Sounding the Alarm on DoH: Privacy Push Produces Blind Spots
There’s a major change coming to web browsers everywhere, and it’s going to fundamentally change how network monitoring works. DNS over HTTPS, or DoH, encrypts DNS traffic to make it invisible to third-party observers on the network. It’s already available in just about every major browser — and is or soon will be turned on by default in many browsers, including the dominant Google Chrome and Firefox.
But There’s a Price to Pay in Security
While the move is a victory for privacy advocates, it comes at a cost for enterprise network security managers, for whom DNS traffic is a valuable signal and mechanism for detecting malware and performing security data science. Enterprises need to start taking a good look at their network monitoring plan to figure out how to maintain their current levels of network visibility, and think about where decryption fits into their roadmap.
Why DoH and Why Now?
The push for DoH is part of the “encrypt everything” movement that aims to ensure privacy for users. In particular, DoH aims to prevent snooping by nation-states and ISPs; the latter are particularly upset about the move, which most privacy advocates probably see as proof the technology is doing its job. The way ISPs track user DNS information to mine data and even inject ads into their browsers was one of the major incentives for DoH.
DoH is controversial for a number of reasons, however. Paul Vixie, one of the original developers of DNS, is strongly opposed, saying that “DNS is part of the control plane, and network operators must be able to monitor and filter it.” (Vixie backs a rival technology, DNS over TLS.)
DoH can provide a false sense of security, especially when it comes to government surveillance: DoS hides DNS requests, but not IP addresses, and nation-states could still monitor dissidents by examining the IP addresses they visit and comparing them to a database of known dissident sites.
Is It Privacy, or a Ploy for a Walled Garden?
When a browser is using DoH, it will attempt to find DoH-compatible DNS servers in order to resolves internet addresses. If the user’s ISP provides such servers, then they’d simply rely on their ISP for DNS as they normally would; however, since many ISPs don’t support DoH, the browser will seek out other servers that will. Chrome, predictably, will connect to Google’s servers. This gives rise to worries about “walled gardens,” in which Google browser users have their network traffic directed to Google’s DNS servers (where, despite the encryption, traffic could still be analyzed for the benefit of Google advertising business).
Nevertheless, with both Google Chrome and Mozilla starting to shift to DoH by default, enterprises will be left to grapple with the fallout from a move that was mostly built to protect the privacy of individual consumers.
Trouble in the Enterprise
From the perspective of the end user, privacy and security may seem like two sides of the same coin. But network admins know that the two can be in conflict: Fully private communications are in practice very difficult to secure. If you’re at home, it feels very safe to know that nobody can snoop on what web sites you’re visiting; but at work, the team that protects the IT infrastructure you use needs to see where people are going online in order to detect and respond to threats.
Two Ways Threat Detection Will Suffer
There are a couple of major threat-detection techniques that rely on the network visibility you can only get with unencrypted DNS:
- Network admins can blacklist known bad websites and prevent users from visiting them
- Network admins can detect malicious actors attempting to abuse DNS itself — by communicating with a backdoor installed on a hacked system, for instance
But both techniques are unavailable for DNS traffic that you can’t decrypt. As user browsers shift over to DoH, you’ll find yourself increasingly unable to keep track of traffic on your own network. End users’ browsing will be private, but your infrastructure will be more open to attack.
For example, ZD Net reports that “An Iranian hacking group known as Oilrig has become the first publicly known threat actor to incorporate the DNS-over-HTTPS (DoH) protocol in its attacks.”
And that “Oilrig is most likely using DoH as an exfiltration channel to avoid having its activities detected or monitored while moving stolen data. This is because the DoH protocol is currently an ideal exfiltration channel for two primary reasons. First, it’s a new protocol that not all security products are capable of monitoring. Second, it’s encrypted by default, while DNS is cleartext.”
