Getting to Know You – A Tour of the Updated ThreatINSIGHT Interface
In the seminal Rodgers and Hammerstein musical “The King and I,” Julie Andrews sings the song “Getting to Know You.” For those who don’t know, “The King and I” is a musical about a British schoolteacher — Andrews — hired as a governess, who begins a relationship with the King of Siam and his children. The line that stuck in my mind as I started writing this post was, “You are precisely my cup of tea.”
With the 2022.09 and 2022.10 releases, Gigamon introduces its updated dashboard and improved user interface (UI) for Gigamon ThreatINSIGHT™, and it promises to be precisely the cup of tea for security analysts, threat hunters, and incident responders by providing them with the dark mode version they’ve been craving, plus more analytics they need to combat today’s threats.
Throughout this post, I’ll walk you through these interface updates and how they’ll streamline the investigation process across your security team.
Dark Mode and the New Default Dashboard
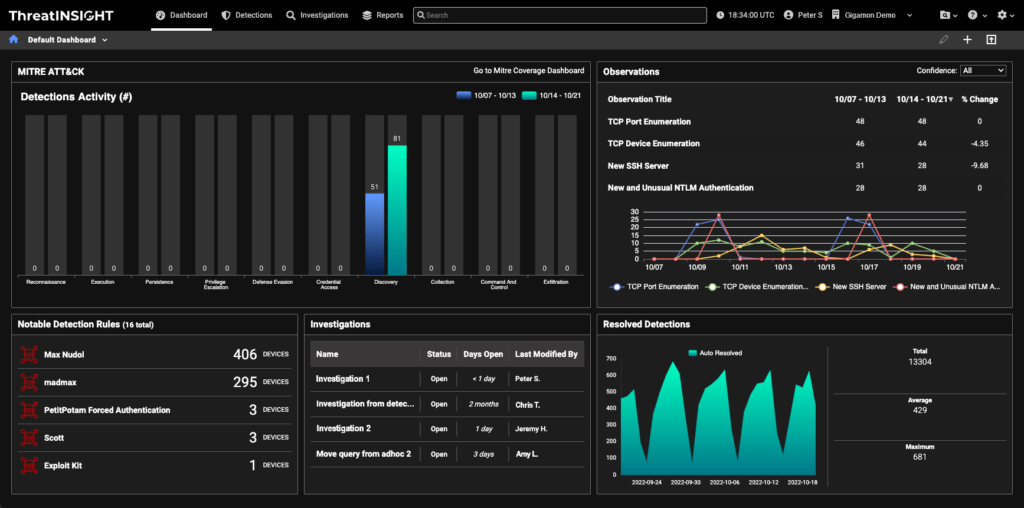
The default dashboard provides you with the information you need to get an idea of what is happening on your ThreatINSIGHT instance. Let’s walk through each of the new widgets in the dashboard:
- Dark mode — With 2022.10, Gigamon ThreatINSIGHT will now allow users to toggle between “light mode” and “dark mode” directly from the settings in the navigation bar.
- MITRE ATT&CK — With the MITRE ATT&CK widget, an analyst gets an overview of the number of detections aligned to the MITRE ATT&CK framework. These are presented in a bar chart and compare detections from the previous week to the current week. It’s a snapshot of what detections are happening on the network.
- Observations — The Observation widget gives you “hunting leads” that aren’t quite detections but indicate anomalous activity on the network. You can use these as the basis for an investigation or to provide data points for incident response efforts.
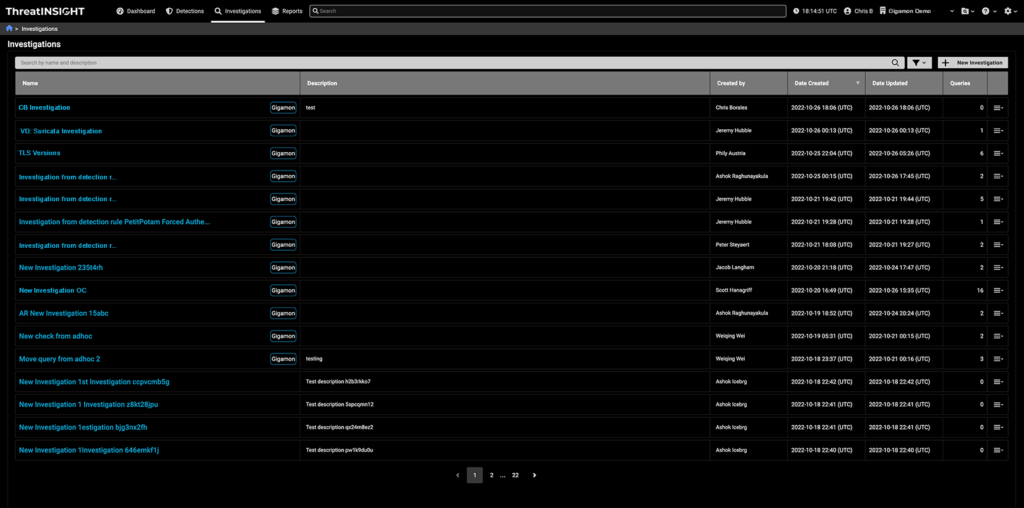
- Investigations — The Investigation widget gives you a snapshot of the five most recent open investigations on your ThreatINSIGHT instance. Each investigation can be worked on in parallel across your security team.
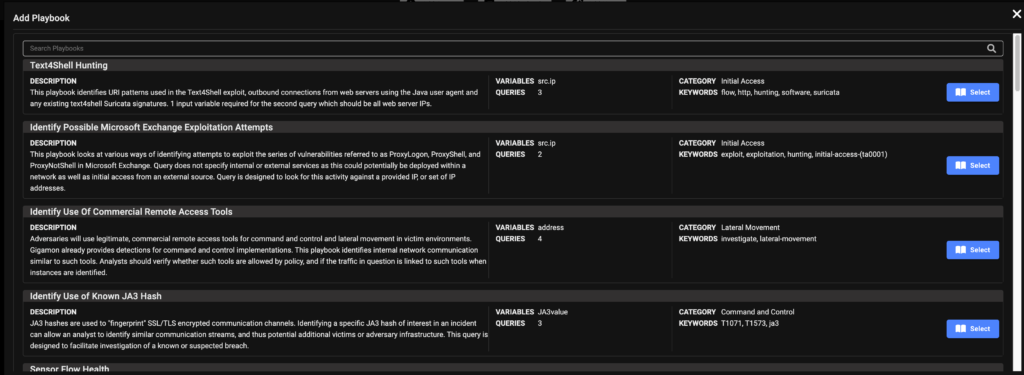
Guided Playbooks
The Gigamon Applied Threat Research (ATR) team continuously develops a set of playbooks of pre-built queries that you can use to build your investigations.
Parallel Hunting
I briefly mentioned this when I discussed the Investigations widget, but with parallel hunting, you ensure that your investigations can be worked on in parallel across your security team (regardless of location). Parallel hunting also allows you to streamline your investigations by searching for multiple events at the same time.
These interface improvements are the direct result of listening to our customers and asking them how we could improve ThreatINSIGHT to make their lives easier. That meant giving them relevant detections, observations, and telemetry to hunt for threats and conduct thorough investigations.
ThreatINSIGHT customers can view the 2022.10 release notes in the web portal.
Want to learn more about ThreatINSIGHT and see these improvements for yourself?
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s ThreatINSIGHT group.
Share your thoughts today