Three Families in Three Days – Revisiting Prolific Crimeware to Improve Network Detection: Emotet
By Ed Miles, Paul Ferguson, Fred Davis and Justin Warner
Some of the most interesting intelligence and sharing occurs on threats that are not new. With the creation of our 2H 2018 Crimeware Trend Report, ATR found that seemingly novel but high-volume threats are continuing to impact customers with little initial detection and impose a great cost on the victims they impact. In the report, we sought to dive into how the top three most pervasive threats from the 2H of 2018 leverage network communications to accomplish their objectives: Emotet, Lokibot and Trickbot.
This is Part 1 of a three-part blog series that will share details summarizing the technical methods used by these malware families. In this post, we will explore Emotet, a threat that exhibited significant experimentation in 2018 but still had many consistent techniques in their campaign that provide detection opportunities. It is our goal in this post to clearly apply an intelligence-driven methodology to detection where we seek to understand threats, gain visibility into their field of play, and utilize artifacts of their techniques to gain robust detection.
Emotet’s Trends
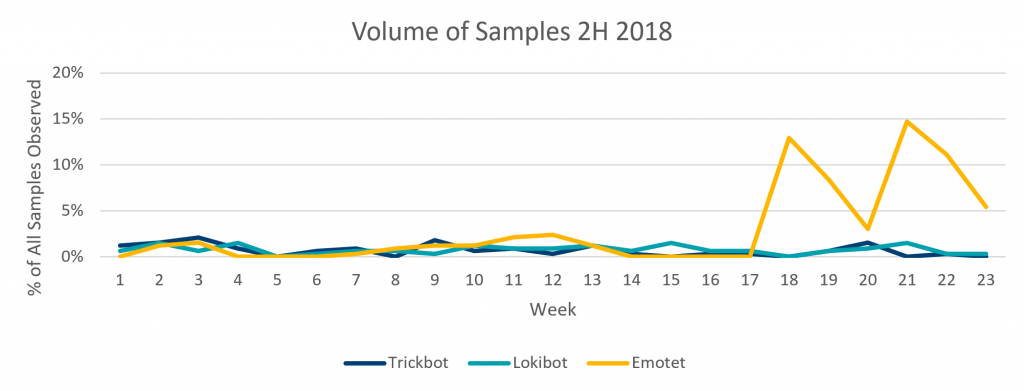
In the 2H of 2018, Emotet as the most prolific threat we observed, at almost 45.9% of our observed samples. Most notably, Emotet’s rapid increase began in early November 2018, which continued through late December 2018. During this time, Emotet campaigns appeared daily with different attachment hashes, different attachment filenames and different email subject lines. On or about 21 December 2018, Emotet went silent and remained silent through the first weeks of 2019.
While Emotet is known to use a variety of office formats, in our observations, 100% of the observed payloads were documents.
Emotet’s Malicious Objectives
Emotet serves many objectives: Information stealer, credential theft, spam and malware distribution are amongst its top offenses. As Emotet persists on its victim machines, it continues to pull down modules that execute independently to carry out the threat actor’s objective. These include:
- Information theft: Steals information from various programs on the machine that might provide sensitive financial information.
- Credential theft: Steals passwords from multiple sources on the machine.2 The blatant use of public freeware utilities by the actor continues the common theme of using off-the-shelf methods to accomplish their objectives with as little work as needed. The threat actor takes minimal effort to evade or disguise the capabilities.
- NetPass.exe (NirSoft) recovers network passwords for currently logged on user
- Outlook Scraper scrapes names and emails from victims’ Microsoft Outlook inbox
- WebBrowserPassView (NirSoft) is a password recovery tool for modern browsers
- Mail PassView (NirSoft) is a password recovery tool for several popular mail clients
- Spam: Emotet will utilize stolen address book details to send additional spam and propagate using its’ standard campaign methods.
- Malware distribution: Once Emotet persists on a victim machine, it often provides access to other malware families such as TrickBot, Qakbot, ICEID and GootKit.
