Gigamon Guide: Advanced Techniques to Respond to Log4j Vulnerability
We released a blog on the importance of response to mitigate fallout from Log4J vulnerability. Per requests from customers, this blog provides guidance on leveraging the Gigamon Visibility and Analytics Fabric™’s capabilities for an additional layer of security.
The vulnerability allows the adversary to execute their code on servers running Log4j versions 2.14.1 and earlier. The exploit works with any protocol that triggers a log by a system using certain versions of the log4j java class object. Gigamon can help uncover exposure to this vulnerability via several methods.
#1. Monitoring East-West Traffic
The pervasiveness of this attack surface is a good example of why it’s so important to monitor East-West traffic in physical, virtual, and cloud environments. Security tools connected to a Gigamon Visibility and Analytics Fabric will learn to detect and mitigate known and emerging methods using this exploit.
As a force multiplier for security solutions, Gigamon recommends extending visibility beyond the perimeter into the internal networks, VMware networks, and other private and public cloud networks. As new techniques develop, our more than 5,000 unique metadata elements will be useful for ad hoc threat hunting. Other protocols likely to be exploited could include DNS and SQL, for example. Different techniques will certainly be developed using different protocols.
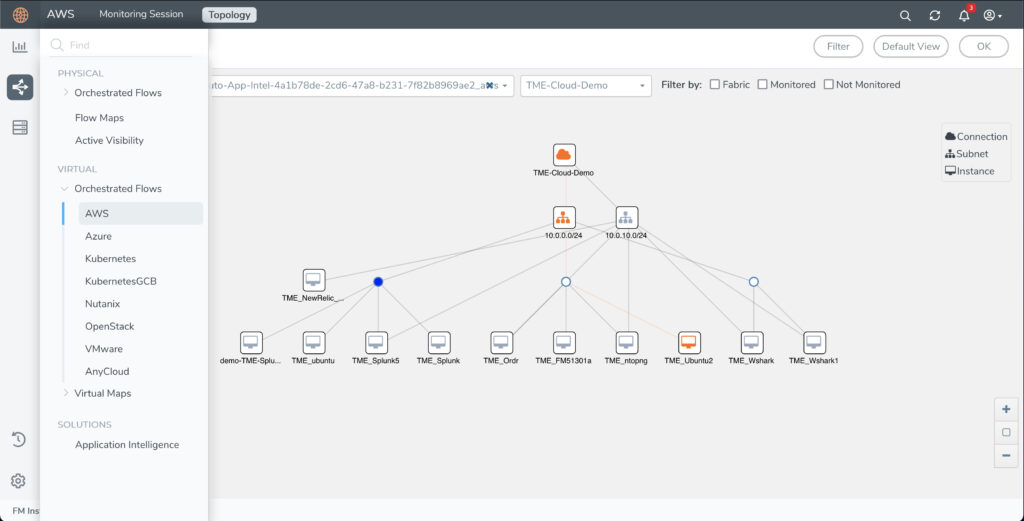
Here is an example how customers can use Gigamon GigaVUE-FM fabric manager as one single platform to see and manage all traffic.
#2. Monitoring Outbound Calls Over LDAP Protocol
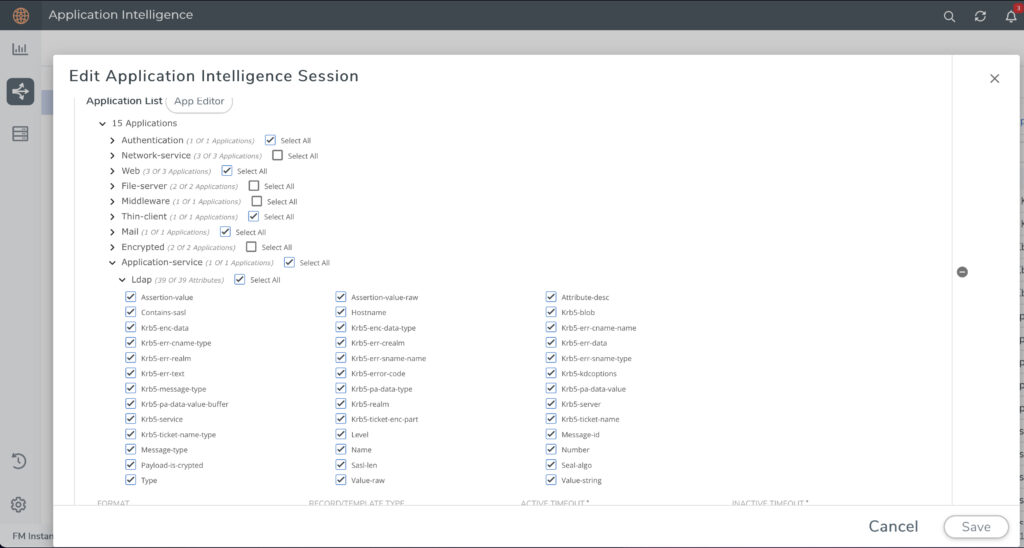
You can configure Gigamon Application Meta Data Intelligence to send a log event of any machine accessing an LDAP resource. This generated list is useful for remediation efforts. Any calls to an LDAP resource outside of an organization would be immediately suspect.
