Do You Have an Application Visibility Gap?
The Application Visibility Gap
With organizations caught between conflicting demands of doing more with less, developing new apps to support the business, and ensuring all critical assets, data, and processes are secure, it’s no surprise that many struggle to know exactly what’s running on their hybrid network.
In many cases, it’s accurate to say that there’s a gap between the applications IT and Security have authorized to be on a network and the reality of the apps actually on the network. Eliminating this gap is a major challenge for many organizations, but they must resolve it to ensure security, maintain network efficiency, and contain costs.
Five Factors That Drive the Application Visibility Gap
While contributing factors will vary for each organization, there are many economic, business, and technical reasons that allow this gap to develop. Here are five such reasons:
- Changing and accelerating business needs – Applications, whether SaaS-based or custom developed, are constantly changing in response to business needs. And the rate of change is accelerating, especially with customer-facing applications that enable your organization to differentiate and respond to competitive pressures in your market.
- Well-meaning but misguided users – Many lines of business units — or even technically capable individuals — may respond to these needs by deciding to go it alone and deploy a new SaaS app or engage a DevOps team to solve a pressing problem without IT and Security oversight. While this can be understandable, it carries significant risk.
- The pressure to do more with less – Almost all IT and Security teams are being asked to freeze or contain costs in 2023. That, combined with continuing staffing and skills shortages across all sectors, makes it increasingly difficult for organizations to monitor and prevent the application reality gap from developing and widening.
- Bad actors outside and inside the organization – Besides external risks from criminal and state-sponsored actors planting ransomware and other malware, such as crypto mining, on corporate networks, many undertrained, careless, or malicious internal users contribute to this gap by using unauthorized apps on the network.
- Tools don’t provide enough visibility – Gaining a holistic view of all the applications running on a hybrid or multi-cloud network is a significant technical challenge when each platform has a unique monitoring tool. What’s needed is a way to pull this holistic view together so you can act on the insights provided.
The Application Visibility Gap Creates Risk and Costs You Money
Not knowing exactly what applications are running on your network exposes your organization to a range of security risks and costs you money. Risk issues are easily understood but could include malicious applications, such as ransomware; unauthorized and potentially criminal applications, like crypto mining; and peer-to-peer apps capable of exporting and exfiltrating sensitive data. Any of these applications pose serious financial, regulatory, and reputational risks.
In addition to these risks, running unauthorized applications means your organization is paying for compute power, bandwidth, and potentially storage capacity it’s unable to use to support its operational functions.
How to Close the Application Visibility Gap
To close the application visibility gap, organizations need visibility into all the applications on their networks and the traffic that these applications generate. This means being able to identify all the applications running anywhere within your infrastructure, whether apps are hosted in physical or virtualized data centers (private clouds) or the public cloud.
These applications are often hard to identify and may be named and designed to appear to be legitimate apps, masking their actual purpose. In this case, seeing the protocols and ports the apps are using, identifying the servers they are communicating with, and inspecting the traffic they’re generating may be critical to understanding their true nature.
For over 15 years, Gigamon has been the leader in network visibility, a market segment now being redefined by analysts as the deep or network observability market. Gigamon is the acknowledged market leader in the deep observability market (according to the latest 650 Group Deep Observability report).
In large part, our market leadership is based on our ability to see all the applications on a network and the traffic these applications generate, from the packet to the application level. We call this capability Gigamon Application Intelligence. It enables our customers to visualize all applications running on their network and set up simple rules that specify how application traffic will be managed from an inspection and security perspective. You can set rules up for each application or group applications into categories and then set up rules for entire categories. To accelerate this process, Gigamon Application Intelligence can identify almost 4,000 applications out of the box, and you can extend this by adding your in-house apps to your unique library.
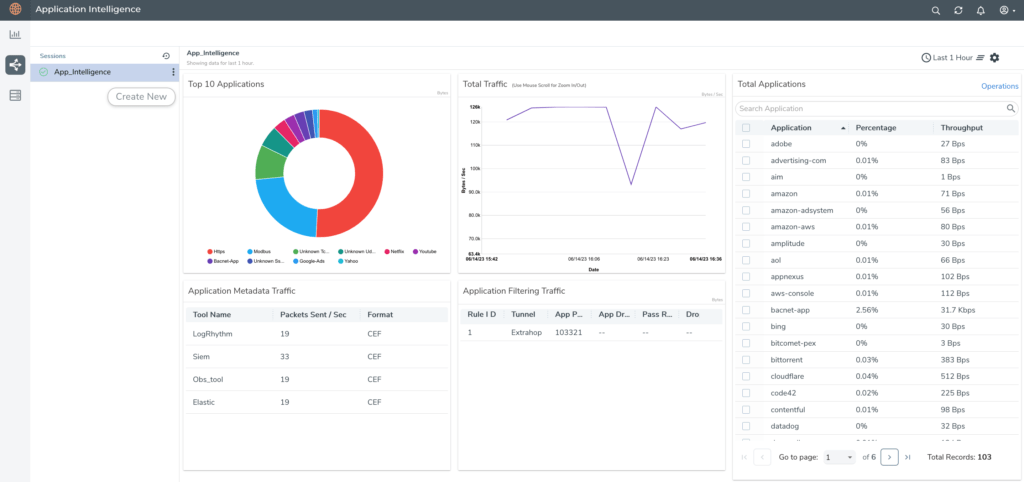
These rules (or filters, as we call them) can be very simple — for example, send all traffic from this app category through tools A and C but not B. Or they may be more complex, such as: inspect the header of this stream of traffic and, based on its content, do X. These rules can be driven not only by the packets in the traffic but also by metadata derived from the application. Network-level intelligence derived from this activity can be used to populate performance or security dashboards in SIEM or observability tools where it can enrich metrics, events, logs, and traces (MELT) data for an application.
Put Gigamon Application Intelligence to Work for You
Visualize applications, filter application traffic, and extract contextual metadata with Gigamon Application Intelligence, our most popular GigaSMART® solution. Augment your GigaVUE® traffic intelligence functions (like de-duplication, filtering, and Flow Mapping®) by enabling these to operate at the application as well the network level. To find out exactly how we achieve this and how Gigamon Application Intelligence closes the application visibility gap, please contact us to arrange a demonstration.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today








