Gigamon Raises the Network Visibility Bar to New Heights with GigaVUE-OS 5.8
With the holidays almost upon us, the latest GigaVUE-OS, GigaVUE-FM and GigaVUE® Cloud Suite software releases are now available. Read on for details about how this version will help you maximize visibility for your networking, security, cloud and scalability requirements in a world of rapid digital transformation.
The Gigamon 5.8 release brings a broad array of powerful capabilities to further optimize and simplify your networking and security operations. Here’s what’s in it for you:
- Diminish traffic processing burdens to offload overworked tools
- Improve user experience and productivity while lowering help desk expenses
- Control resource access for enhanced security
- Securely transmit encapsulated traffic from remote sites at line rates
- Automatically discover monitoring and security tools on the network
- Increase SSL/TLS performance by over 30 percent
Advanced Flow Slicing
Gigamon next-gen network packet brokers with the GigaSMART® engine have offered Packet Slicing for years. This feature truncates packets while preserving the portion of the packet (the protocol headers) required for network analysis.
Now we introduce Advanced Flow Slicing to intelligently slice or truncate content within flows. Select and fully analyze a pre-configurable number of initial packets in a flow (HTTP session or any general TCP/UDP session) and drop all subsequent packets or remove specific payload data from each subsequent packet.
Benefits:
- Reduces traffic sent to tools by more than 60 percent
- Avoids costly tool upgrades to inspect unnecessary traffic
- Improves overall tool efficiency and effectiveness
- Retains complete visibility into each flow’s establishment
This capability is supported on GigaSMART modules for:
- GigaVUE-HC1
- GigaVUE-HC2
- GigaVUE-HC3
Fabric Manager Administration Enhancements
GigaVUE-FM provides intuitive single-pane-of-glass centralized orchestration and management of Gigamon visibility nodes. FM monitors all the physical and virtual nodes across your on-premises, virtual and public cloud deployments. This solution offers simplified workflows for traffic policy configuration, end-to-end topology visualization, hierarchical grouping based on location and customizable dashboards.
Single Sign-On with SAML 2.0
Now FM supports single sign-on (SSO) which allows you to access multiple applications with a single set of login credentials. Integrated authentication facilitates easier user sign-on and improved security policing. GigaVUE-FM provides the following SSO options:
- Internal Identity Provider (IdP): GigaVUE-FM uses Shibboleth 2.0 (which builds on SAML 2.0) as the IdP for authentication and authorization. When a user accesses GigaVUE-FM, the IdP’s login URL appears, prompting the user’s login credentials. The internal IdP reads the AAA settings configured in GigaVUE-FM to authenticate the login. Upon authorization, the user is redirected to the GigaVUE-FM Dashboard.
- External IdP: Microsoft ADFS and Okta are qualified as external IdPs for GigaVUE-FM.
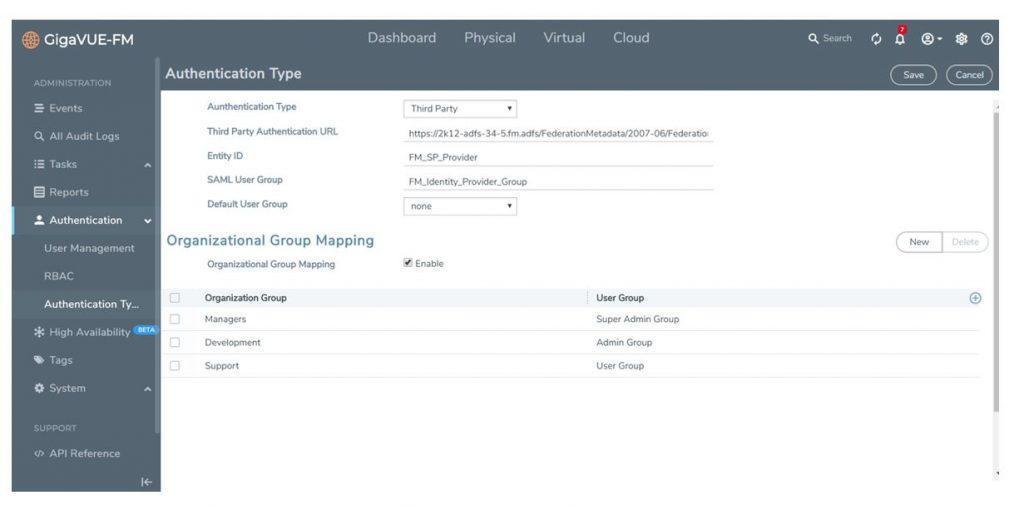
You may configure how user logins are authenticated using the Authentication Type screen within GigaVUE-FM. FM can authenticate users via a local user database or through the configurations in an external authentication server (LDAP, RADIUS or TACACS+) or even by Microsoft ADFS.
