Bringing Truth to Cloud
How Gigamon Hawk Network Context Helps Cloud Observability
Growing innovative solutions provided by every cloud vendor have enabled applications to span different public clouds, utilizing the best of every cloud service to provide the best experience for end users. A simple web application running on the internet may have the front end hosted on AWS, data stored on Azure, and machine-learning algorithms running on Google Cloud.
This inherently creates a wider surface, with each facet operating within a different set of rules and requiring a different set of monitoring and analyzing capabilities. The amount of data flowing cannot be stored in runtime and used for quick analysis and decision-making to figure out if traffic flow is a potential security threat. This has largely been solved by looking at “data about data,” or metadata. But most of the solutions available still require capturing data at the endpoint itself, then creating metadata and sending it to a place where it can be analyzed for threats. This can give an incomplete picture if the network context is not available or if the endpoint is not capable of creating and providing metadata, as with IoT devices. In such scenarios, network context can play a vital role, and as it’s been said, the data on the network is the single source of truth, since it cannot be modified or changed: It is what it is on the network.1
Imagine a scenario in which each car on the road reports back its location and where it’s headed. That’s useful information to optimize traffic, find anomalies, and so forth. In that situation, network metadata from Gigamon Hawk can be viewed as a new dimension of visibility within the system. It will be like having a camera at every intersection that verifies where each car actually is and what direction it’s going, even for cars that don’t have the capability to report their own status.
Gigamon Hawk provides a single place to capture and see all traffic, whether it is in a public cloud, a private cloud, or an on-premises network. This network context, captured from all sources and providing metadata about the network, can become a powerful source of truth about the data.
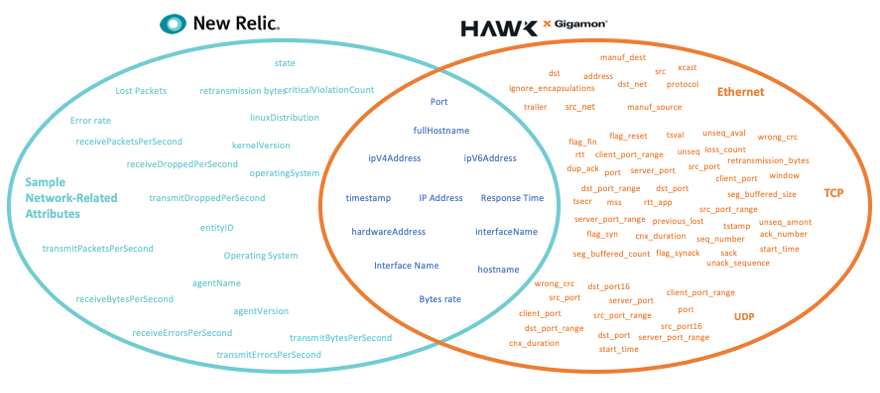
New Relic is one of the leading providers of observability platforms, enabling customers to gain rich insights into their applications and endpoints. Gigamon Hawk can empower this observability platform further by providing detailed metadata about the network context. The diagram below highlights how Gigamon Hawk can fill in some pieces and provide the missing part of the picture.
Rich network context provided by Gigamon Hawk can provide metadata from all sources at the same level and make any solution more powerful. The metadata elements shown on the left side of the diagram are provided by the network sample data source of the New Relic Agent, and the elements on the right are provided by Gigamon Hawk. There are certain attributes that overlap and can help build a stronger understanding of the network context, but in situations where these attributes are not available — like IoT devices — Gigamon Hawk can not only provide similar attributes but also a huge list of other attributes that can help build better insight. The best part is that these attributes can be collected from multiple environments, such as a public or private cloud and an on-premises device, and sent to any location for analysis.
This provides very powerful insights that can help create dashboards on New Relic or any observability platform that can show data collected from several locations at same level, and if you have the data from the endpoint and actual network, you could quickly and easily spot a threat or unusual traffic pattern.
Imagine a single dashboard displaying a full overview of what is going on in your network, on top of individual detailed dashboards that can quickly isolate the problem and identify where to look for it. Two of the dashboards that Gigamon Hawk has enabled by working with New Relic’s API and JSON ingestion are shown below.
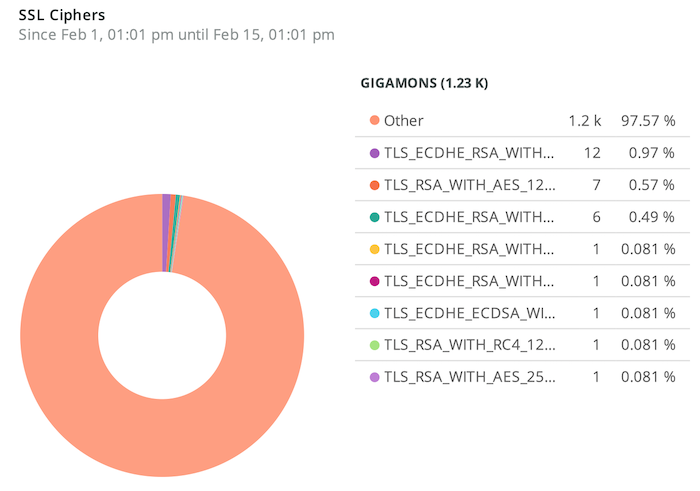
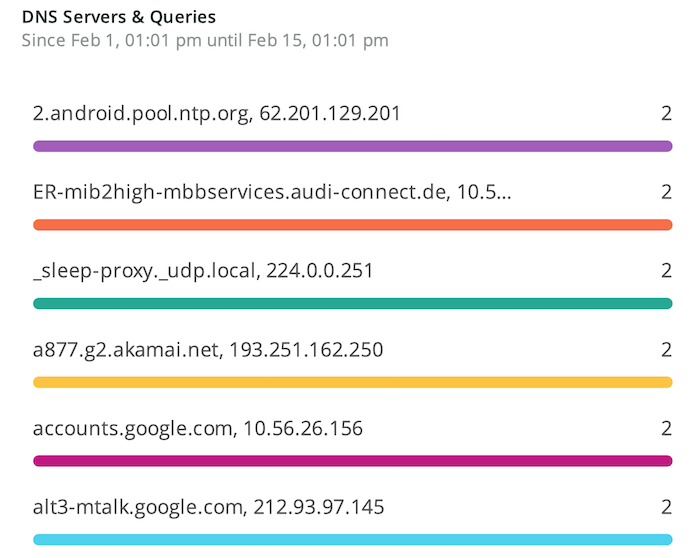
This valuable data in a single place can reduce problem solving significantly. These dashboards are just few examples. If you understand how the traffic flows within your web application from front end to data store or machine-learning workload, you can easily define a context that can instantly highlight any behavior that seems irrelevant. As stated in “Securing Internet of Things Devices Using the Network Context,”2 the network context would become the only source of truth for securing a network in which agent-based solutions cannot be deployed, such as IoT networks.
Gigamon Hawk can seamlessly merge into existing environments and provide complete network context and empower existing solutions to do more with less effort.
Citations
- Andrew Lerner. “Network Source of Truth (SoT).” Gartner, January 28, 2020. https://blogs.gartner.com/andrew-lerner/2020/01/28/network-source-truth-sot.
- M. Trnka, J. Svacina, T. Cerny, E. Song, J. Hong and M. Bures, “Securing Internet of Things Devices Using the Network Context.” IEEE Transactions on Industrial Informatics, Vol. 16, No. 6, pp. 4017–4027, June 2020. doi: 10.1109/TII.2019.2954100. https://ieeexplore.ieee.org/document/8903557.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Hybrid/Public Cloud group.
Share your thoughts today