5G Security Insights You Should Know
New technology always brings a host of worries about its negative potential, and 5G is no different. Although there are many legitimate 5G security concerns to address and discuss, it’s worth first clarifying the false claim that 5G causes health problems. It doesn’t — 5G technology is not harmful to humans.1 With that out of the way, we’ll discuss what 5G is, what security risks it faces, and how experts are working to ensure 5G network security.
What Is 5G?
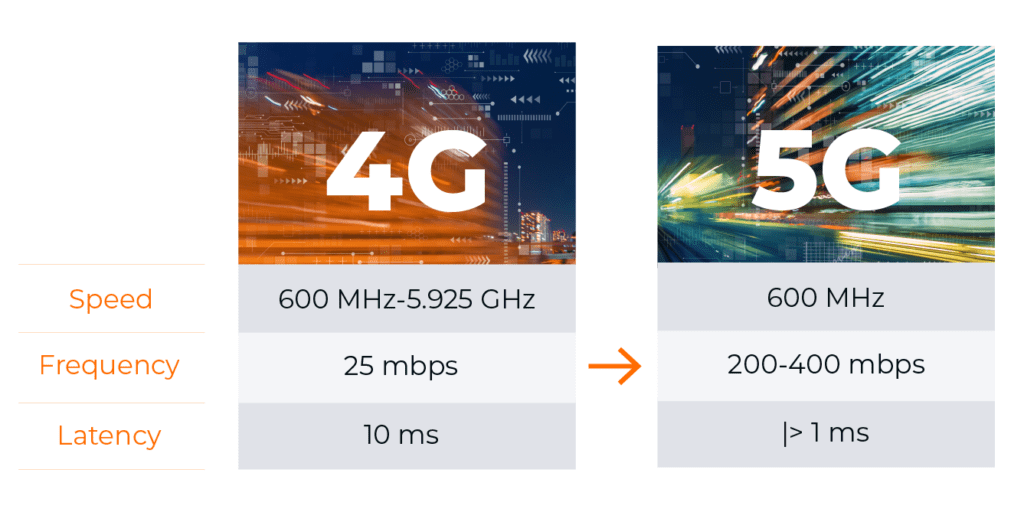
5G stands for the fifth generation of cellular mobile networks. In terms of architecture and protocols, the 5G radio access network (RAN) and 5G core are quite different from 4G LTE. The 5G RAN uses new radio frequency (RF) protocols, offers a broader and higher frequency band spectrum, and has an open-distributed architecture. The 5G core differences include SDN with control and user-plane separation (CUPS); disaggregation offering many more discrete control and orchestration functions, virtualization, and microservices (that is, containers); HTTP/2 (not GTP-C) control plane; TLS 1.3 encrypted control plane; and multi-access edge compute (MEC).
These all represent significant changes, and while in some cases they look to help with security, in other cases they open up the potential for more vulnerabilities and even a lack of visibility. The new 5G core is required to help fulfill the expectations that 5G promises; the high-band spectrum alone is not sufficient to fulfill this.
5G is expected to be roughly 100 times faster2 than the current 4G network, in part because the networks are built on a high-band spectrum, rather than mid-band. This speed boost will bring upgrades to everything from cloud robotics to healthcare.3
One major downside of this lower latency network, however, is the range and penetration. The lower power and higher frequency signals don’t travel as far and have a harder time getting through walls,2 which is why it might take a little longer for 5G to become a standard feature of most mobile device services.
There is a major advantage to this high-band adoption lag, though: Experts have more time to find solutions to 5G security concerns.
5G Security Threats
Many of the things that make 5G so appealing, like the decreased latency and increased bandwidth, are also threats to security. When it comes to 5G security, threats include:
- New technology – New advances in technology often mean new problems. And given that 5G is not only new but also very different from 4G, this means that while experts can predict some security weaknesses, others may not become apparent until the breach has already occurred.
- Increased points of access – 5G allows for more access points. Every additional hardware point of contact creates another potential opening for attackers to get into the network. That means all access points will need to be monitored on a physical and digital level.
- Internet of Things (IoT) – The speed of 5G lends itself well to use with IoT devices. That said, an increase in connected machines can also mean an increase in security 5G risks. Smaller IoT devices, like thermostats, often have weaker security — and a breach in one of these devices can mean the entire system is compromised.
- Speed – 5G is fast enough that it is being considered for use in remote surgery and self-driving cars, but that also means it could be harder to track and prevent attacks. At the same time, this critical and sensitive data transmission will require even higher levels of security to prevent breakage in communication, malicious behavior, or snooping/stealing information.
- Disaggregated architecture – As previously mentioned, 5G’s disaggregated architecture means that network functions are able to operate freely from the underlying system hardware, allowing for improved control and visualization. However, the downside is that, rather than relying on a single, overarching security approach, each of these components will need to have its own security measures “baked in.”
Of course, these are just some of the risks to 5G security — keeping services and connected devices secure is rarely, if ever, a 100 percent guarantee.
Solutions for 5G Security
Although the 5G network poses new and unique threats, there are already ways to help ensure a secure 5G environment:
- Increased defense for individual mobile and IoT devices
- Zero Trust combined with a foundation of software security
- End-to-end visibility
- Threat analytics
For optimal 5G security, networks should be treated as a Zero-Trust environment, where it cannot be taken for granted that connected devices will have sufficient security or vulnerability protection. Therefore, the first step should be ensuring adequate visibility across the network with appropriate security monitoring, threat detection, and mitigation processes in place even before devices are connected to the 5G network.
Secure 5G networks will be a group effort, involving network providers, cybersecurity experts, and customers themselves. As a second line of defense in conjunction with Zero Trust, a foundation of software security for mobile and IoT devices will need to be developed in tandem with network providers and cybersecurity firms. Even innocuous IoT devices, like smart fridges, should be equipped with high-level security. Furthermore, precautions should be in place to ensure a breach in lesser IoT machines won’t lead to unauthorized access to sensitive information.
Next, end-to-end visibility is vital for monitoring any system, but it’s especially necessary for 5G security, where there are so many points of access for malicious actors to target. This monitoring should extend across all layers of the network, including the physical network cells and data planes. Effective monitoring will also provide vital information for understanding new attacks. Combined with mitigation procedures, this will provide a more effective defense against potential incursions and a secure 5G environment.
Threat analytics is a useful way to track and even predict attacks. Ideally, these analytics systems would be able to enact preventative measures to stop a breach from occurring. These programs offer vital information in the ongoing process of defending devices on a 5G network.
Secure 5G with Gigamon
For more information on how Gigamon can help provide 5G defenses, check out these additional readings:
- Service Providers Under Attack
- Enabling the 5G Experience
- 5G Traffic Intelligence
- 5G and CUPS Correlation
- Secure VoIP and Cloud with RedShift and Gigamon
References
- Khang T. Vuong. “Is 5G Dangerous or Harmful to Our Health? – A Summary of Previous Research.” Mira, Dec. 30, 2020. https://www.talktomira.com/post/is-5g-dangerous-or-harmful-to-our-health-a-summary-of-previous-research.
- Clare Duffy. “The big differences between 4G and 5G.” CNN, Jan. 17, 2020. https://www.cnn.com/2020/01/17/tech/5g-technical-explainer.
- “What Can You Do with 5G? Everything.” Nokia (sponsored content). Inc., Oct. 30, 2019. https://www.inc.com/nokia/what-can-you-do-with-five-g-everything.html.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today








 Dan Daniels
Dan Daniels