Expanded Role-Based Access Control (RBAC)
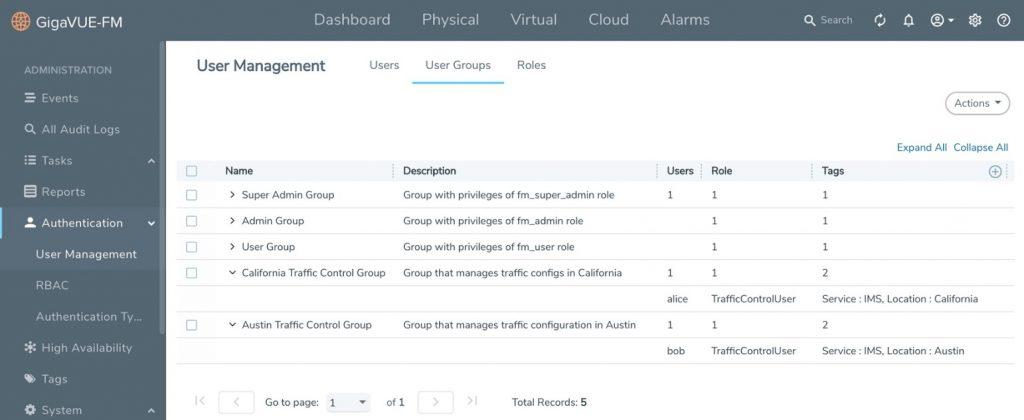
Added RBAC functionality in GigaVUE-FM enables highly granular role definitions for user profiles and privileges, which provides more specific user control over Create, Read, Update and Delete operations. This involves:
- Tags: Tags are used to identify resources. Access Control tags are used to filter the resources that a user can access. Users can access a resource if the tags configured for their group match the tags present on the resource. Filtering can be based on clusters, ports, port groups, GigaSMART groups, GigaStream®, Port-Pair and maps. The resources in GigaVUE-FM are associated to tag IDs and their associated values. Every user in the system is also associated with a set of tag IDs and their associated values.
- User Groups: This is a collection of one or more roles where the role defines the kind of resource and the action that can be performed by a user (for example, read access or read/write access to map information). The User Group option helps to associate the users with roles and tags.
