100 Percent Infrastructure Visibility Is More Critical Than Ever in The New Tomorrow
In any major event, changes in how we work and live create a shift on all levels. One shift created by the recent COVID-19 pandemic is remote work and access to business resources like applications and data to continue doing our work. This created an impact on enterprises to enable employees to work remotely in a secure and efficient manner. However, a smooth transition has not been the same across enterprises.
Security Challenges in Working Remotely
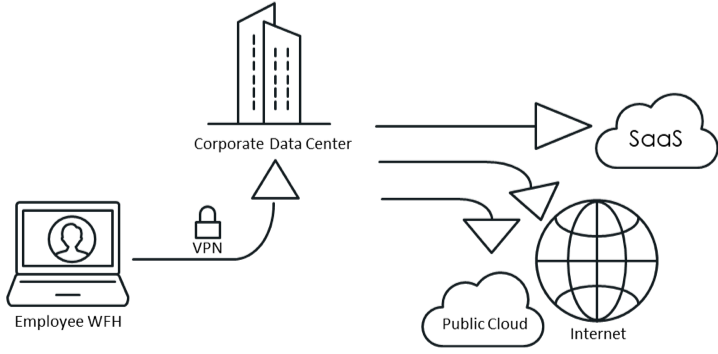
A huge challenge for enterprises is that the work-from-home or anywhere network doesn’t belong to the enterprise itself. In other words, when employees work physically from the office and access on-premises or cloud-based business-critical applications, surf the web, access business and personal emails and download attachments, it’s all done from within the secure walls of the enterprise perimeter network. That allows IT to easily control, secure and monitor traffic that goes in and out of the network. In contrast, in the new era of the COVID-19 pandemic and remote working, IT doesn’t have similar control or visibility.
Remote workers can access the web and download all types of information without a VPN to the corporate data center that would normally provide secure connection and traffic inspection. This traffic pattern shift is not new per se, but it is magnified manyfold in the wake of COVID-19, and thus the huge risk.
Now, business applications running in the data center are at higher risk when remote workers try to access them.

Why 100 Percent Visibility Is More Critical Than Ever
The possibility of a laptop being infected becomes a source of threat to enterprise assets. As the user accesses internal servers, the potential attack surface goes way up.
The article “Hackers Use Java to Hide Malware on the Data Center Network” contends that hacking is becoming more sophisticated and the attack surface is expanding with more employees working at home.
Companies are expanding their remote access solutions (remote desktop protocol servers, virtual network computing servers and commercial remote desktops like Citrix) so quickly that applying basic security hygiene is overlooked, which enables malicious actors to target them.
As a result, attackers who are able to steal employees’ credentials can now access other data center servers via the remote desktop protocol servers that run virtual desktop. Therefore, the need for 100 percent visibility and being able to inspect all traffic, whether encrypted or not, becomes increasingly critical. Without visibility, enterprise networks and assets are at much higher risk.
How the Gigamon Visibility and Analytics Fabric Can Help

The Gigamon Visibility and Analytics Fabric™ (VAF) simplifies connecting security and monitoring tools to be more reliable and efficient in inspecting and monitoring traffic. The VAF supports inline and out-of-band decryption models for all SSL and TLS versions, including the latest TLS 1.3. This enables enterprises to have a flexible and comprehensive visibility and analytics fabric that can adapt to their needs today and in the future. With the ability to decrypt once and feed copies to as many tools as needed to inspect and monitor traffic, the outcome reduces the security stack complexity and enables tools to be more efficient in inspecting traffic, thereby extending each tool’s life.
As a final thought, check out the e-book “Defending the Digital Enterprise,” which highlights seven things you need to improve security in a world dominated by encryption. For example, centralizing decryption, as the NSA Cybersecurity Information recommends in order to inspect all traffic, improves your organization’s Zero Trust posture.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today