Leveraging Application Metadata Intelligence to Identify CVE-2024-3400: MidnightEclipse, CVE-2024-20353 and CVE-2024-20359: ArcaneDoor
*Updated April 26, 2024, to include details on CVE-2024-20353 and CVE-2024-20359.
The goal of this blog is to offer Gigamon customers guidance on how they can leverage the observability Gigamon Application Metadata Intelligence (AMI) provides to enhance best practices in their organizations. We will cover recent challenges, tactical elements for CVE-2024-3400, CVE-2024-20353, and CVE-2024-20359, as well as best practices for AMI metadata that go beyond any specific incident.
The Problem
On Friday, April 12, Palo Alto Networks published an advisory for a CVSSv3 severity 10 zero-day vulnerability of several PAN-OS versions PAN-OS 10.2, PAN-OS 11.0, and PAN-OS 11.1, the operating system for Palo Alto Networks (PANW) firewalls, which has been under exploitation for at least two weeks. This is an example of an attack on firewalls, email appliances, managed file transfer facilities, and other IT infrastructure which were not traditional targets for adversarial attention and is part of a broader trend where threat actors have been focusing less on attacking servers and endpoints–both of which have received much security attention in recent years–and are moving on to attacking appliances, infrastructure, and services to evade detection.
This recent attack has exposed a severe vulnerability, formally known as CVE-2024-3400, in Palo Alto next-generation firewalls (NGFW). This vulnerability facilitates the installation of code into the firewall, including backdoors and other malicious software, without any authentication. Using such code, attackers can execute lateral movement that bypasses the firewall and could potentially penetrate the organization. Affected versions of firewall software cannot self-detect these intrusions, making network telemetry crucial for identifying breaches. Currently only one threat actor group, generically known as UTA0218, has been publicly documented exploiting this vulnerability. But now that the vulnerability’s existence and general nature are publicly known, it is likely that others may leverage the details and create exploits.
On Wednesday, April 24th, Cisco Talos released a notice about a state-level threat campaign dubbed ArcaneDoor that is targeting Cisco Adaptive Security Appliances (ASA) and Firepower Threat Defense (FTD) appliances. It appears most appliances with AnyConnect IKEv2, AnyConnect SSL VPN, or http server running are vulnerable. This campaign has been attributed to UAT4356 with unknown affiliation. Specifics can be found on the Talos blog.
What Is Gigamon Application Metadata Intelligence?
Gigamon Application Metadata Intelligence (AMI) empowers observability, security information and event management (SIEM), and network performance monitoring tools with critical metadata attributes across thousands of business, consumer, and IT applications and services. This helps rapidly pinpoint performance bottlenecks, quality issues, and potential network security risks. Application Metadata Intelligence expands upon application layer visibility derived from Gigamon Application Visualization and Filtering and supports a comprehensive approach to obtaining application behavior. Whether organizations deploy their workloads on-prem or in the cloud, they can acquire critical details about flows, reduce false positives by separating signals from noise, identify nefarious data exfiltration, and accelerate threat detection through proactive, real-time traffic monitoring and troubleshooting forensics. AMI uses deep packet inspection to provide summarized and context-aware information about raw network packets based on Layers 2–7. It enables tools to measure performance, troubleshoot issues, spot security events, and improve effectiveness.
Identify Indicators of Compromise (IoCs) Specific to this Vulnerability
Using AMI, you can detect traffic targeting a network device, such as a firewall, as well as outbound traffic originating from it. In this use case, you will look for traffic that is targeting or originating from the NGFW, including:
- Proxy traffic over standard and non-standard ports.
- SSH on port 31289. (The threat actor has displayed flexibility in using different ports/protocols.)
- SOCKS5 traffic on port 8123. (Note again that this is a non-standard port, as SOCKS5 is usually on port 1080.)
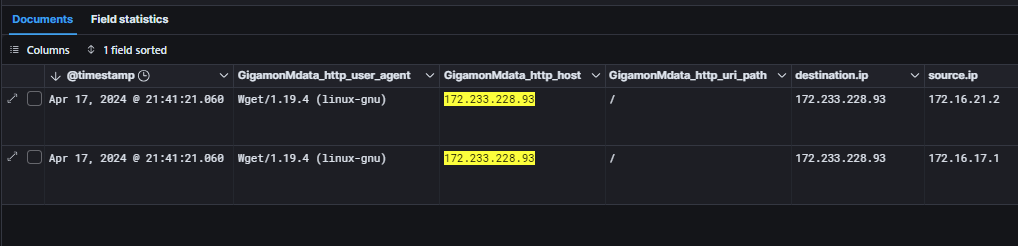
- A wget request using HTTP on port 80 to the URL http[://]172.233.228[.]93/policy every 60 seconds or so. As of the time of writing, nothing will be returned from this address.
