Dude, Who Are My Applications Talking To?
Updated October 14, 2021.
“We don’t know what apps are talking to each other,” said a worried IT professional at the Gigamon booth during a major conference in Las Vegas in 2019. His team’s main concern was that in their complex multi-tiered environment, services were provided through application components talking to other applications through API calls.
The team, however, was completely blind to this inter-application communication. Gaining full visibility was therefore critical in ensuring the applications were secure and performing to the levels of expectation. They also wanted to know what part of the application relationship was the “Achilles’ heel” when a service went down. Without visibility, securing the applications or troubleshooting outages were difficult tasks.
Fast-forward to 2020, where we find ourselves in a more complex working environment with many more employees working from home. Companies have been forced to accelerate their digital transformation efforts to stay viable. And Microsoft CEO Satya Nadella recently said: “We have seen two years’ worth of digital transformation in two months.”
Furthermore, users comprise not just the employees of a company, but also partners, customers and bots. Users are also using their own devices with an explosion of cloud apps across wireless and wired infrastructure. And as if that were not enough, IoT devices are making their own API calls for the services they are providing. Applications are no longer monolithic but composite, and are always evolving with any new digital transformation needs. Application architecture is becoming more complex, with restful APIs enabling companies to integrate across different physical, virtual, private or public cloud environments. Application traffic no longer has a perimeter. Given all that, it has become imperative to not only discover what applications are in an environment, but also to find out what communication is taking place under the hood at the application level.
But that can be possible only if someone has complete visibility of all network assets across any networking environment. It requires capturing all application traffic across all physical and virtual infrastructure without leaving any blind spots, and then running analytics to discover a holistic view of inter-application communications.
For this very complex problem, Gigamon, a world leader in visibility and analytics space, has teamed up with vArmour, the leader in application relationship management. Together, we now provide a comprehensive and pervasive application relationship management solution for customers across any environment, including physical, public cloud, hybrid cloud, private cloud or virtual — for unprecedented visibility and control of applications across infrastructure.
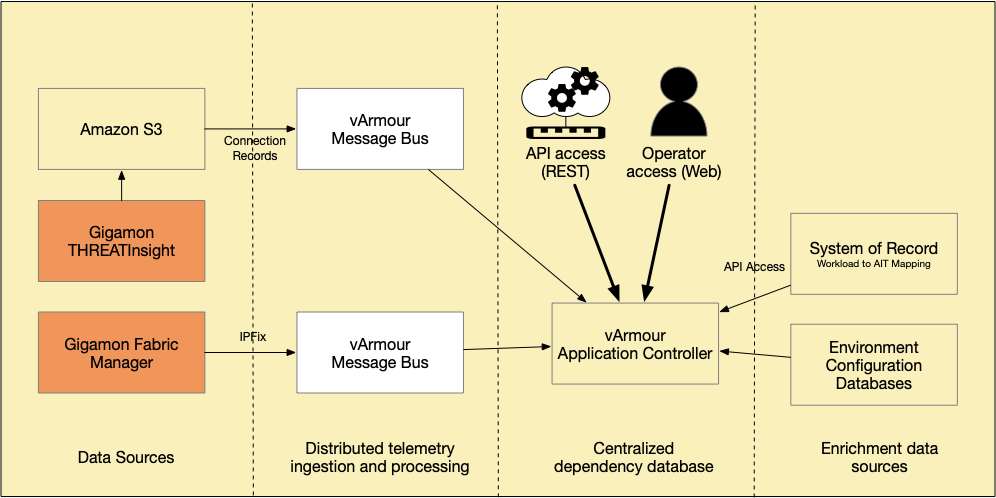
Gigamon ThreatINSIGHT™, a network detection and response SaaS solution, collects network traffic for threat detections. During this process ThreatINSIGHT sensors generate flow data and identify Layer 7 applications using metadata inspection, rather than assuming the application based on the destination port. By doing this identification, vArmour Application Controller can accurately report the type of traffic between application relationships.
Finally, the flow data generated by ThreatINSIGHT is stored in an AWS S3 bucket, where it is then collected and ingested by the vArmour Application Controller — bringing rich new telemetry and insights into vArmour’s Relationship Graph. vArmour uses this and other data to create rich maps of all your applications, regardless of environment or location, enriching the reach of visibility and control of applications.
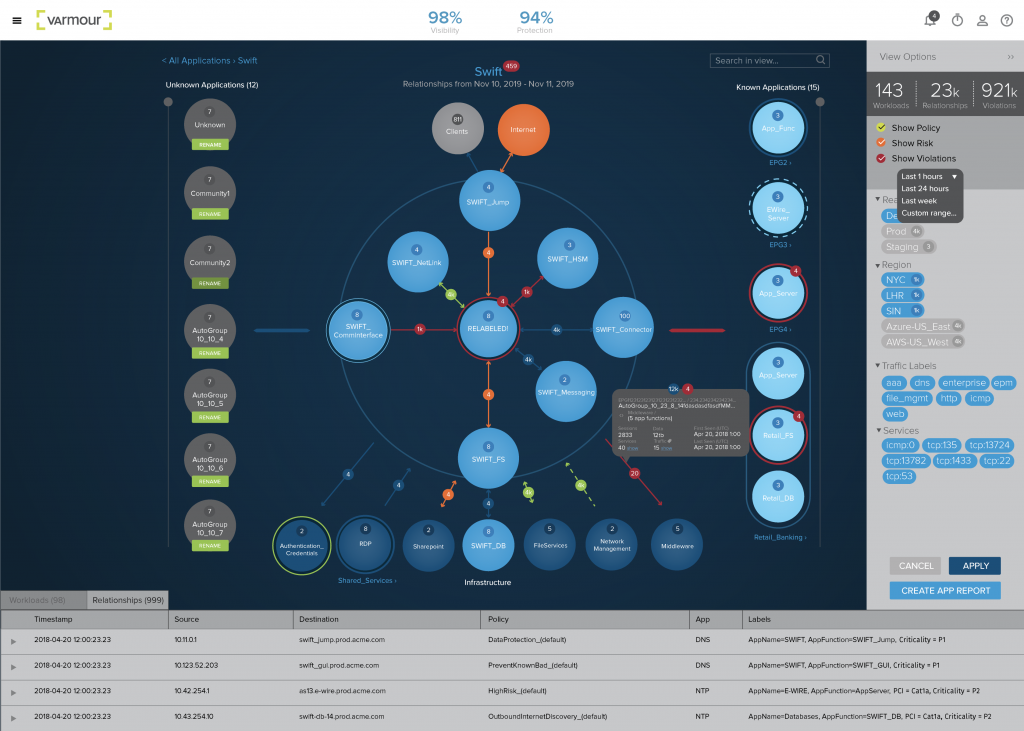
Gigamon and vArmour provide an industry-leading solution for unprecedented visibility and control across network infrastructure with the joint integration of ThreatINSIGHT and Application Controller, critical to the security of diverse enterprise IT and security environments. Used together, vArmour and Gigamon enable both Operations and Information Security teams the ability to operate, detect and respond, and optimize their application environments for minimized risk.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Networking group.
Share your thoughts today








