What a Seamless NDR + EDR Integration Looks Like: Gigamon ThreatINSIGHT and CrowdStrike Falcon
Over the last decade, the acceptance and adoption of “detection and response” has finally been reached. It required the market to ultimately have empathy for the struggles SOC and incident response teams face when trying to identify and stop the activities of adversaries after they got beyond frontline security tools. But now security vendors are applying their “what’s hot” marketing playbook to detection and response. We now have EDR, NDR, XDR, and MDR acronyms and promises flying around unabashedly. What’s worse are the check-box integrations vendors have put into the market to be able to back their “we integrate too” promises.
Without flashy words and empty promises, we are proud to introduce a full-featured NDR/EDR integration that is designed specifically for SOC and incident response teams while delivering the benefits security leaders seek — an efficient, effective security team.
Gigamon ThreatINSIGHT™ NDR has partnered with CrowdStrike Falcon to deliver a detection and response solution unlike any currently available. ThreatINSIGHT Guided-SaaS NDR integrates with the Falcon platform to deliver the most comprehensive network-to-endpoint visibility with combined threat intelligence, advanced behavioral threat detection, host containment, and the strongest tools and telemetry to allow security teams to do their job: stopping attackers in their tracks.
Focused on enabling and empowering joint customers to detect and respond with certainty, ThreatINSIGHT, Falcon Insight EDR, and Falcon X threat intelligence products combine to provide a fully unified NDR and EDR integration. Together, they help you close the SOC visibility gap and dismantle adversaries.
Scenarios | Technical Capabilities | Why SOC/IR Teams Should Care | Why Security Leaders Should Care |
Avoid multi-vendor headaches | Out-of-the-box, cloud-to-cloud integration with both Falcon X threat intelligence and Falcon Insight EDR | Fewer distractions with zero integration work or ongoing maintenance | Fast time to value, plus security teams can focus on threats, not solutions management |
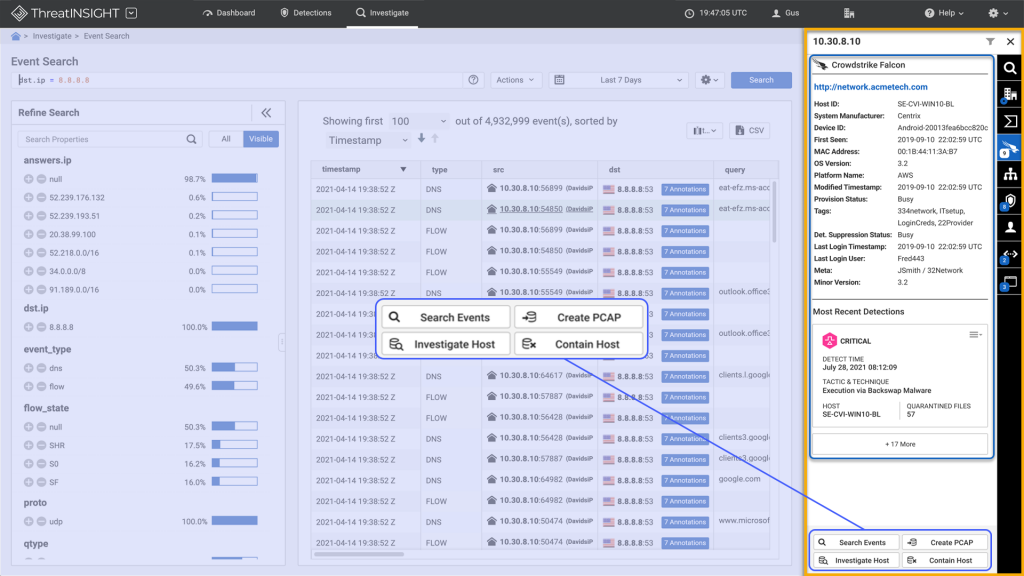
Close SOC visibility gaps | In-depth host telemetry for managed devices and L2-L7 network metadata for all devices within ThreatINSIGHT Note: Most NDRs can only provide L2-L4 visibility for all devices | Observe all devices (x-axis breadth) with rich host and network context (y-axis depth) within a single console to perform triage, hunting, and investigations across current and historical activity (z-axis time) | In-depth context for SOC teams on a single platform for efficiency and effectiveness |
Achieve IoT, BYOD, and unmanaged device visibility | Employ ThreatINSIGHT to observe the behavior of all managed and unmanaged devices and identify whether the Falcon agent is present | Secure all devices and make informed response decisions even when Falcon agent is not present | Visibility into EDR gaps for better response decisions on all hosts, not just managed ones |
Faster threat intelligence detections | Utilize both ThreatINSIGHT proprietary threat intelligence and Falcon X threat intelligence on live network traffic | Faster Falcon X threat intelligence detections via real-time matches for all network devices, compared to trying to match against historical data in your SIEM | Get more out of your Falcon X investment by applying matches on live traffic, not just SIEM history |
Behavioral detection corroboration | Observe, triage, and investigate both ThreatINSIGHT and Falcon Insight behavioral-based detections with correlated telemetry | High-fidelity adversary behavior identification using CrowdStrike and Gigamon machine learning and behavioral analysis techniques | Improve mean time to detect by combining network and endpoint adversary behavior identification techniques |
Hunting and incident investigations | Query Falcon host-based telemetry alongside enriched network metadata with ThreatINSIGHT advanced investigation capabilities | Rich L2-L7 network and robust endpoint telemetry at your fingertips | Data and tools for hunting teams on a single platform for efficiency and effectiveness |
Host management | For any host being explored within ThreatINSIGHT, single-click to pivot directly into CrowdStrike to manage that device | Quickly investigate ThreatINSIGHT detections within Falcon Insight | Reduce complexity and drive faster mean time to respond |
Host isolation | For any host being explored within ThreatINSIGHT, easily isolate the device with a single click | Mitigate risk quickly once a device has been triaged and confirmed infected from within ThreatINSIGHT | Take swift action, improving mean time to contain |
Joint Gigamon ThreatINSIGHT and CrowdStrike Falcon customers can benefit from the integration immediately and should reach out to their Technical Success Management team with any questions.
If you are a CrowdStrike customer looking to close the SOC visibility gap by adding a network detection and response solution built by responders for responders, request a demo today.
How to Get More Information
To learn more, read the CrowdStrike + Gigamon ThreatINSIGHT solution brief.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Network Detection and Response (NDR) group.
Share your thoughts today








 Fayyaz Rajpari
Fayyaz Rajpari