So Much Data, So Little Time: The Need for Metadata
As enterprise networks continue to grow, so, too, do network speeds. And they’re only going in one direction: up. At the same time, the percent of network traffic consumed by security appliances is going in the opposite direction: down.
While security technologies are capable of complex tasks to detect threats, there’s simply too much data, which, unfortunately, greatly complicates the threat detection process.
Conventional security technologies used to do simplistic matching of suspicious patterns within a large signature database. Today, tools perform more sophisticated tasks—such as machine learning, flock analysis, and virtual machine execution—to unearth anomalous patterns and bad actors. At the same time, as network speeds continue to increase, the mean time between packets has been reduced to 16.7 nanoseconds for a 40G link. That means security tools holding onto a packet must make a decision within that same “split second” timeframe.
Leveraging Network Metadata to Find the Needle in the Haystack
Security appliances are looking for the proverbial needle (i.e., threat patterns) in the haystack (i.e., network traffic).
One way to help reduce the immense volume of data sent to security technologies is to provide, alternatively, a summary of data. Or, in other words, metadata. This “data about data” helps to uncover and deliver more needles—and less chaff—to security appliances.
The benefits of leveraging network metadata include:
- Improved security efficacy. Many security appliances operate at one to a few gigabytes, at most. With network metadata, it’s about getting the essential information to those security tools so they can become more efficient.
- Faster time to detection. Again, by looking at summarized metadata versus raw packet streams, security tools can discover suspicious threats much faster.
- Expanded reach. Security tools often don’t have access to valuable pieces of information like Active Directory, DNS, and DHCP requests. Getting this data from a single place—the network—overcomes that limited reach to improve efficiency.
