TLS 1.3 — Its Benefits Are Real, but So Are the Drawbacks
Updated October 28, 2021.
TLS 1.3 is the newest version of transport layer security, and provides reliable encryption for data sent over the internet. But it’s not perfect. Here, we address the advantages — and possible drawbacks — TLS 1.3 brings to the table.
I’ve always wondered if Sir Timothy John Berners-Lee, the inventor of the World Wide Web, would have put more emphasis on security if he knew how pervasive the internet would become across all aspects of our personal and business lives.
There is a critical need for better security as larger volumes of sensitive data flow over the web. Just as living creatures have evolved to adapt to challenging conditions, security technologies must also adapt to new, more risky environments.
In terms of evolving internet security, TLS 1.3 (Transport Layer Security) has been talked about for many years in the network and security domains. The relatively long timeline of five years from inception to release reveals just how much time and effort has been put into refining and ratifying this standard. Very simply put, TLS 1.3 will become the de facto security standard for all communication over the internet.
TLS 1.3 Overview
TLS 1.3, starting from April of 2014 to the final draft released in March 2018, is the most recent version of TLS, which is itself the successor to (now-deprecated) SSL. Much like SSL and previous TLS versions, TLS 1.3 is an encryption protocol designed to ensure the security of information sent and received over the internet. For a website to feature HTTPS encryption, it needs a TLS certificate.
The development of TLS 1.3 focused on two main enhancements: faster speeds and stronger security. What does TLS 1.3 mean for end users and the NetOps and SecOps professionals responsible for network performance and security?
For Users
Users can upgrade to TLS 1.3 with a click of a simple “update” button on their browser. Other than that, the transition is mostly transparent to the end user. Users will benefit from faster and more secure browsing. The performance improvement may not be noticeable to the naked eye since it’s a 100ms improvement in handshake. Over time, however, users will enjoy better connections and faster browsing without needing other upgrades to their internet services.
For NetOps Teams
Wearing a NetOps hat means having responsibility for creating “an agile, scalable and programmable infrastructure capable of delivering business-critical applications and services rapidly and efficiently.”1
In practical terms, this means NetOps teams work to ensure the network runs fast and stays secure even as new standards, tools and applications are added to the mix.
While enabling TLS 1.3 as a de facto standard in your organization may be as simple as adding TLS 1.3 under application or web settings, troubleshooting encrypted cyber content may become more difficult because you can no longer identify, control or log which sites users are going to, as an example.2
As a workaround, you can disable certain fields like server name identification (SNI) to keep some visibility, but this means losing the full benefits of TLS 1.3. Standard network troubleshooting techniques may not be efficient and manual intervention may be required.
These challenges can be partially overcome by using third-party tools, which show unencrypted traffic, but this can bring additional issues — decryption is very resource-intensive and tools at the edge still can’t decrypt east-west traffic.
For SecOps Teams
Nothing makes a SecOps team happier than hearing that their organization will become more secure, especially without extra effort on their part. Yet TLS 1.3 is a double-edged sword. While TLS 1.3 brings lots of security benefits by disabling weak ciphers and using forward secrecy, it also makes it harder for SecOps teams to monitor malware or phishing attacks.
For example, strongly encrypted content presents formidable blind spots for security analysis tools. As a result, they cannot see all the traffic traversing the network, which can lead to long dwell times and increased damage.
Just like new types of security protection, threats also evolve to take advantage of new security loopholes. To detect and remediate threats as quickly as possible, SecOps teams must ensure that they and their tools get a complete view of all traffic on the network (not just a percentage).
The TLS 1.3 Bottom Line
What does TLS 1.3 mean to you as a NetOps or SecOps professional? The bad news is that you can’t just sit back and reap the benefits of better network security as TLS 1.3 rolls out. The good news is that there are things you can do to facilitate the transition that will make your organization much more secure than before.
As mentioned above, decryption can be done at the individual tool level, but this approach has drawbacks — it’s resource-intensive and each tool receives only a subset of network traffic. For example, edge devices like firewalls can see only north-south traffic.
A centralized decryption solution, capable of decrypting all TLS 1.3-encrypted traffic — without violating privacy regulations — and sending compliant traffic to the relevant tools, is a better approach. This approach also frees up tool resources, so they can perform their core tasks more efficiently. A single solution can also serve the purposes of NetOps and SecOps teams so both groups benefit without overlapping investments or adding complexity to the network.