As this exploit vector matures, LDAP (and other) communications that happen internally need to be constantly inspected. Detection systems on the perimeter will learn quickly and will catch this behavior.
As attackers become stealthy and focus on nurturing APT botnets inside of networks, they will attempt to set up unauthorized LDAP and other resources to propagate malware within organization boundaries. This compromise vector will persist for a long time as part of malware toolkits.
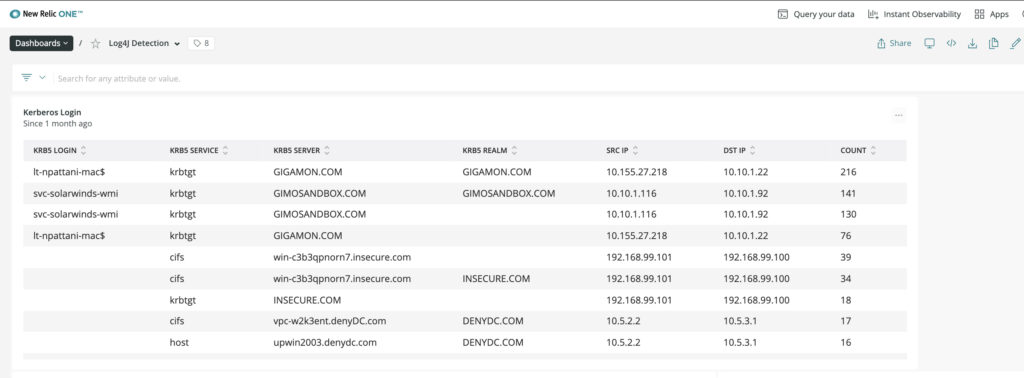
Here is another screenshot, using New Relic One, that illustrates how customers can track LDAP logins with reference to domain and source/destination IPs. The compromised hosts would normally be accessed from external IPs. Customers often combine monitoring and dashboards and alerts with both New Relic approach and Gigamon metadata.
#3. Application Filtering
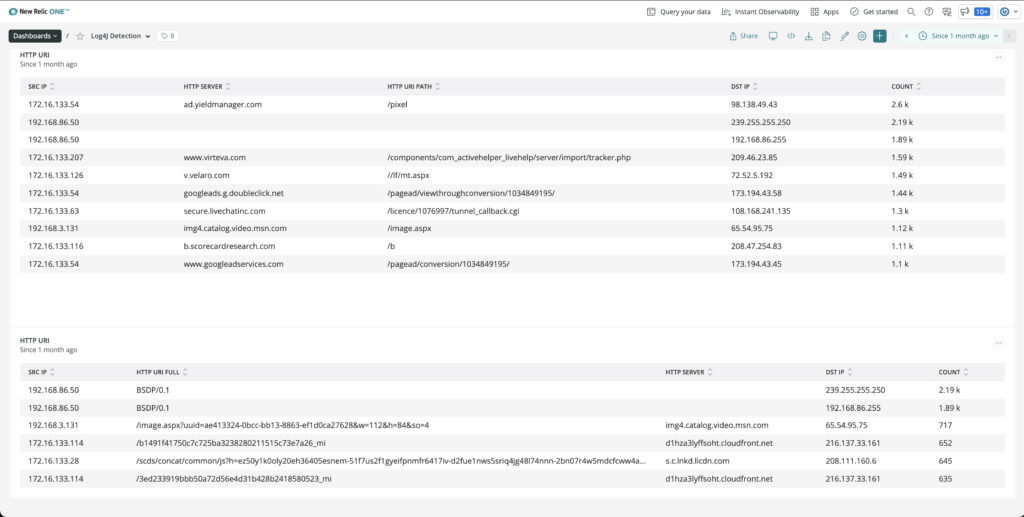
Any protocol that causes a log event can be used to trigger this exploit. In the wild right now, the user agent string and post command from web transactions are being used to push the malicious string to log4j. Gigamon Application Filtering Intelligence can catch these web fields to send to a log storage system. A search for the malevolent string will expose devices launching attacks. Here is a defanged example:
${jndi:[protocol]://[remote server and code address]}The protocol would be the abbreviation for Lightweight Directory Access Protocol. It goes without saying that your primary logging repository must be patched.
