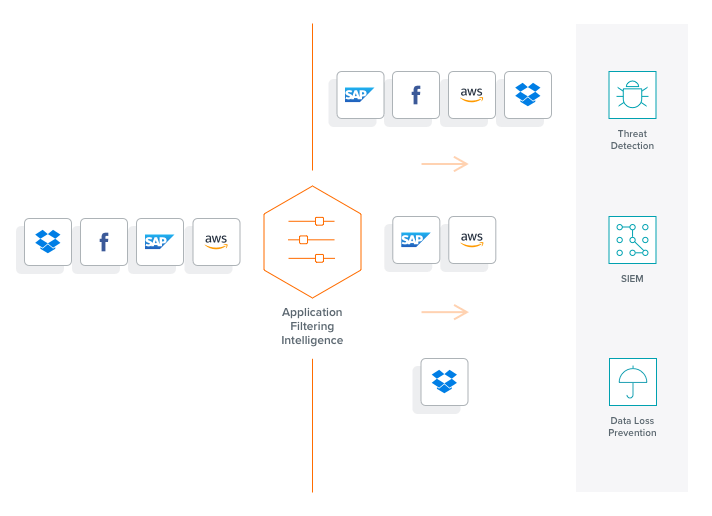
Application Visualization, combined with our Application Filtering Intelligence (AFI), uses deep packet inspection (DPI) to identify applications and protocols from network packets and filter them as appropriate. Applications are classified based on various attributes related to traffic behavior; this involves flow-based matching, bi-directional flow correlation, heuristics and statistical analysis. AFI lets you accurately identify over 3,000 off-the-shelf software applications, as well as custom apps.
AFI provides this discovery process independent of encapsulation, port number or encryption, which lets you feed only the intended traffic to tools. With AFI, you can filter out high-volume/low-risk traffic and custom-built applications, and you can send high-risk, application-specific traffic to the right security tools for the best security posture. Once the apps are identified, Gigamon Flow Mapping® directs traffic under the auspices of GigaVUE-FM fabric manager. For more details, read the Application Filtering Intelligence Feature Brief.
The ability to do targeted inspection of network protocols and applications of interest helps you achieve better ROIs by improving the performance-and-detection efficacy of the tools.
AFI Use Cases
To help you be more efficient and get the most out of this investment, Gigamon provides a set of validated designs that focus on common use cases across multiple industries. Gigamon Validated Designs (GVDs) are lab-tested solutions that cater to your network and security architects and administrators who want to gain more insights and learn how to deploy these solutions in your environments. The following use cases have been assessed and help you get the most out of AFI.
- Focus on relevant flows to optimize security tools. Some network tools focus exclusively on certain applications and protocols, and therefore feeding them anything outside of a narrow protocol suite (HTTP or email, for example) is unnecessary. If these tools spend processing power inspecting all network traffic, then most of the tools’ resources are expended without yielding any additional threat detection. To optimize tool performance, therefore, it’s best to refine traffic with a laser focus upon specific applications or protocols and offload irrelevant traffic from expensive resources.
- Filter high-volume and low-risk traffic. Threat detection tools are primarily interested in suspicious traffic. To optimize tool performance and to prevent traffic from hogging limited tool capacity, it’s best to not feed them high-volume/low risk traffic. Some content can be deemed safe by design, such as high-bandwidth Netflix or Hulu streaming media and Windows updates. This content does not have, for instance, hidden command/control code and it’s from a known, secure source. IT needs to distinguish this from other content that is not safe, such as certain YouTube channels where the content could contain hidden malware.