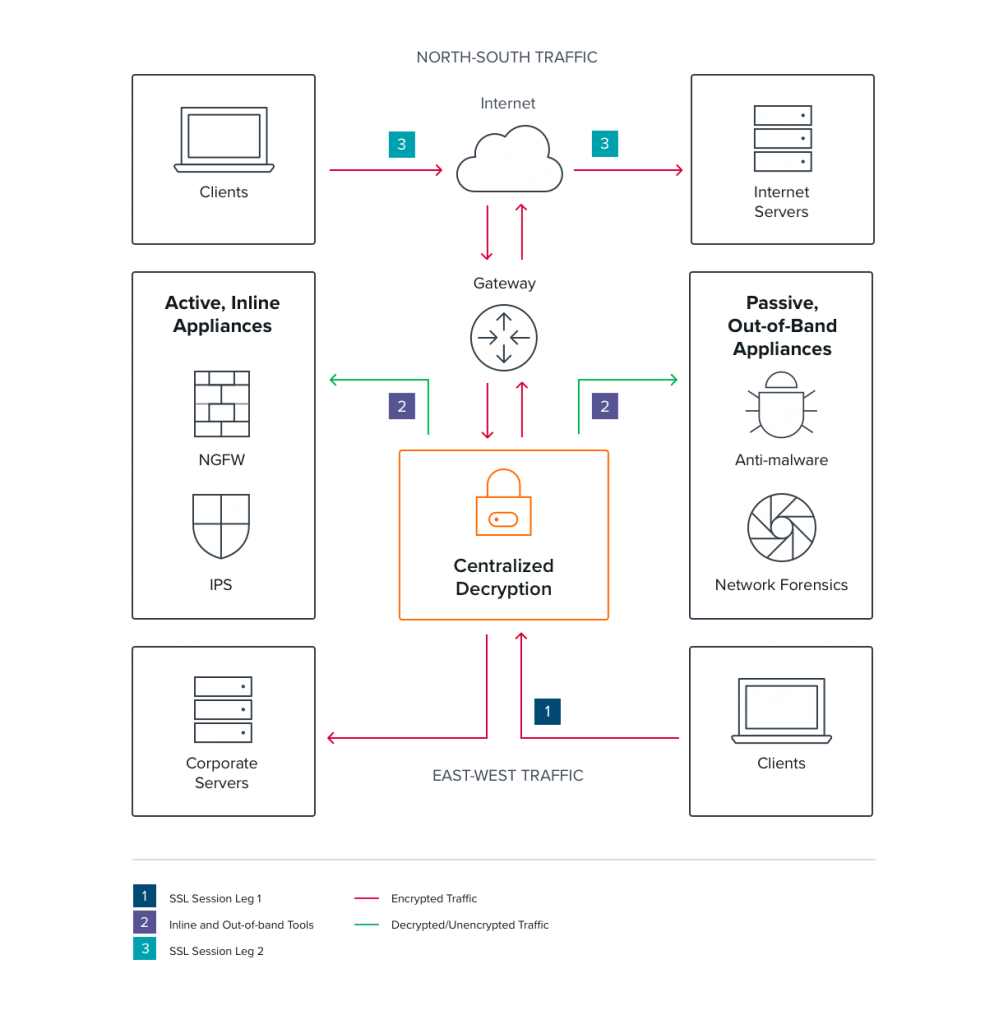
Centralized Decryption — It’s Available Today
Gigamon SSL/TLS Decryption enables SecOps, NetOps and applications teams to obtain complete visibility into SSL/TLS traffic regardless of protocol or application. Learn more by reading “Defending the Digital Enterprise” and our feature brief.
Citations
- “What Is NetOps?” TechTarget. Accessed July 18, 2019. https://searchnetworking.techtarget.com/definition/NetOps.
- Conran, Matt. “Can TLS 1.3 and DNSSEC Make Your Network Blind?” Network World. IDG. December 20, 2018. Accessed July 18, 2019. https://www.networkworld.com/article/3329858/can-tls-13-and-dnssec-make-your-network-blind.html.
Further Reading
- “Gigamon’s Guide to Communications Security: What Is SSL, TLS and HTTPS?“
- “Yes, You Can Run Fast and Stay Secure During Uncertain Times”
- “The Art of Scrying — How Network Visibility Helps Enterprises ‘See’“
Continue the Discussion
People are talking about this in the Gigamon Community’s
Security group. Share your thoughts today.









