Three New Features — and Key Benefits — in the New GigaVUE-OS 5.5 Release
The new year means new beginnings — and with the new GigaVUE-OS 5.5 release this means three new features you’ll want to know about:
- Gigamon Resilient Inline Protection (GRIP™) Now Facilitates the Implementation of Inline Threat Prevention Tools Within Resilient Network Architectures and Solves the Security Blind Spot in Asymmetric Routing
- Fabric Maps (a Feature Included With GigaVUE-FM) Now Enables Mapping of Traffic Flows Across Clusters to Scale Network Visibility Across Hundreds of Nodes
- Centralized and Reduced Components in GigaSECURE® Cloud for AWS and Azure
Below, you’ll find details on each feature and how they can help you manage your network and security. Also, be sure to read on to the end for more information on GigaVUE-OS.
#1. Gigamon Resilient Inline Protection (GRIP) Now Facilitates the Implementation of Inline Threat Prevention Tools Within Resilient Network Architectures and Solves the Security Blind Spot in Asymmetric Routing
As more tools move from an out-of-band detection mode to an inline active protection mode, network resiliency becomes a particular concern. Inline security appliances, however, represent potential points of failure in the network. Whether due to a power outage, software malfunction or processing bottleneck, failing inline tools can disrupt the very applications and services they are meant to protect. Moreover, redundant network architectures are designed to be fault-resilient, but they present their own challenges when it comes to inline inspection of traffic.
GRIP (Gigamon Resilient Inline Protection) is a resilient inline architecture that utilizes the GigaVUE® HC Series nodes to address these concerns as part of the Gigamon Security Delivery Platform. GRIP leverages both inline tool redundancy and bypass protection to optimize network uptime without sacrificing security.
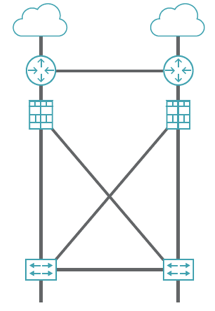
Multi-Path Architectures
A common way to achieve network resiliency is with active-active network configurations. These multi-path architectures form a bow-tie shape, as shown in Figure 1.
Figure 1. Bow-tie (multi-path) architecture
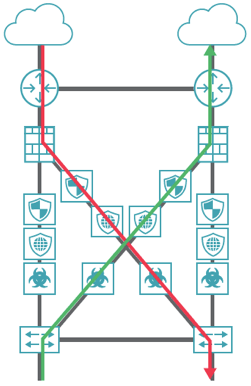
Active-active configurations pose challenges for threat prevention and detection because of the increased number of paths that need monitoring, as shown in Figure 2. In this example, there are four different paths that network traffic can follow, based on what is the best route available, or what has the best bandwidth available to it.
Figure 2. Redundant network architecture where asymmetric routing leaves tools blind
If you deploy inline threat prevention tools along these lines, the proliferation of tools can quickly get costly. The more network routes you need to protect, the more tools you need to deploy. However, sending multiple network paths through a single inline tool without bypass protections voids the notion of redundancy and may send the tool more traffic than it can reliably process.
In active-active networks, asymmetric routing leaves your tools blind. Suppose you have incoming traffic that follows the red line in Figure 2, and it goes down to servers deeper in the network.
Now suppose the return traffic from the server goes up the green line. Now you can see that the tools connected on the red line don’t see traffic going on the green line (and vice-versa). Lacking visibility into the whole sessions, the tools will usually ignore the traffic and any threats contained therein.
This means that the routing architecture created because it was the most efficient way of keeping your network up and running and stable is actually hurting your security. Worse, this could be happening without your knowledge. Security teams especially should be aware of this situation with asymmetric routing.
The way to fix this is to deploy a fully redundant model, as shown in the Figure 3. You will have one side of the network protected by the inline GigaVUE HC Series node and its tools, and the other network protected by a second HC Series node and its tools.
Figure 3. Fully redundant network architecture that addresses asymmetric routing
Notice the two inline HC Series nodes are connected as traffic flows between them the same way as the traffic flows between the switches and firewalls above them. This allows the tools to be shared across the redundant network paths. The tools on the left can be looking at traffic coming from either side of the network, as can the tools on the right.
#2. Fabric Maps (a Feature Included With GigaVUE-FM) Now Enables Mapping of Traffic Flows Across Clusters to Scale Network Visibility Across Hundreds of Nodes
If you’re not yet using Fabric Maps with GigaVUE-FM now is the perfect time to start. Why? Because you can now map traffic flows across clusters to scale network visibility across hundreds of nodes.
As seen in Figure 4, Fabric Maps benefit you by:
- Enabling end-to-end mapping of traffic flows across clusters and/or standalone nodes, thus scaling network visibility across hundreds of nodes
- Automating orchestration of local maps between nodes and clusters
- Supporting various topologies (standalone/cascade, normal and leaf-spine cluster)
- Reducing operator time for configuration troubleshooting and Mean Time To Resolution (MTTR)
- Reducing operating expenses
Figure 4: Fabric Maps orchestration across nodes and clusters
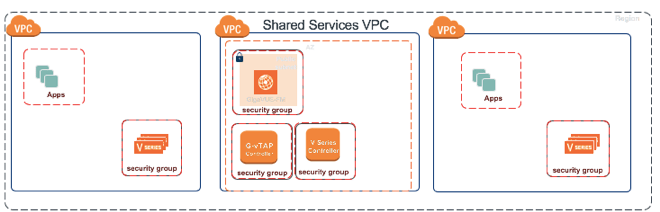
#3. Centralized and Reduced Components in GigaSECURE Cloud for AWS and Azure
The benefits of the new GigaSECURE Cloud architecture for you are (see Figure 5):
- Reduced complexity and operating costs for implementing GigaSECURE Cloud for AWS and Azure
- Eliminated the need for a V Series Controller and a G-vTAP Controller in every Virtual Private Cloud (VPC) and can be shared across VPCs saving implementation time resources
Figure 5: Optimized GigaSECURE Cloud architecture that reduces operating costs
How to Learn More
Check out these resources to learn more about GigaVUE-OS and these recent enhancements:
- Gigamon Resilient Inline Protection (GRIP) Architectural Overview
- GigaVUE-FM
- GigaSECURE Cloud web page
If you have questions, please contact us.








 Sam Kumarsamy
Sam Kumarsamy