SSL Certificate Metadata: A Fast Track to Better Security
Originally developed by Netscape in the early 90s, SSL quickly emerged as the de facto standard for in-transit data security for websites. Today, every major bank as well as hundreds of thousands of sites—including Google, Salesforce, Dropbox, Facebook—use SSL certificates to authenticate the identity of a server by a client prior to starting an encrypted session. In fact, Gartner estimates that, for most organizations, as much as 40 percent of Internet-bound traffic uses SSL. And in certain verticals, like healthcare, the volume can exceed 70 percent.
A typical SSL certificate exchange might go like this. Via a favorite browser, a user tries to connect to a secure website. He types “https” plus the name of the website, hits enter, and a few error messages appear (e.g., “There is a problem with this website’s security certificate. The security certificate presented by this website was not issued by a trusted certificate authority.”). He decides to ignore the warnings and clicks through until he sees the lock symbol in the browser. Ah, assurance that his transaction is encrypted. Or is it?
For more than a decade, the lock symbol in conjunction with https (i.e., for secure http) has continued to reassure users that their information is less susceptible for interception than if using the less secure http protocol. Sadly, such trust may be misplaced at times. And, in the case above, if he were to continue and enter his credentials, trouble could ensue.
With open source implementations of SSL available from OpenSSL, anyone can create a Web server to conduct SSL transactions. Hackers, who are well aware of this, frequently use SSL as the communications channel between malware on the victim’s computer (often called bots) and their own control center, also called a Command and Control (C&C) Server. Gartner estimates that less than 20 percent of firewalls and 50 percent of Web security devices turn on SSL decryption due to performance implications. As a result, SSL communications get a complete pass in most organizations.
Uncover Certificate Anomalies Quickly and Easily
There is a better way: Gigamon’s SSL Certificate metadata—available as part of the GigaSECURE Security Delivery Platform.
With this latest innovation, organizations can now improve the efficacy of their security tools by extracting relevant certificate metadata from raw packets in their network. The certificate metadata can help them uncover a range of certificate anomalies and identify potentially infected endpoints connecting to malicious servers in a targeted and scalable manner.
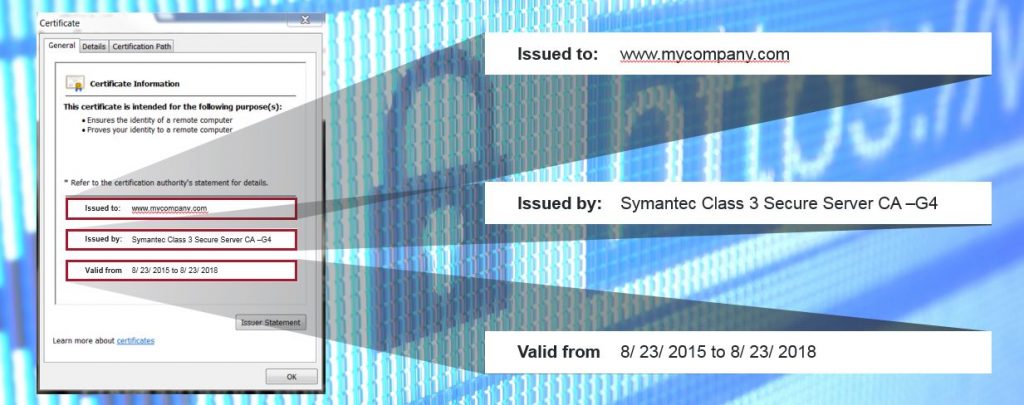
All certificates have an Issuer Field that lists the name of the Certificate Authority granting the certificate. There are only a few reputable Certificate Authorities that sign the majority of certificates. A certificate signed by an authority outside this select list would be of interest to a security administrator. Similarly, self-signed certificates, certificates that have expired, or certificates with very small public key sizes or insecure hashing algorithms may also indicate potentially suspicious behavior and be worth looking into.
Certificates also have a Subject field that indicates who a certificate has been issued to. If a user were to go to a website that hands out a certificate with a Subject field that does not match the URL of the website, this could be a source of concern. Or, if the Subject field were to point to a server that is known to be malicious, this could indicate that clients within your organization are connecting to a suspicious server.
SSL Certificate Metadata is a key element of Gigamon’s Metadata Engine for the GigaSECURE Security Delivery Platform. By generating security metadata, Gigamon gives advanced security appliances, such as SIEMs, critical context with which to better protect networks, applications and data, while simultaneously reducing infrastructure costs and performance overhead. To learn more about SSL Certificate and other metadata extensions, you can visit the Metadata Webpage and view the Certificate Metadata Video.