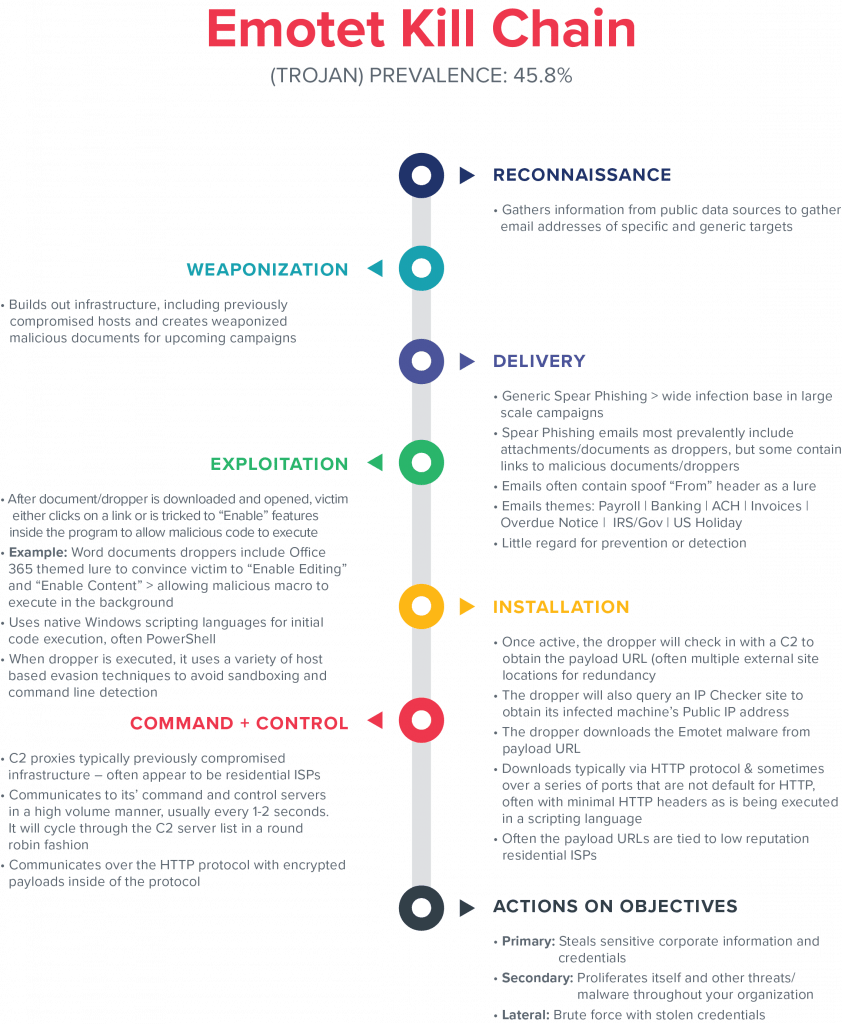
Emotet’s Installation
Once execution has occurred via the initial infection vector, the Emotet dropper will reach out to a command and control (C2) server to retrieve a list of multiple payload URLs. These URLs offer the malware redundancy in the case that a single server has been taken down. In many cases, during this process, the dropper will also utilize a common IP checker website to retrieve the public IP address of the victim. The final step of the dropper is to utilize the payload URLs previously retrieved to make a programmatic request out to stage down the full Emotet payload. This request is performed using native windows scripting languages which results in a minimal set of headers and the response content containing a Windows PE file.
GET /aDAffHe/ HTTP/1.1
Host: <DOMAIN>
HTTP/1.1 200 OK
Date: <DATE>
Content-Type: application/octet-stream
Transfer-Encoding: chunked
Connection: keep-alive
Server: nginx/1.15.5
X-Powered-By: PHP/7.2.8
Expires: <DATE>
Last-Modified: <DATE>
Cache-Control: no-store, no-cache, must-revalidate, max-age=0
Cache-Control: post-check=0, pre-check=0
Pragma: no-cache
Content-Disposition: attachment; filename="TfgVHhYfgF.exe"
Content-Transfer-Encoding: binary
d47
MZ......................@............................................. .!..L.!This program cannot be run in DOS mode.Figure 2: Example request showing minimal request headers resulting in a executable download over HTTP.
Emotet’s C2 Activity
Emotet’s malware communicates using the HTTP protocol to egress a network by appearing as normal browser activity. However, the malware uses encrypted payloads inside the HTTP protocol to allow the actors to evade direct network monitoring of their communication activity. Hardcoded within the payloads are the ever changing C2 lists and necessary ports to avoid detection and provide redundancy. Oddly enough, Emotet does communicate over ports such as 22 and 443 where unencrypted HTTP transmissions are not common and yet still often evades detection.
Emotet’s C2 behavior is noisy, with active communication attempts in the order of every one to two seconds to varying C2 server URLs. Compromised host machines will cycle through C2 server lists in a round-robin fashion. Most often, Emotet uses C2 servers within Residential ISP IP blocks.
