What Is NetFlow?
Last updated March 1, 2023.
What is NetFlow and how is it used? How do IT professionals use the NetFlow protocol? And how does Gigamon eliminate risks using NetFlow data? Here, we answer those questions and show you how you can put it to work for your business.
What Is NetFlow?
NetFlow is a network protocol system created by Cisco that collects active IP network traffic as it flows in or out of an interface. The NetFlow data is then analyzed to create a picture of network traffic flow and volume — hence the name: NetFlow.
The NetFlow protocol is used by IT professionals as a network traffic analyzer to determine its point of origin, destination, volume and paths on the network. Before NetFlow, network engineers and administrators used Simple Network Management Protocol (SNMP) for network traffic analysis and monitoring.
While SNMP was effective for network monitoring and capacity planning, it didn’t provide detailed insight into bandwidth usage. NetFlow is now part of the Internet Engineering Task Force (IETF) standard as Internet Protocol Flow Information eXport (IPFIX, which is based on NetFlow Version 9 implementation), and the protocol is widely implemented by network equipment vendors.
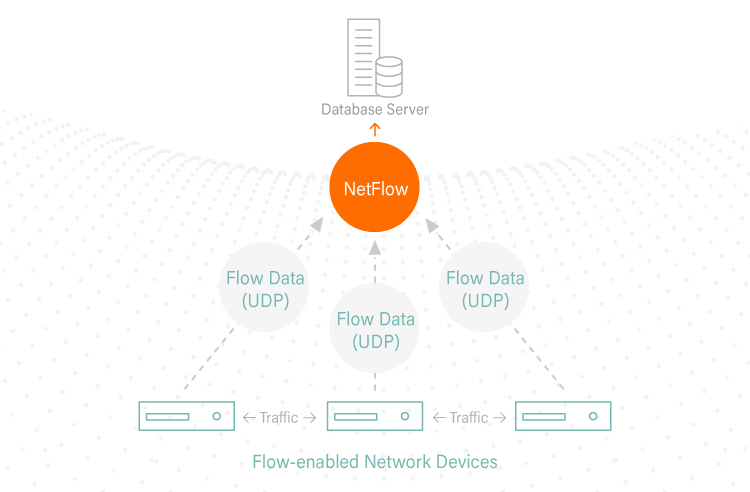
How Does NetFlow Work?
NetFlow follows a simple process of data collecting, sorting and analysis. The main components include:
IP Flow
An IP flow consists of a group of packets that contain the same IP packet attributes. As a packet is forwarded within a router or switch, it is examined for a set of attributes, including IP source address, IP destination address, source port, destination port, Layer-3 protocol type, class of service and router or switch interface.
NetFlow Cache
The NetFlow cache is a database of condensed information where NetFlow data is stored once the packets have been examined.
Command Line Interface
The Command Line Interface (CLI) is one of two NetFlow connection methods to access NetFlow data. It provides an immediate view of your network traffic and is useful for troubleshooting.
NetFlow Collector
The second option to access NetFlow data is to export the data to a NetFlow collector. A NetFlow collector is a reporting server that collects and processes traffic and the exported data so that it is easy to analyze. These NetFlow collectors fall into two categories: hardware-based collectors and software-based collectors, with software solutions being more common than hardware devices.
Why Use NetFlow?
NetFlow statistics are useful for several applications. Among the top advantages of using NetFlow are:
- Network Monitoring: Businesses and users can utilize flow-based analysis techniques with NetFlow to visualize traffic patterns throughout the entire network. With this overarching view of traffic flow, network operations (NetOps) and security operations (SecOps) teams can monitor when and how frequently users access an application in the network. Also, teams can use NetFlow data to monitor and profile a user’s utilization of network and application resources to detect any potential security or policy violations.
- Network Planning: Team can use NetFlow to track and anticipate network growth. For example, with NetFlow they can plan upgrades to increase the number of ports, routing devices, or higher-bandwidth interfaces needed to meet growing demand.
- Security Analysis: With NetFlow, security teams can detect changes in network behavior to identify anomalies indicative of a security breach. The data is also a valuable forensic tool to understand and replay the history of security incidents so security teams can learn from them.
Shortcomings of NetFlow
Although NetFlow provides improved network traffic visibility, planning, and security analysis, it does bring with it certain disadvantages.
Given its inherently high demands on available bandwidth, NetFlow has a performance impact on the devices where it is implemented. To reduce that impact on performance, networking devices often rely on sampling packets (similar to sFlow) to generate NetFlow statistics. Unfortunately, low sampling rates — sometimes as few as one in 1,000 packets — dramatically reduce network visibility and could prevent teams from uncovering critical security threats or performance issues.
Additionally, NetFlow records can only be forwarded to a select number of collectors or monitoring tools. Often, this number can be far fewer than required to properly manage and troubleshoot the network. As businesses face a growing volume of both data and security threats, seeing only a portion of what is happening in the network puts businesses at risk of having insufficient information to combat security threats.
NetFlow and Gigamon
Gigamon eliminates the risks associated with data sampling by running NetFlow statistics in parallel with the raw packet streams. With these processing capabilities, Gigamon users can generate NetFlow statistics either at a much higher sampling rate or even at line rate.
NetFlow generation is typically undertaken by the routers and switches as part of the production network. However, as mentioned above, NetFlow does have a performance impact on the devices where it is implemented. Keeping up with growing data volume and network speeds is a growing concern for most enterprises that are straining to have enough compute resources to match the growing demand.
How does Gigamon address this challenge? Through metadata. While NetFlow provides Layer-4 flow-generated data, organizations also need access to Layer-7 or application-level metadata. The Gigamon Metadata Generation capability, which includes NetFlow, generates both Layer-4 and Layer-7 metadata that is both unsampled and done without impacting performance.
When we implemented this solution here at Gigamon, we saw a reduction in false positives, achieved faster time to threat detection, and leveraged our security team much more effectively. By integrating Gigamon Metadata Generation with our Security Information and Event Management (SIEM) solution, we were able to identify unusual patterns in Hypertext Transfer Protocol (HTTP) response codes, specific domains indicating a possible security breach, and users attempting to reach sites signed by WoSign Secure Sockets Layer (SSL) certs.
NetFlow has been and will continue to be a powerful application for gaining greater network visibility. By offloading NetFlow to Gigamon Metadata Generation, both SecOps and NetOps teams will be able to keep pace with growing data volume and speed without sacrificing the important insights that can be gained from network monitoring and security analysis.
Further Reading:
- “How Pervasive Visibility Reduces Network Downtime in the New Tomorrow”
- “Elevate App Layer Visibility and Control Within Nutanix Hyperconverged Infrastructures”
- “NetFlow/IPFIX Generation from AWS Clouds“
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Networking group.
Share your thoughts today