AWS re:Inforce — Takeaways on Cloud Security, Refactored NGFWs, and the Need for Deep Packet Inspection
Next-generation firewalls (NGFWs) aren’t new, but the recent refactoring of AWS Network Firewall and Palo Alto’s NGFW has some significant implications for cloud security that were apparent at this year’s AWS re:Inforce conference.
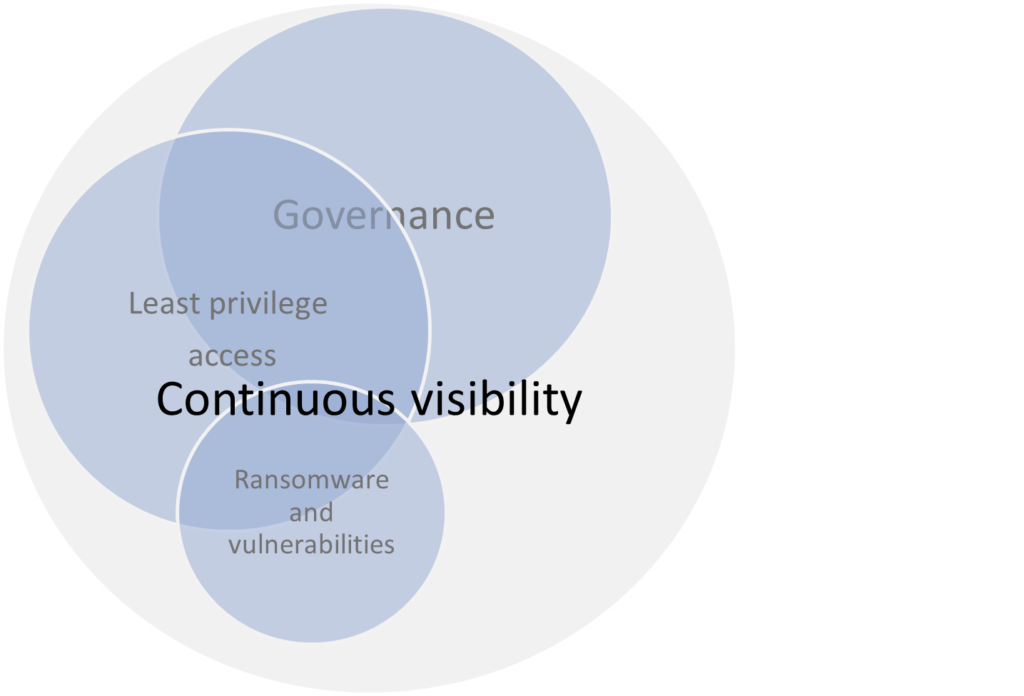
AWS re:Inforce highlighted several broad areas that cloud security can be broken into:
- Governance
- Least privilege access
- Vulnerability identification/remediation/protection
- Continuous verification
Let’s look at these overlapping security factors and how they relate to NGFWs.
Governance Guardrails
Many issues that were never a problem in-house or in a localized dev environment are now huge security risks in the cloud, so you’ll need to ensure the cloud, user accounts, and compute are configured correctly. For example, while working on projects locally, it’s common for credentials and access rules to be left as default. Doing this in the cloud invites disaster. The shared security model is clear about where security responsibilities lie, but this may not be apparent to devs who haven’t worked with a lot of infrastructure. Gartner highlights this in their recommendations for cloud security: “Through 2025, 99 percent of cloud security failures will be the customer’s fault.”*
Additional guard rails are needed. In this case, a cloud security posture management (CSPM) can help deploy, verify, and enforce guardrails that may be new or novel to groups that don’t traditionally have to worry about them. Continuous monitoring is also needed — not just at the programmatic level but at the network level. This can be seen in AWS Network Firewall and Palo Alto’s new refactored next-generation firewall (NGFW) using Gateway Load Balancer (GWLB).
Least Privilege and Continuous Monitoring
Least privilege is one of the key aspects of Zero Trust. Does newly spun up compute need network access to the whole enterprise or just the few nodes it needs to do its job? Do all dev accounts need full access? Network access lists should be modified to limit access. User/machine accounts should be audited and continuously verified to detect inappropriate access or privilege escalation. While it’s continuously monitoring, a CSPM can handle most of the account privileges and some of the network visibility via native tools. You will also need a specialized solution, such as AWS Network Firewall or another solution, to see beyond logs and detect and identify applications and protocols in flight. This is where a network visibility gap exists. Standard VPC flow logs only identify protocols on sec/dest ports, so there is a chance of misidentification.
Vulnerabilities: You Can’t Hide from Deep Packet Inspection
Ransomware and vulnerabilities are detected through a number of cloud-native and non-cloud-native tools. Workload protection clients come to mind here, but one absolute truth is that no ransomware can spread without putting traffic on the network. The network application visibility offered by AWS Network Firewall can help identify this; however, it is not enough. DNS and CnC requests on nonstandard ports could be invisible outside of deep packet inspection. VPC flow logs will only identify them based on standard ports. Here is where continuous network monitoring is immutable in its detection, and the addition of newly refactored NGFWs could be read as an acknowledgment of that. Endpoints can be altered or logs turned off, but attackers can’t evade deep packet inspection.
An Evolution in NGFWs
NGFWs have undergone a long-overdue refactoring. All routing has been removed from AWS Network Firewall and the refactored Palo Alto NGFW using GWLB. The cloud does all the routing now. Previous forklifted designs were an intermediate step to gaining this visibility but were very high friction to deploy and maintain. Refactored NGFWs have been distilled into inspection nodes that can perform intrusion prevention (IPS), deep packet inspection, and some application identification. This is a critical addition to AWS standard logging.
The downside of these solutions is the expense and the need for either a transit gateway or a GWLB to pass traffic for inspection. Other deep packet inspection tools that do not require such deployments also augment the continuous visibility needed for proper governance, security, and maintaining least privilege access.
In conclusion, there is significant feature overlap in most virtual firewalls and native cloud functionality. AWS network firewall and other firewalls are evolving into inspection points with most of the networking function removed. The cloud does most, if not all, of the networking firewalls that used to be done natively. NGFWs are evolving into inspection nodes/IPSs on a stick, to use old network terminology, which indicates that additional visibility is needed in the cloud in the form of deep packet inspection.
Citations
* Kasey Panetta. Is the Cloud Secure? October 10, 2019. Gartner. https://www.gartner.com/smarterwithgartner/is-the-cloud-secure.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Hybrid/Public Cloud group.
Share your thoughts today