ESG Testing Validates Gigamon Hawk Deep Observability Pipeline
As organizations pursue digital transformations, their infrastructure grows more complex — which causes countless headaches. According to research from the Enterprise Strategy Group (ESG), 79 percent of surveyed organizations believe their IT environments are as complex or more complex than they were two years ago, and 73 percent say the number of tools they use for observing network performance and application behavior add to that complexity.
The problem is particularly acute for those organizations that must coordinate on-premises and cloud infrastructure and multiple tools from multiple vendors that don’t share a common interface or workflow. This opens organizations up to risks of poor performance or cyberattacks.
The Gigamon Hawk Deep Observability Pipeline aims to tackle these problems by helping organizations proactively identify and remediate security and performance limitations in hybrid and multi-cloud environments. Instead of replacing existing monitoring tools, Gigamon Hawk enables the access and sharing of data collected across all applications and the underlying network.
To find out if Gigamon Hawk could deliver on that promise, ESG evaluated that platform via remote product demonstrations. The tests assessed how Gigamon Hawk helps organizations preserve investments in existing toolsets, establish comprehensive visibility into workloads deployed on-premises or in hybrid and multi-cloud environments, and bolster overall security.
Establishing Hybrid and Multi-Cloud Visibility
Organizations need to monitor both their internal (East-West) and incoming/outgoing (North-South) network traffic. But when their infrastructure sprawls across both on-premises datacenters and one or more private clouds, that’s a lot harder to achieve. The tools that cloud service providers offer are generally limited and inadequate. Twenty percent of respondents to an ESG survey cited the lack of visibility across public or hybrid cloud environments as one of their top three challenges when it comes to deploying observability technology solutions.
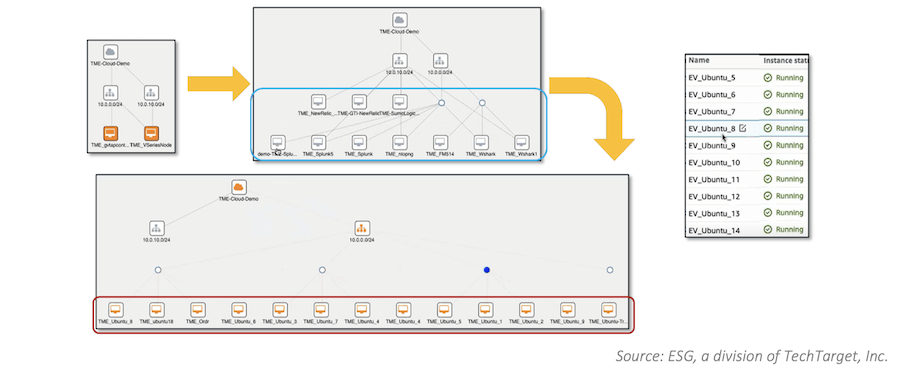
ESG’s validation analysts used Gigamon Hawks’ Inventory Map UI to examine three levels within an AWS-based monitoring domain: the AWS Virtual Private Clouds (VPCs) within the domain, the monitoring tools associated with the AWS VPCs (such as New Relic, Splunk, and Wireshark), and the AWS Elastic Computing Cloud (EC2) instances feeding traffic data into the tools, as shown in Figure 1.
ESG also viewed resources in other public cloud environments not part of the original monitoring domain and saw how Gigamon Hawk made it simple to maintain East-West visibility as workloads scaled up. Overall, they noted that with Gigamon Hawk, organizations no longer have to switch between provider- or vendor-specific tools to determine what is happening with their workloads; the solution lets you monitor both North-South and East-West traffic, no matter what cloud service provider you use.
Part 2. Bolstering Security Posture
Many organizations use separate tools for application and network monitoring. More often than not, these tools do not share data, leaving visibility gaps that prevent organizations from identifying potential security threats embedded in network traffic. In particular, traffic that passes through network monitoring tools is often SSL/TLS-encrypted by applications and thus opaque to security scans, leaving open the possibility that lurking malware is moving East-West across your infrastructure.
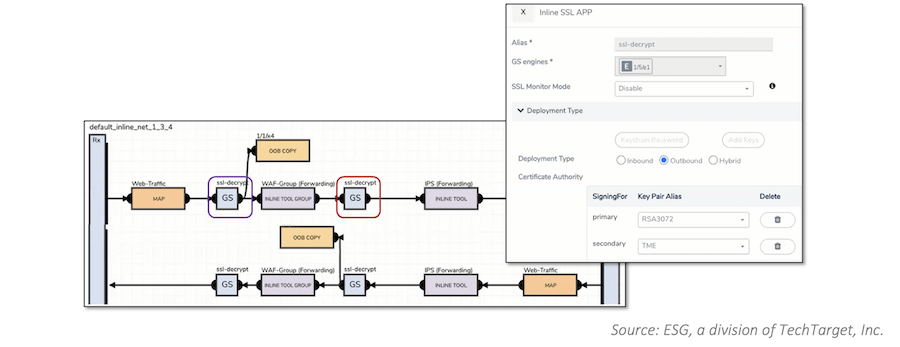
ESG’s validation analysts used Gigamon Hawk’s intuitive network GUI to specify traffic packets or flows that they wanted copied and decrypted once before being transmitted to their final destinations, on both on-premises and public cloud environments.
