Securing the Promise of SDDC Micro-segmentation
SDDCs promise to dramatically increase the security of data centers using NSX micro-segmentation allows you to take advantage of granular security today with design choices that maximize your visibility and give you operational scale.
The Evolution and the Promise
Data center design has been in the midst of revolutionary changes for the last decade. By embracing virtualization and n-tier application design, organizations have been building more dynamic data centers capable of faster scaling for performance, capacity and functionality.
These changes have dramatically altered traffic patterns with the majority of flows now found within the data center or “east-west” traveling among the layers of workloads that execute applications and manage data. The Software Defined Data Center (SDDC) approach with network virtualization increases network and service provisioning agility by orders of magnitude. By abstracting the physical network, the new data center can be organized logically by the business needs and applications that fulfill it. In that construct, critical networking and security services can be provisioned for applications that require them. Firewalling, inspection for intrusion prevention, content inspection and other services make up a security profile that is spun up and applied as the application and its compute are provisioned and wound down when those same resources are no longer required. In the SDDC the ultimate in security is possible. Data center resources are secured at the most granular level, the application, based on the assumption of zero trust or that there is no trusted network boundary. Security services are applied dynamically and pervasively at the virtual layer. This new data center is also the ultimate in flexible design housing a mix of physical and virtualized workloads, different virtualization technologies, and best-of-breed security applications
Where We Are Today
Modern threats target traffic inside the data center. They may enter the data center hiding within authorized devices or traffic streams but once inside they propagate laterally, server-to-server. In theory, security controls and devices can be applied at each data center segment but in reality this is impractical from a scale and performance perspective especially given growing network speeds and traffic volumes. When security is introduced it is rarely pervasive or granular. Also, despite some innovation in this area, the unification of security policies and application control across physical and virtual workloads is simply not a realistic deployment option at least today. As a result data centers remain highly vulnerable and the favorite targets of attackers because they often house an organization’s most valuable data.
Micro-segmentation and the application of granular security controls inside data centers is operationally feasible with VMware NSX today. Application and workload provisioning happen at a high rate, as do errors in this provisioning especially in the virtualized realm. This increases the probability of a data center server or VM becoming infected with malware. And given the absence of security controls and the complexity of traffic flows in the data center, the threat can hide indefinitely and proliferate quickly. Inspection of data center traffic for the presence of malware, nefarious communications and data exfiltration has never been more important. And with micro-segmentation, the discovery of malware in the network means the threat can be contained to a node..
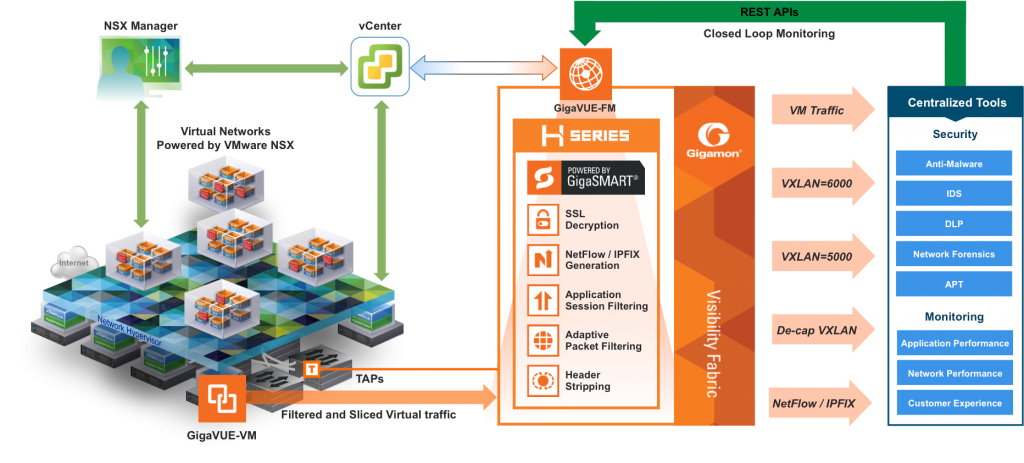
Introducing micro-segmentation and granular security starts with an understanding that while putting security devices on all data center segments is performance prohibitive, ensuring that all traffic flows are security inspected is not. The key is gaining visibility and access to all the packets and traffic flow metadata in the data center in an unobtrusive way, aggregating it and sending it to all of the security applications and controls that the organization requires. A Security Delivery Platform (SDP) is emerging as critical data center architecture for accomplishing just that. By tapping into the physical and virtualized network segments, aggregating packets and grooming them for privacy, tag and application identification, traffic among physical servers and VMs can be sent selectively and at high-bandwidth speeds to threat detection, antivirus, intrusion prevention and data loss prevention systems. This approach ensures that all data center traffic has the same benefit of next generation and advanced threat detection capabilities that are found today in enterprise campus and branch networks.
With VMware’s NSX you’re poised to fully implement micro-segmentation. NSX creates a layer of abstraction above the physical networking infrastructure. Virtual networks are isolated by default, and the NSX Distributed Firewall enables resources to be grouped into “segments”. A Security Delivery Platform (SDP) in this setting is SDDC-ready and able to unify all physical and virtual traffic for security monitoring. To define SDDC-ready further consider that the SDP recognizes VXLAN headers and can forward traffic to the appropriate tools based on the security policy for that VXLAN. Also by stripping off the header, the traffic can even be forwarded to those security devices that are not SDDC-ready but nonetheless can provide advanced security inspection and detection capabilities for IP-based traffic. The SDP even includes application awareness so that traffic of a particular type like email or web can be forwarded to specialized gateways offloading them from the computationally taxing task of discarding irrelevant traffic.
As services are provisioned, workloads motioned and topologies expanded, the traffic aggregation and forwarding policies adjust automatically serving as a layer of constant visibility and oversight.
Stay tuned for more detail and sample architecture designs in future posts.
To see an example of the Security Delivery Platform providing unifying access to all physical and virtual traffic for security monitoring see our joint solution with RSA “Securing the Software Defined Data Center” solution brief.