GET / HTTP/1.1
Cookie: 94852=<ENCRYPTEDDATA>
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/7.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; .NET4.0C; .NET4.0E)
Host: <IP>:443
Connection: Keep-Alive
Cache-Control: no-cache
HTTP/1.1 200 OK
Server: nginx
Date: <DATE>
Content-Type: text/html; charset=UTF-8
Content-Length: <LENGTH>
Connection: keep-alive
<ENCRYPTEDRESPONSE>Figure 3: Example HTTP Request and Response headers of Emotet on port 443.
Emotet’s Lateral Activity
Emotet achieves its primary lateral movement activity by using the stolen passwords it has accumulated to brute-force internal network resources. Emotet will first enumerate the network to identify systems with SMB (server message block) open and accessible. It will then attempt to authenticate to the discovered systems using the credentials stolen by Emotet’s credential theft module. If successful, the malware will copy over a malicious tool and install it as a service on the remote host. The service, upon launching, will write Emotet to disk and continue with the standard infection process. These secondary infections will continue to carry out Emotet’s objectives as well as spread other threats.
In the above scenario, security professionals with pervasive network visibility to east/west traffic would be able to observe a one-to-many pattern of attempted authentications with frequent failures and occasional successful authentications, followed by services being created over the network.
Microsoft Service Control,
CreateServiceW Operation: CreateServiceW (12)
Policy Handle: OpenSCManagerW(LAB\)
Service Name: htysa7fegcthye_wd8sad09de1xad1w4d_h2eefhtfca11vjkszcdbz__2sd6dgs
Display Name: htysa7fegcthye_wd8sad09de1xad1w4d_h2eefhtfca11vjkszcdbz__2sd6dgs
Access Mask: 0x000f01ff
Service Type: 0x000f0000
Service Start Type: (2)
Service Error Control: (0)
Binary Path Name: C:\WINDOWS\htysa7fegcthye_wd8sad09de1xad1w4d_h2eefhtfca11vjkszcdbz__2sd6dgs.exe C:\WINDOWS763t8ah99t3l2_hedagrh8fgrxwfrhdsc9fcstgjsvd16dagr8dhhds_21d1jl.exe
NULL Pointer: Load Order Group
Tag ld: 0
NULL Pointer: Dependencies
Depend Size: 0
NULL Pointer: Service Start Name
NULL Pointer: Password
Password Size: 0Figure 4: Example CreateServiceW RPC call details based on observed Emotet behaviors.
DETECTION AND MITIGATION ACTIONS
Gigamon ATR recommends that detection and mitigation strategies take into account adversary behavior across the kill chain and be diverse in their approach, taking advantage of known atomic indicators, simple behaviors, and complex analytics. For this blog, ATR has scoped the focus of detection to be on network activity.
It is critical to note that by performing detection on techniques associated with a threat, you often take advantage of an economy of scale and gain detection coverage over threats that share and recycle similar techniques.
Installation:
- Executables retrieved with minimal HTTP headers: It is common among crimeware families to stage follow-on malware using barebones scripting-language capabilities native in the operating system. The programmatic retrieval of binaries over plaintext looks significantly different than normal web browsing behavior and can be detected.
- Public IP address check: While not unique to malware, the observation of a public IP check clustered with other suspicious behavior could potentially elevate the confidence of interest.
Command and Control:
- IoCs: Signature-based detection of known Emotet indicators:
- Known identified C2 proxies
- Format and specific indicators associated with network traffic
- HTTP communications over non-standard ports: Emotet communicates out over ports generally reserved for other protocols and ports.
- High volume and periodic communication to low reputation host: The regular communication to foreign residential ISPs on common ports used by internet services.
Actions on Objectives and Lateral Movement:
- One-to-many authentication failures: Authentication failures—identifying credential brute forcing.
- Service creation with suspicious or unknown binaries: Remote service creation should be performed only by administrators from authorized locations. Unknown binaries being executed using remote services from unauthorized hosts present a unique detection opportunity.
Conclusion
It is critical that as an industry, we continue to increase the costs for attackers and dismantle their ability to operate. While intelligence on Emotet activity is abundant, it is only good if actioned by organizations in an effective manner. The ability to action intelligence is dependent upon an understanding of the artifacts produced by the threat, visibility into the “field of play,” and the ability to leverage processes and technology to discover and detect the threat.
Stay tuned for the next blog on Lokibot.