- Separating signals from noise. Security appliances can confuse signals with noise, making it difficult to determine threats and, too often, producing false positives. Metadata delivers more signals, less noise.
A Tour of Netflow Metadata Enhancements
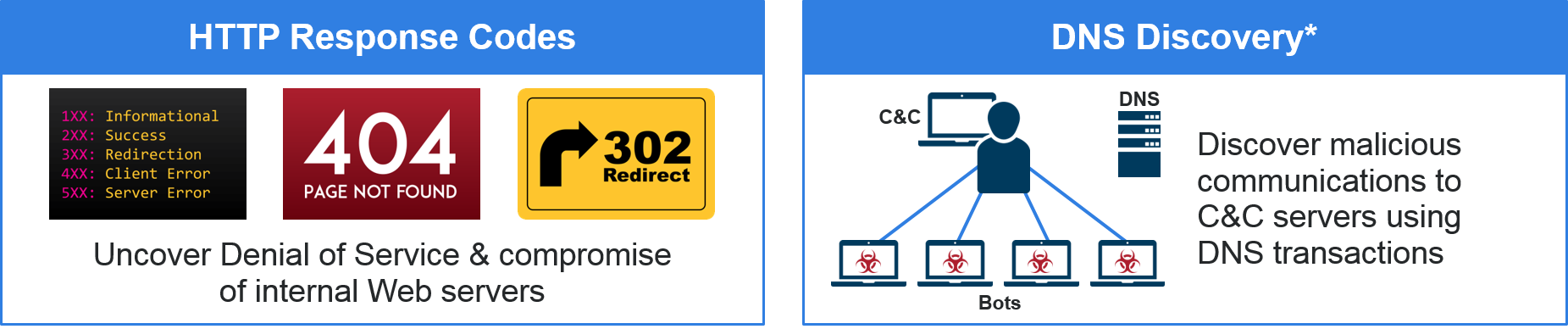
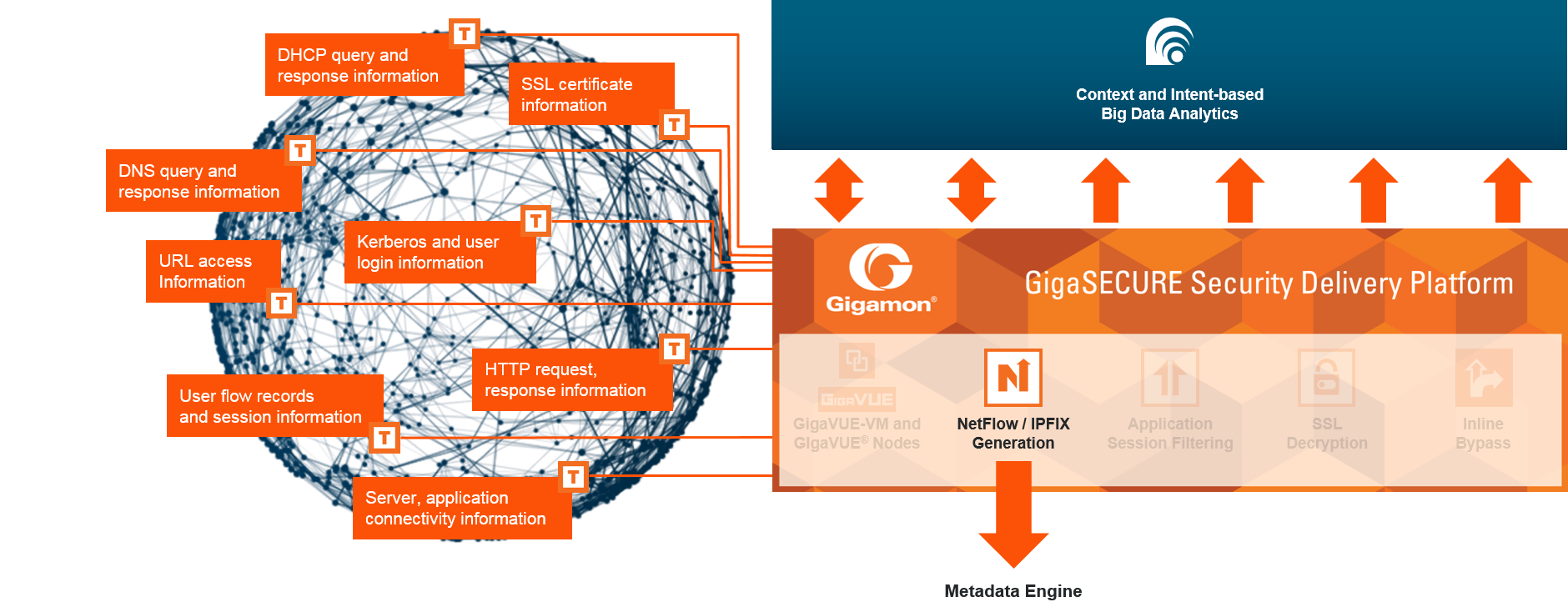
Netflow transports metadata. An easy way to think of it is: Netflow is the bus; and metadata is the passenger. And a few of the types of passengers traveling via Netflow today include URLs, DNS queries, HTTP response codes, or SIP sender/receiver information.
The GigaSECURE Metadata Engine can, for example, extract URLs from HTTP messages, or it can extract HTTP response codes such as 200 OKs and redirects. Organizations looking for potentially infected endpoints or compliance violations simply need to search for a URL in their metadata to identify endpoints that accessed that website. Additionally, they can baseline HTTP response codes to spot deviations from the norm (e.g., too many redirects could indicate a compromise of your internal servers).
Similarly, DNS metadata can provide valuable security clues. If a botnet tries to reach its command and control center (e.g., www.evil.com), the first thing it does is initiate a DNS request to resolve the IP address for the domain www.evil.com. The GigaSECURE Metadata Engine can spot this DNS request and provide the original DNS request and response information as metadata needed for security incident analysis and response.
With the GigaSECURE Metadata Engine, Gigamon has transformed NetFlow generation into a full-blown metadata engine. The new metadata engine, which sits inside the GigaSECURE Security Delivery Platform (SDP), serves as the single source of network truth for all kinds of information about applications, users, and devices, and sends relevant information to all of the security tools connected to the SDP.