It’s true that browsers that support DoH don’t mandate it, and in theory you could just turn it off in order to keep your network’s DNS traffic unencrypted. But in practice, this is a difficult management problem: Chrome, by far the most popular browser, is shifting to implementing DoH by default, and very few shops use the browser’s enterprise management features.
In a large enterprise, the task of manually toggling this setting on hundreds or thousands of end-user computers can be a challenge, with the very real possibility of some systems being missed. In addition to the computers within the infrastructure, there are other devices to account for, such as mobile, tablet and IoT devices; it is not always practical or possible to change the configuration on such endpoints.
Get Visibility Even into Encrypted DNS
In order to maintain your visibility into DNS traffic, you need a decryption solution that works on DoH. You may or may not be using decryption today, but the increasing prevalence of DoH traffic will mean that without this capability, you’ll be in the dark.
Gigamon GigaSMART® SSL/TLS Decryption, which is part of the Gigamon Visibility and Analytics Fabric™, can fill this role. Much of the discussion about encryption’s effects on privacy versus security that we’ve covered here may give you a sense of deja vu, as similar debates arose with the advent of version 1.3 of the TLS protocol. Gigamon SSL/TLS Decryption has helped admins navigate that problem; and whether or not you’re using it for that purpose, it can help with DoH too.
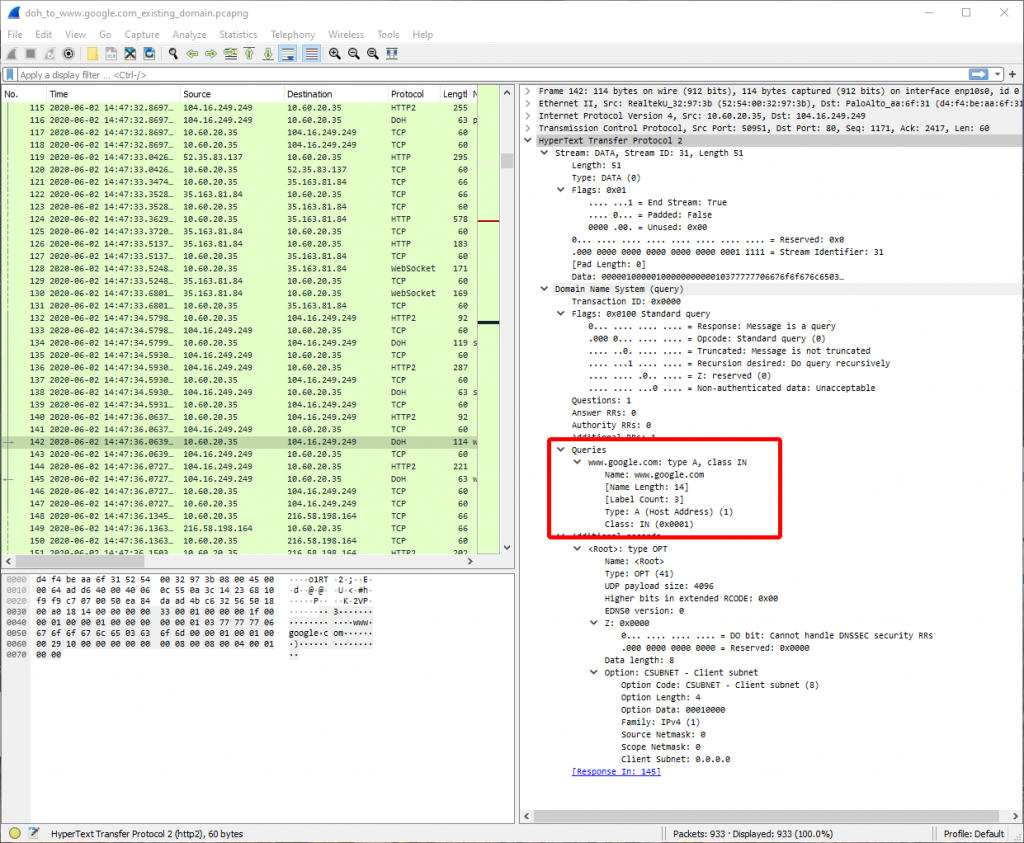
Figures 1 and 2 are screenshots from Wireshark that demonstrate the visibility Gigamon provides into encrypted DNS traffic. In Figure 1, we can see that packet 142 contains the DNS request (“what is the IP address for www.google.com?”). Note “DoH” in the Protocol column; this is the information that the Gigamon Visibility and Analytics Fabric has decrypted for us.