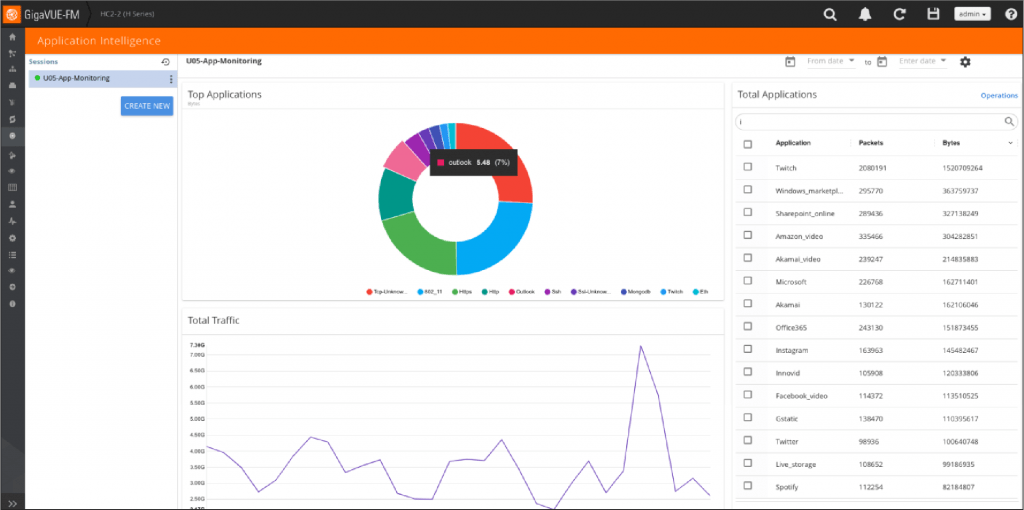
- Throttle bandwidth by app. AFI provides not only the identification of numerous apps, but also the amount of capacity they are drawing. The main dashboard shows the top ten apps by usage, as well as details on all other apps and traffic levels. IT can leverage this data to enforce bandwidth limits by application via rate-limiting or other methods. With users nefariously using corporate resources for Facebook, Instagram or other social networking sites or streaming media, these non-critical, personal-use only apps can cause higher priority traffic to suffer performance loss.
- Find and stop rogue apps. With the identification of thousands of applications, IT can discover those shadow IT apps running on the network. In the age of bring your own device (BYOD) and cloud-based SaaS services, such usage is commonplace. While the primary focus is to filter this traffic and rely on security tools for protection, you can also use AFI to proactively find and eliminate unsanctioned apps, particularly those with known vulnerabilities.
- Prioritize most critical traffic based on apps. Modern networks typically incorporate quality of service (QoS) methods to give priority to select traffic, but this is based on L2–L4. With AFI, you can give traffic from specific apps precedence. Typically, these apps would involve things like e-commerce, outbound web-based servers or VoIP and would be elevated over things like CRM, email and internal streaming media use.
- Identify and filter custom applications. Large organizations typically run hundreds of custom applications that are often developed in-house for specific functions. With growing network traffic, these applications tend to outgrow the available hardware resources needed to support this expansion. To prevent future network disruptions, it’s crucial to identify the exact resources these applications need. Moreover, compliance makes monitoring custom applications essential since they could also be vulnerable to attacks. As these apps are not as dynamic as standard apps and their structure is well known, IT can potentially use IP address ranges and/or port numbers to help identify them. Given that these in-house apps may use the same port, however, a much better approach is to leverage deep packet inspection (DPI) by defining signatures and searching for these regex patterns in the header or payload. Once found, they can be filtered out as needed.
- Identify missing or misclassified traffic and direct it to proper tools. This is a corollary to finding relevant flows. Network operations teams use various methods to properly route traffic. This AFI technique can identify improperly classified traffic or traffic not being directed to the right tools. AFI can also validate legacy routing methods to ensure accuracy and completeness.
- Identify encrypted apps running on nonstandard ports. Apps normally are assigned to specific ports and IT can to some degree identify and filter based on port. However, for many apps, this is not the case, especially when SSL/TLS is encrypted, running on nonstandard ports and IT desires to filter out ports such as 443. AFI provides this ability.
- Identify connections using nonstandard ports. For communication protocols such as SSH, DNS, Telnet and RDP, the ports are well known and normally used. If these connections are using different ports, then this could indicate hackers are using are using them to bypass IT security controls.
- Overcome port spoofing. With traditional client-server traffic, hackers can use port spoofing techniques where they send SSH traffic over port 443, which is used for SSL. If you cannot identify applications, this technique works and traffic is improperly shown as SSL. AFI, in contrast, can see through this misdirection and properly list this traffic as SSH.
Learn More
AFI provides the insight you need into application traffic running on your network. You can better manage, monitor and secure your infrastructure by leveraging Layer 7 visibility. To better understand how to solve these ever evolving use cases, please request a demo. View an on-demand webinar on Application Intelligence for more insights.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today