Three Oscars-Inspired Lessons in Network Visibility
Updated October 28, 2021.
It’s officially awards season and all the Oscar buzz has us in a movie state of mind. We’re having fun spotting cameos in this year’s crop of Oscar contenders like Ed Sheeran in Star Wars and Dakota Fanning in Once Upon a Time in Hollywood. And it got us thinking that the blink-or-you’ll-miss-them moments from our favorite films are much like the surprise “cameos” NetOps and InfoSec pros contend with from day to day — on the network.
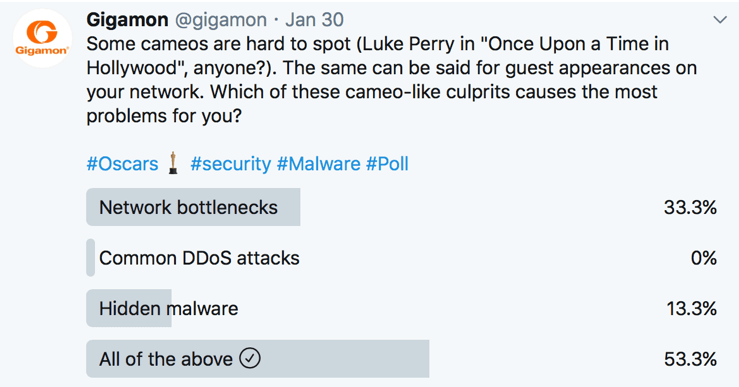
So we took to Twitter with an informal poll asking which of these so-called network cameos are most problematic. The majority of respondents reported that network bottlenecks and hidden malware rank as the top unwanted guest appearances. It’s tough to spot them, especially when organizations today are grappling with the complexities of public, private, and hybrid cloud infrastructure and multitier applications.
Well, we’ve got you covered. Our President and COO Shane Buckley recently channeled his A-list inspiration into a list of tips for dealing with such issues, particularly in context of digital transformation (DX) efforts, when the need is high to effectively spot both application and network-layer cameos.
#1. Hidden Malware
At a pivotal moment in the Oscar-nominated Joker, the evil protagonist studies a tape to prepare for his appearance on a popular TV show. On the tape, he sees a comedian appear on the same show—played by Justin Theroux. It’s a blink-and-you’ll-miss-it cameo from Theroux, very much like hidden malware traversing the network without detection.
Whether they’re sophisticated or non-targeted, high-volume criminally motivated attacks can move throughout the network without your knowledge and cause enterprises significant damage and cost, to the tune of $6 billion by 2021.
Emotet, described by the U.S. Department of Homeland Security as one of the most costly and destructive instances of malware, likely comes to mind as one of the most pertinent examples. It has the ability to move laterally through the organization, spread other damaging malware and constantly evolve.
Spotting hidden malware requires network visibility that spans the entire distributed digital infrastructure, as well as having access to network data to ensure visibility for all security and performance tools. Specifically, organizations need reliable access to data in motion to tap into traffic across cloud and on-premise infrastructure and traffic flowing across 5G and 100GB networks. This type of pervasive visibility allows enterprises to keep up with the speed at which networks and businesses run, as well as with security demands.
#2. Interactions Between Applications or Microservices
When Brad Pitt’s character in Once Upon a Time in Hollywood unknowingly ends up at the Manson Family compound, he comes across Dakota Fanning, who plays a key member of the infamous cult. Their meeting is short but meaningful, and sets the stage for additional character development and exchanges down the line. Interactions between applications or microservices are just as meaningful, with 80 percent of network traffic consisting of such communication on average.
Understanding these interactions is critical for guiding DX efforts, which are a top priority for 87 percent of business leaders. Among the goals of DX are streamlining business processes, cutting costs, improving productivity and introducing new business models that redefine industries — or build new ones.
These are ambitious goals, and they’re ultimately realized through new digital applications built on intricate microservices-based architectures that need to be managed and secured.
Only with a clear view, and the right kind of data, can you understand the applications’ interactions, performance and security characteristics, in order to accelerate DX. And the only way to get to this view is to look at the data in motion on the network.
The ability to isolate specific applications or microservices communication streams for deeper inspection allows InfoSec teams to easily understand access patterns and put in place effective micro segmentation strategies. Application developers too can benefit from this by better understanding communication bottlenecks between applications and microservices, as well as troubleshoot them.
#3. Traffic Bottlenecks
The latest rendition of Little Women follows a non-linear storytelling structure, constantly jumping between two timelines. It can be jarring to viewers when the girls’ father returns from war, revealing himself as the actor Bob Odenkirk. While this moment is meant to be an intimate glimpse into a family coming together after a long separation, it brings the movie-watching experience to a standstill, since the audience associates Bob Odenkirk less with a serious scene and more with his previous comedic roles.
Networks today are similarly prone to experiencing abrupt slowdowns or bottlenecks that limit network performance and waste bandwidth. Managing the network to ensure constant availability is a major challenge when data volumes are growing exponentially. It’s estimated that about 1.7 megabytes of new information will be created every second for every human being on the planet this year. This data explosion paired with DX technology investments and lightning fast 5G and 100GB has led to a very complex enterprise infrastructure setup — and network blind spots across physical, virtual and cloud environments.
The solution lies in having the right kind of data to help you understand network and application performance. By analyzing the network traffic, you get immediate actionable data points that can be used to address trouble spots.
Whether we’re talking big screen or enterprise
network, surprise cameos are common and they are easy to miss — and this is
particularly problematic when things like malware and bottlenecks pose a threat
to network security and speed. For the NetOps
and InfoSec pros tasked with complex infrastructure development,
implementation, maintenance and security, you need a clear line of sight
into what’s happening within the network.
Armed with insights on traffic patterns (both cloud and on-premise), delays in data flow and insecure areas, you can use this intel to write the screenplay (or plan) to support a robust and secure digital infrastructure.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today