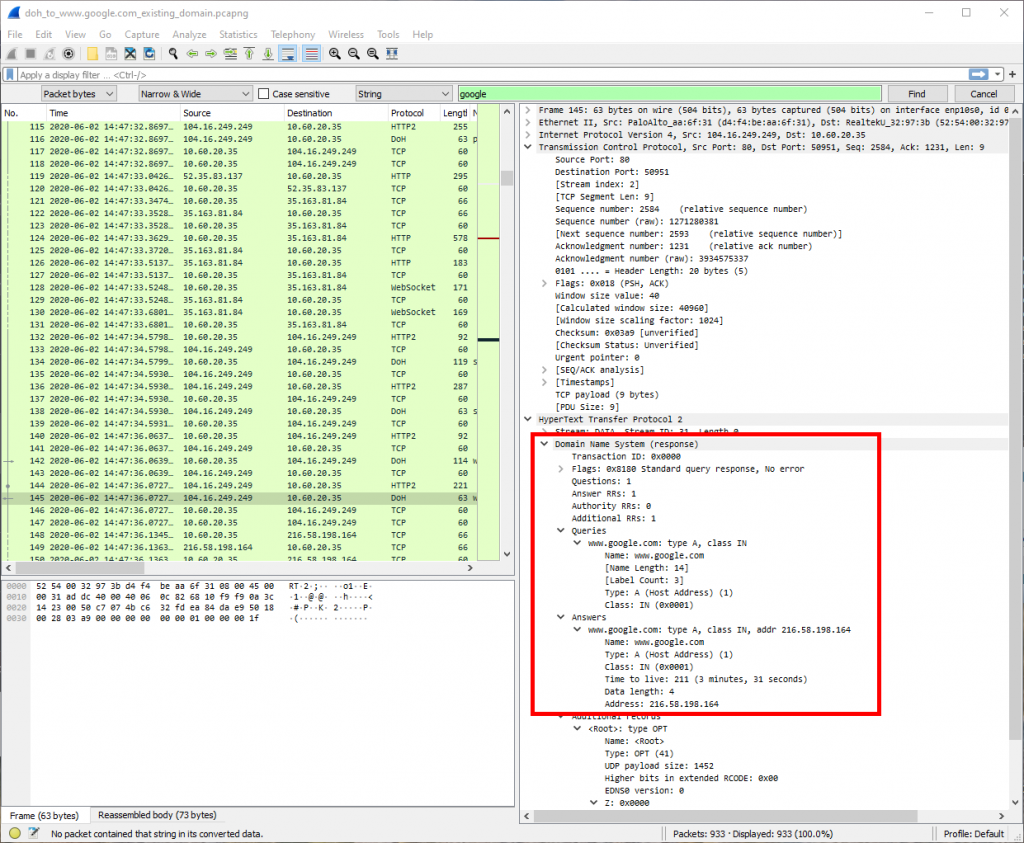
Figure 2 below shows the similarly decrypted HTTP response in packet 145.
Every enterprise needs to have to a serious conversation about network monitoring and what the impact of DoH will be on its security posture. Despite the seismic shift that omnipresent DoH represents, very few organizations have grappled with it and it doesn’t seem to be on the radar of many network admins.
Join the Discussion in the Gigamon Community
We’ve started a special discussion in the Gigamon Community about the DoH situation. Please take a look and share your thoughts.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.