#4. Detecting Cryptojacking
This vulnerability opens a wide door for the threat actor to install and execute any type of application. Recently, cryptocurrency mining servers have rocketed to the top of the list of applications because that is the shortest route from breach to monetization. A recent Google Cybersecurity Action Team research report shows that 86 percent of compromised Google Cloud instances were used for cryptocurrency mining, most happening within 30 seconds of the compromise!
Crypto-mining traffic is difficult to detect because many mining applications are designed to be stealthy and avoid security detection mechanisms; there is no C2 communications, they can turn up/down their resource consumption with the VM’s natural ebb and flow, they don’t generate log files, or generate traffic of significant volume.
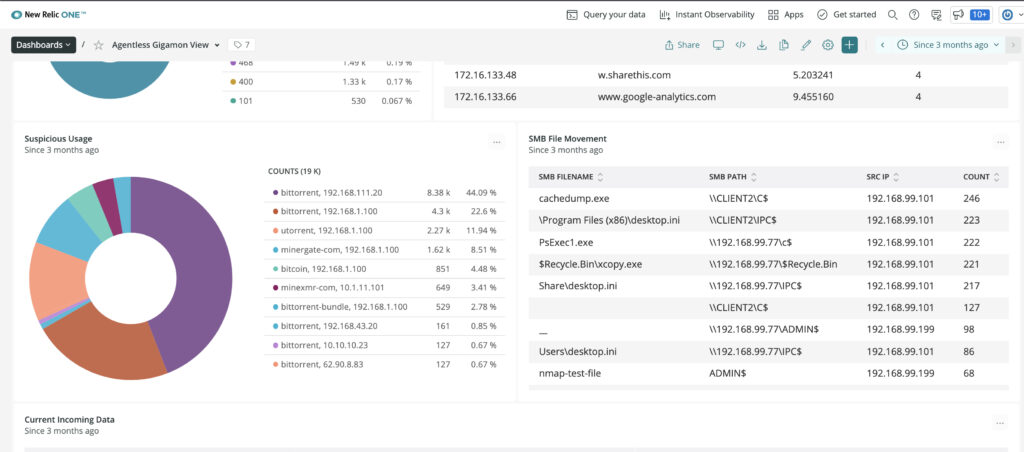
Through deep packet inspection, Gigamon Application Metadata Intelligence helps you identify over a dozen types of crypto traffic, including Bitcoin, Monero, Ripple, and Ethereum.
You can use Gigamon application metadata with your observability or SIEM tool of choice. This dashboard below shows Gigamon detecting crypto traffic and displayed in New Relic One dashboard.