GigaVUE-FM Alarm Management
A variety of alarm management capabilities involving thresholds, correlations and filtering improve root cause analysis for accelerated troubleshooting and remediation. Specific features in GigaVUE-FM include the following:
- Alarm Correlation: Correlate alarms generated due to simultaneous network or resource faults to prevent alarm flooding
- Bulk acknowledgment of alarms
- Delete or de-acknowledge alarms
- Port utilization-based alarms (upper and lower threshold-based)
- Threshold values for memory and CPU status
- Percentage based traffic threshold alarms for packet drops and errors
- Exclude resources from health computation and alarm generation
What’s New in Traffic Handling
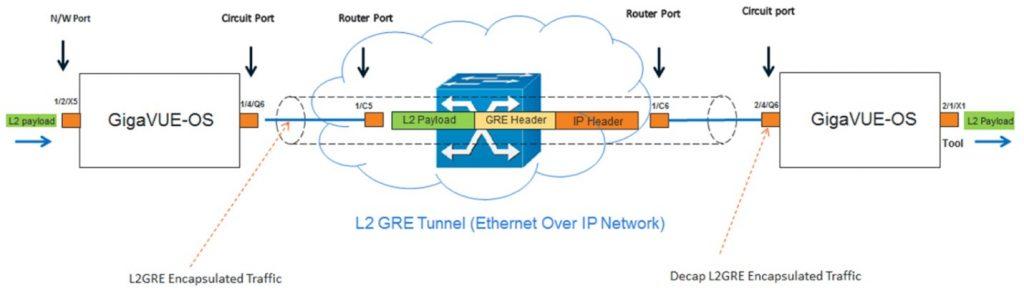
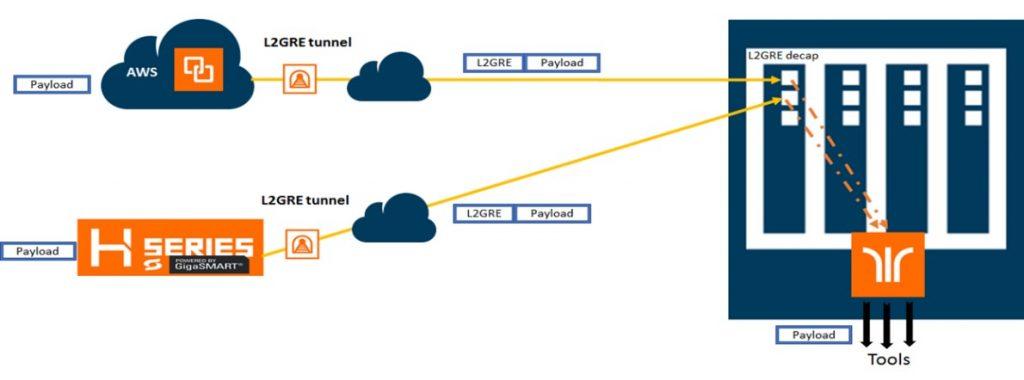
L2GRE and VXLAN Tunnel Encapsulation on TA and HC Platforms
In Gigamon deployments, most or all of the Visibility Fabric™ coexists at a specific location. But there are many scenarios where you may have geographically dispersed offices and need to acquire traffic at remote sites such as power stations or retail outlets. In turn, this traffic must be encapsulated and transmitted across a LAN or WAN to a central office where the security and network monitoring tools are present. In turn, the data is aggregated, decapsulated and processed by a central Gigamon visibility node and sent to the tools for further analysis.
GigaVUE-OS now supports both tunnel initiation and termination for L2GRE and VXLAN encapsulation without GigaSMART cards on most TA Series and HC Series devices. Tunneling is essential to support backhauling from remote sites and forwarding to cloud-based tools. Organizations can now tunnel at line rates more cost-effectively by leveraging the appropriate appliance, and tunneling is supported across node clusters. Visibility nodes supported include:
- GigaVUE-TA40
- GigaVUE-TA100
- GigaVUE-TA200
- GigaVUE-HC1
- GigaVUE-HC2 (CCv2 only)
- GigaVUE-HC3
Provisioning and Auto Device Discovery
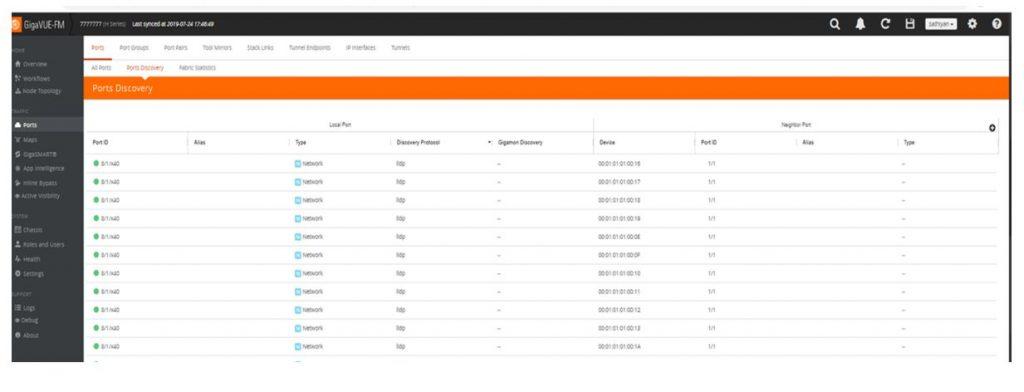
Organizations would like to automatically discover security and network monitoring tools that are connected to Gigamon Visibility Fabric nodes or any network devices connected to management ports of Gigamon Visibility Fabric nodes.
