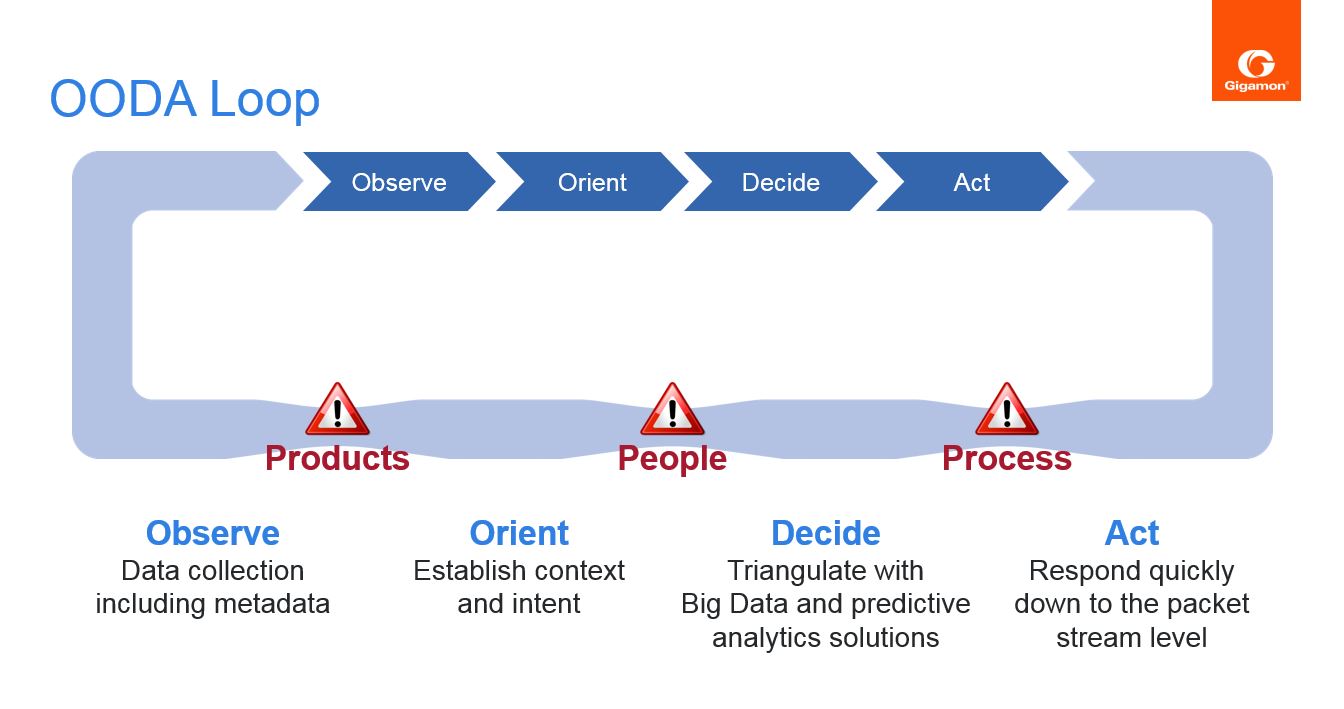
OODA Loop and Security Workflow Orchestration
Recently I came across some material on the application of “OODA loop” as a strategy in the world of cybersecurity. OODA stands for “Observe”, “Orient”, “Decide”, and “Act”, the concept being that adversaries are in a constant cycle of Observing, Orienting, Deciding and Acting. The OODA loop concept was first proposed by military strategist and USAF pilot Colonel John Boyd who observed that the air force pilots are constantly in this loop and the pilot that has the ability to close his loop faster, can disrupt the adversary’s own OODA loop and gain the upper hand. The strategy and philosophy has since been applied to cyber warfare, as defenders and attackers are also in this perpetual cycle of observing, orienting and building situational awareness, and based on that awareness, deciding on a certain course of action. Once that action has been executed, the players go back to building a new situational awareness and this continues endlessly, since an organization’s work as a defender is never done.
What is interesting though is that when applied to organizations that are playing the role of the defender, the ability of the defender to close the loop faster than the attacker is often hampered by organizational silos, processes, and the inability of security products or tools to work in cohesion.
In other words security workflow orchestration is one of the biggest impediments to rapidly closing the loop and disrupting the attacker’s own OODA loop. This typically gives the attacker the upper hand. . As a simplistic example, a security solution that is focused on anomaly or behavioral based threat detection, is designed to generate alerts when a potential abnormality is observed. It may be desirable to immediately start forwarding traffic that matches that profile to a sandboxing solution. However, in today’s world, this requires human intervention as typically there is no automated way for the anomaly based threat detection solution to influence what traffic gets directed towards the sandboxing solution, particularly if they come from different vendors. Worse still, this may require crossing organizational boundaries and processes, since access to network traffic may require intervention on the part of the networking team. As the number of security products and solutions increase, the problem only keeps exacerbating, requiring increased human intervention, and increased cross-functional dependencies to take certain actions. In the meantime, the attacker has already shifted his situational awareness and decision points in a different direction i.e. the attacker has closed his OODA loop faster than the defender, thereby gaining the upper hand.
Restoring speed and efficiency to the cycle requires re-thinking the deployment model for security solutions. In practical terms, the best way to achieve this is to leverage a common platform that unifies the deployment model for disparate security products and provides a conduit for those products to “influence” each other based on each product’s real time, near real time, or post real time analysis. Furthermore, the ability of the platform to isolate and insulate security workflow changes from the networking or applications teams can only help speed up the cycle by overcoming inter-departmental inefficiencies. A security delivery platform provides an ideal solution to addressing both challenges.
 At the heart of the platform is a common set of APIs that allows each security product to not only influence what slice of traffic it receives in real time, but also to influence and change what network traffic other security solutions can see as the situational awareness changes. In other words, adapting to changing conditions and orchestrating security workflows becomes a much simpler exercise with a security delivery platform, and indeed many aspects of this can be automated and free from the inefficiencies associated with crossing departmental boundaries. The more security products that leverage the platform, the greater the benefit of the platform and the common set of APIs that become available to all the security solutions. The combination of a common set of APIs exposed by the security delivery platform, and the ability to change network traffic feeds to security products without impacting the production network traffic or requiring networking operators to schedule maintenance windows, provides a strong foundation for speeding up and optimizing the organization’s OODA loop and ultimately giving the advantage back to the defender.
At the heart of the platform is a common set of APIs that allows each security product to not only influence what slice of traffic it receives in real time, but also to influence and change what network traffic other security solutions can see as the situational awareness changes. In other words, adapting to changing conditions and orchestrating security workflows becomes a much simpler exercise with a security delivery platform, and indeed many aspects of this can be automated and free from the inefficiencies associated with crossing departmental boundaries. The more security products that leverage the platform, the greater the benefit of the platform and the common set of APIs that become available to all the security solutions. The combination of a common set of APIs exposed by the security delivery platform, and the ability to change network traffic feeds to security products without impacting the production network traffic or requiring networking operators to schedule maintenance windows, provides a strong foundation for speeding up and optimizing the organization’s OODA loop and ultimately giving the advantage back to the defender.