Key Takeaways from Black Hat USA 2018
Black Hat USA 2018 attendance was as strong as ever with hightened interest and energy levels present in the briefings, trainings and exhibit floor. After attending briefings and meeting with customers, here are some key takeaways from this year’s conference.
#1. In-Line Bypass and SSL Solutions Are Top of Mind
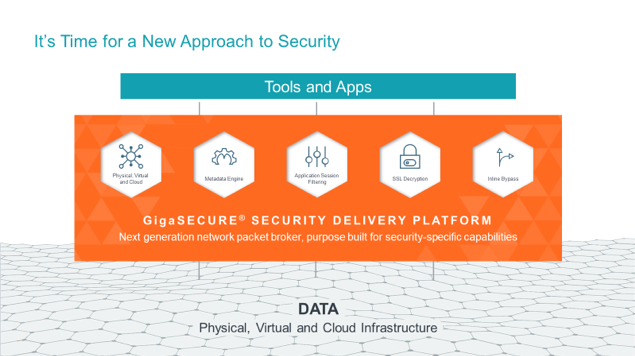
The value of the GigaSECURE® Security Delivery Platform resonated amazingly well with attendees. In particular, the GigaSECURE Inline Prevention solution is compelling to customers for the resilience, flexibility and agility it delivers to their in-line ATP, IPS and WAF tools.
Our SSL Decryption capability also garnered a lot of attention. Many customers told us there was an increasing proportion of encrypted traffic in their networks, presenting an enormous blind spot and vulnerability that can be exploited by hackers to infiltrate networks and exfiltrate data.
The GigaSECURE Security Delivery Platform delivers SSL decryption capability that feeds tools with unencrypted packets for threat analysis and supports both in-line and out-of-band deployment. A key benefit is decrypting once and then feeding multiple tools to achieve greater efficiency. Offloading CPU-intensive SSL decryption from the tool significantly improves performance and efficiency and allows the tool to spend more time on packet inspection and threat detection.
#2. Customers Recognize the Power of Network Data
Many customers see the immense value of network data, which can provide insights into the geo-location, application, user and device context of network communication flows. These key attributes are progressively being leveraged for real-time threat detection and response, as well as compliance and forensics or historical analysis.
Network data comes in three major variants — including flow data such as NetFlow summary reports; metadata that offers more detailed summary information with application summary data; and raw packets — each with their own benefits and tradeoffs. A general purpose log collection tool, such as a SIEM platform from Splunk or IBM QRadar, has the ability to ingest and store this network data in all formats.
While seeing the value of the network data, these customers are looking for vendors to deliver cost-effective and scalable solutions to harness the rich value of the network and derive insights from the vast amounts of network data. All of this data is stored in a data repository that provides a persistent and historical perspective of the network data.
The historical look-back capability of these data repositories is key to detecting advanced persistent threats that are now characterized in the industry by long dwell times ( >100 days) in a typical enterprise. Being able to roll back the clock and piece together the sequence events or clues that form a trail of a multi-stage attack chain is a huge advantage for teams performing security incident investigation and threat analysis.
Today’s malware is designed to evade detection by endpoint protection solutions installed on servers. While endpoints can be compromised, the network is an independent and unbiased periscope into all activity.
Network data is easily accessible and represents a single source of truth providing the critical context in which to detect and respond to threats effectively. It also helps with alert prioritization and severity characterization by correlating it with other IoC (Indicators of Compromise) present in log and telemetry data. This translates to huge benefits for overburdened SOC teams. If you see it on the network, it really happened.
#3. IoT Is the Next Security Frontier
A few IoT device vendors visited our booth seeking a solution to protect their devices from hackers and cyberthreats. One example was a power management vendor that could remotely control power supplies in industrial environments. Many of the conference briefings explored IoT vulnerabilities and exposed successful hacking experiments on actual IoT deployments.
Network data analysis plays a key role in securing IoT solutions, where the gigantic array of IoT devices presents a vulnerable attack surface and blind spot that can be easily compromised due to weak built-in security protections. While IT lacks visibility into IoT devices and cloud components, the network communication flows are readily available and can be monitored, captured and stored in a data store for both real-time analysis and forensic investigations.
#4. Enterprise Defenders Can Win the Security Battle Against Hackers
While some customers needed help seeing network data as a key element of their security architecture, many still need guidance in navigating the overall security landcape, which is increasingly complex and fragmented with the shear number of vendors, tools and approaches.
Each tool offers a point product that addresses a specific use case or threat and is commonly delivered in a purpose-built appliance.The time has come to rethink security with a new approach to tackling the security challenges.
The GigaSECURE Security Delivery Platform forms the center and foundation of a scalable and cost-effective enterprise security architecture and is geared towards effective and efficient threat detection and response. The platform allows enterprises to unify security applications and eliminate blind spots and partial visibility.
If you didn’t get a chance to go to Black Hat this year or swing by our booth, learn more more about how Gigamon can help you secure your environment at www.gigamon.com. See you at Black Hat USA 2019!