With 5.8, not only can you leverage discovery protocols for network ports, but these protocols are enabled on our tool and circuit ports as well. Further, these protocols are supported on the Gigamon management interface, too. These enhancements allow IT to visualize the connected tools. This simplifies and automates overall network administration functions.
Specifically, Gigamon adds Link Layer Discovery Protocol (LLDP) and Cisco Discovery Protocol (CDP) support for tools that can send these packets.
- LLDP/CDP capability on the tool port
enables verification of connectivity and reachability of utility tools
connected to egress ports and is supported by:
- GigaVUE-TA10
- GigaVUE-TA40
- GigaVUE-TA100
- GigaVUE-TA200
- GigaVUE-HC1
- GigaVUE-HC2
- GigaVUE-HC3
- LLDP/CDP capability on the management port enables verification of connectivity and reachability of tools/devices via the uplink switches and is supported by GigaVUE-HC3
Similarly, IT can now identify which Gigamon nodes are on the network. Management ports of Gigamon visibility nodes provide gratuitous ARPs to announce their presence so that network devices can detect them. This is supported by:
- GigaVUE-HC1
- GigaVUE-HC2
- GigaVUE-HC3
Improvements to In-Line and Passive SSL/TLS Processing
In-line Encryption
Heading the list for in-line advancements is a 30 percent increase in SSL performance. With most traffic now encrypted, this increases throughput and cost-effectiveness.
Improved usability has also been added through SSL certificate management enhancements:
- Additional fields for viewing and filtering certificates
- Health status indicator
- Configurable options to auto-enable or auto-delete certificates
- Certificate statistics page displays certificate usage counters and expiration dates
For inbound deployments, you can now utilize transparent forwarding of server certificate chains. Up to now for these environments, keymap configurations requires both the private key and complete server certificate chain to be configured. The uploaded server certificate chain is then validated. During the SSL handshake, this configured server certificate chain gets sent to the SSL client. An incomplete server certificate chain configuration results in connection failures and can be difficult to troubleshoot.
To overcome this limitation, during the inbound keymap configuration phase, the server certificate chain trust is not validated. During the SSL handshake, once the server keymap is matched, the original server certificate chain received from the server is passed to client.
Passive SSL: DSSL Certificate/Private-Key Mapping
For out-of-band SSL traffic decryption, a server’s private key must be known. Typically, this key is uniquely identified by the server’s IP and port number. However, the server IP may change such that it will not match the configured server IP provided to the Gigamon visibility node and that server’s traffic cannot be decrypted. To further complicate matters, servers can have multiple private-key/certificate pairs and these cannot be stored with the same IP.
To overcome these limitations and obviate the need for the server IP/port Gigamon’s visibility node can match the certificate of the server, instead of the server IP and private key. The server’s certificate can be obtained during the SSL handshake. Our platform evaluates the certificates stored in the KeyStore to compare with the incoming server certificate; if there is a match our node will fetch the corresponding private-key from KeyStore and then decrypt the corresponding sessions.
Our visibility nodes will also continue to support the legacy server IP to private key service mapping approach. IT may configure both methods and if none of the existing configured server IP matches with the session’s IP, only then will the SSL handshake will be used for certificate matching.
These SSL/TLS decryption enhancements are supported on GigaSMART modules of:
- GigaVUE-HC1
- GigaVUE-HC2
- GigaVUE-HC3
Private Cloud Solutions
With 5.8 Gigamon has taking a quantum leap forward in this arena. Stay tuned for more details in the New Year! Can’t wait that long and want to know more now? Contact Gigamon today.
Learn More
Sign up for a free trial to see what Gigamon’s Visibility and Analytics Fabric with the latest 5.8 release can do for you. Be sure to check out the Advanced Flow Slicing web page to learn more how to chop out unnecessary packet baggage.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Networking group.
Share your thoughts today