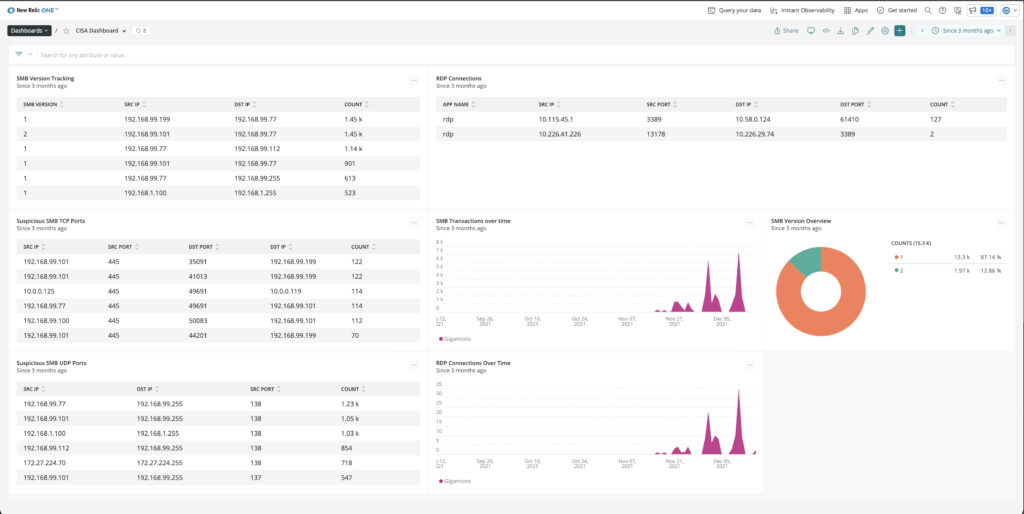
#5. Following CISA Ransomware Guidance
The U.S. Cybersecurity and Infrastructure Security Agency published a best practices guideline with prescriptive steps for ransomware security.
Gigamon customers can use these guidelines for detecting SMB v1 or V2, suspicious RDP connections, monitor SMB TCP and UDP ports, and look for suspicious SMB and RDP traffic for data exfiltration.
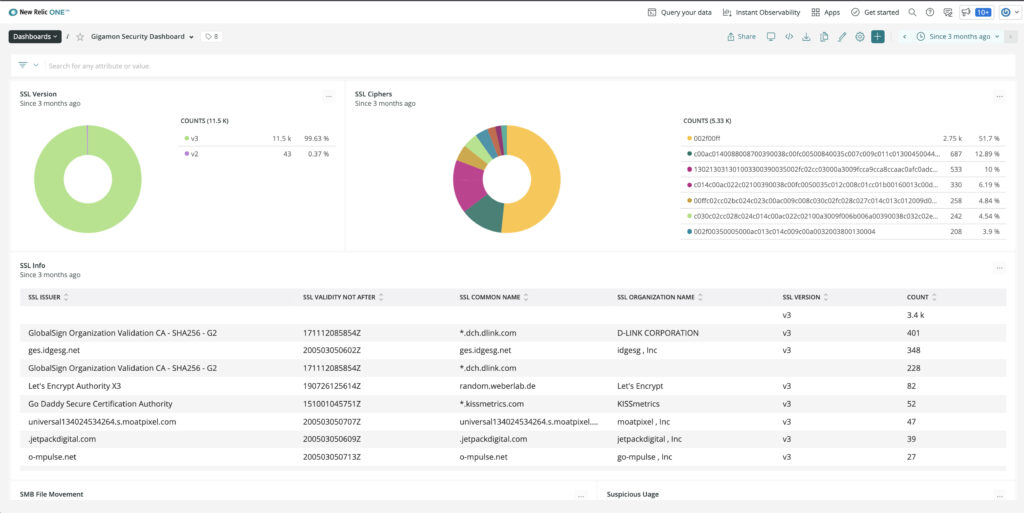
#6. Monitoring TLS Hygiene per the NSA
Lastly, while not directly impacted by the Log4j incident, Gigamon recommends customers constantly monitor the state of their SSL/TLS composition and usage. Using Gigamon Application Metadata Intelligence to keep track of SSL certificates helps discover and identify certs that are expired or are about to expire, self-signed certs that could be compromised, weak ciphers, and use of old SSL version that introduce unacceptable risks.
Here is another New Relic dashboard that tracks this TLS configurations, per the National Security Agency’s advisory from earlier this year.
How to Get Additional Help
If you’d like help with these techniques or additional ideas, sign in to and start a discussion at the Gigamon Community’s Security Group.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.








 Matt Hollingsworth
Matt Hollingsworth