As you can see in Figure 2, ESG was able to perform both inline/man-in-the-middle decryption (by deploying Gigamon Hawk in the red box) and passive/out-of-band encryption (by deploying in the purple box), illustrating an example of inline/man-in-the middle decryption.
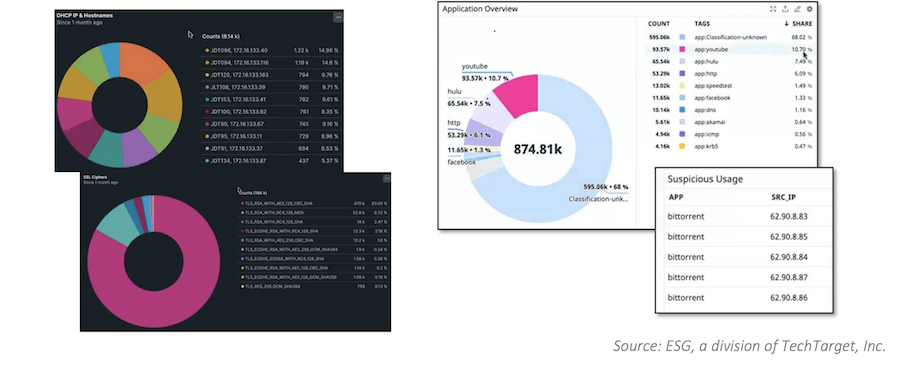
ESG also specified application data and metadata for Gigamon Hawk to filter and forward to security tools like New Relic and Datadog, which could then marry network data with application-derived metrics like logs, traces, and events to provide deep security insights, as shown in Figure 3.
Overall, ESG found that Gigamon Hawk boosted security with existing tools without degrading network performance by offloading traffic decryption and inspection functions, helping users more quickly identify and remediate threats. The ability to filter existing network traffic based on application metadata can also enhance your organization’s security posture, focusing attention on what is critical to monitor.
Preserving Investment in Existing Toolsets
Most organizations have accumulated a suite of network and application monitoring tools. To quickly determine how and why issues have arisen, you need to correlate data obtained from these tools, but ensuring that each tool can access copies of workload traffic from multiple tools typically adds to existing complexity in IT networks and management overhead.
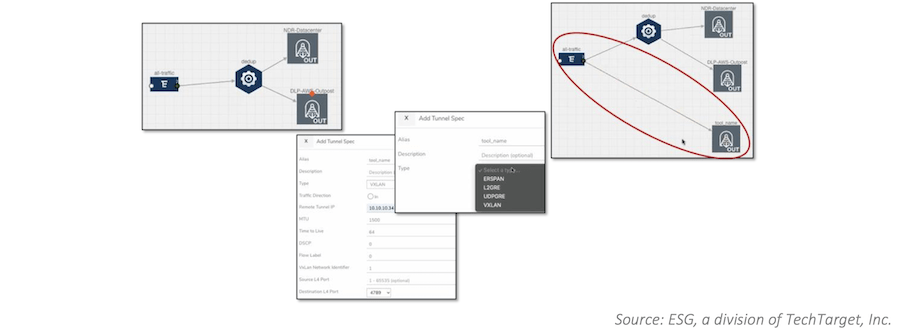
ESG’s validation analysts used Gigamon Hawk to direct traffic flows within AWS to multiple monitoring tools. As you can see in Figure 4, traffic from multiple AWS instances was aggregated and sent via the Gigamon fabric both to a network detection and response tool in an on-premises datacenter and to a data loss prevention tool in an AWS Outpost. Both copies were de-duplicated before they were sent to these tools. ESG was able to then send non-de-duplicated traffic to a third tool.
The alternative to this simple drag-and-drop process would be deploying multiple agents to generate copies of traffic. That would increase operational complexity and costs when managing agent sprawl. ESG concluded that Gigamon Hawk’s ability to direct traffic to existing monitoring toolsets eliminated the need to rip and replace those tools, while simplifying how organizations can improve overall observability.
Take a Deeper Dive
There are plenty of details in the full report to help you understand ESG’s validation methods and what they learned. If you want to find out how Gigamon Hawk can help you gain visibility into workloads deployed across diverse environments, bolster overall hybrid cloud security, and maximize investments in your existing toolsets, read the report today.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today