- NGFW initiating outbound SSH to 172.233.228[.]93.
- HTTP request for the URL worldtimeapi[.]org/api/timezone/etc/utc originating from the Global Protect appliance.
Identify Indicators of Compromise (IoCs) Specific for Arcane door
Gigamon AMI is able to see all certificates and the values of the fields making it possible to identify the self-signed certificates. Additional certificate values to search for when tapping the external interface are:
Certificate Pattern:
:issuer = O=ocserv,CN=ocserv VPN
:selfsigned = true
:serial = 0000000000000000000000000000000000000002
:subject = O=ocserv,CN=ocserv VPN
:version = v3
CPE Identifiers:
cpe:2.3:a:cisco:http:*:*:*:*:*:*::
cpe:2.3:h:cisco:adaptive_security_appliance:*:*:*:*:*:*:*:*
cpe:2.3:o:cisco:adaptive_security_appliance_software:*:*:*:*:*:*:*:*
Look at East-West Traffic Within Your Network
Things to look for inside the network:
- SMB/RDP connections to multiple systems across the environment originating from the GlobalProtect (NGFW VPN) appliance
- SMB file transfers of Google Chrome or Microsoft Edge browser data or the ntds.dit file
General Best Practices
These are some best practices we recommend with AMI, whether pre- or post-breach, for this vulnerability and other attacks, such as ransomware and data exfiltration.
- Have visibility into traffic to the VPN address feeding a network detect and response (NDR) tool. This especially applies if the NDR tool provides forensic recording capability and helped identify anomalous behavior corresponding to the attack. Even if it didn’t detect the initial attack, an NDR can retroactively confirm the presence of the IoC, forensically confirming that you have been subject to an attack.
- Get access to East-West traffic. Even in internal environments that are macro- or micro-segmented, this could detect anomalies corresponding to post-exploitation lateral movement. Fundamentally, network segmentation degrades the ability for an attacker to move laterally, it does not prevent it completely. As it can also blind visibility into typical attacker TTPs when confronted by a segmented environment (e.g. exploratory port scans), segmentation without visibility may have reduced your security posture, not enhanced it.
- Record all nonstandard port traffic. This is a common attack technique, and classic network logging is unable to identify it, meaning investigators must rely on outside telemetry from endpoint detection and response (EDR) and other sources.
- Inspect deeper than logs. Syslog will report, “A talked to B over web traffic.” Application Metadata intelligence will say, “A established a SSH connection over standard SSL web traffic (port 443).”
- Assume compromise. Build security architecture with the assumption that any part can be compromised and be resilient enough to maintain an adequate security posture despite that compromise. This also includes all infrastructure, IoT/OT, ICS/SCADA, legacy compute, BYOD devices, containers, shadow IT, and so on. Special care should be taken to understand and track all infrastructure, not just the infrastructure your IT department is responsible for.” While IT may not be able to access the device, it can and must be monitored by observing its network behavior. The use of layered defensive infrastructure through defense in depth is a core requirement. This concept is implicit in Zero Trust, with its central tenet of denying implicit trust in anything.
- Monitor all network traffic—including encrypted traffic. If anything can be compromised, wargame the scenario, and ask yourself “How could I detect that?” If you can’t, this is a risk you need to manage. Solutions such as Gigamon Precryption™ technology can offer plaintext visibility into all encrypted communications before the payload is encrypted so you can monitor all traffic.
- Deploy decryption North-South and East-West. Gigamon has robust high-speed decryption capabilities that can reach far into the network, expanding traditional North-South deployments. While Gigamon notes no reported use of encryption as an evasion technique in the current attack, one of the characteristics of any adversary is to evade detection. Encryption is a good way of doing this, making decryption an essential strategic imperative to facilitate.
Conclusion
Deep observability can greatly aid in detection, forensics, and remediation for many problems ranging from performance, outages, or compromise. Any enterprise can benefit from detecting traffic originating from or to network appliances and subsequent visibility of lateral movement by adding decryption and application and protocol visibility to network logging. Since the visibility is external to the compromised system, it’s extremely challenging for an attacker to evade it, as it’s outside of the blast radius of their compromise. This means behavior is observed, recorded, and logged outside the device regardless of its state. Appliances experiencing congestion or compromise may not accurately or completely log; routers and firewalls are often single sources of truth. External observation and metadata-enriched logging can help meet many security and Zero Trust requirements.
To learn more about AMI, visit the webpage, read the data sheet or tech brief, or request a demo.
If you are a current Gigamon customer and need help with optimal tap placement for firewalls or turning on the correct detections, you can contact support or submit a ticket in the Gigamon VÜE Community.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today